Web Security Vulnerabilities - Insecure Direct Object Reference (IDOR)
What is IDOR?
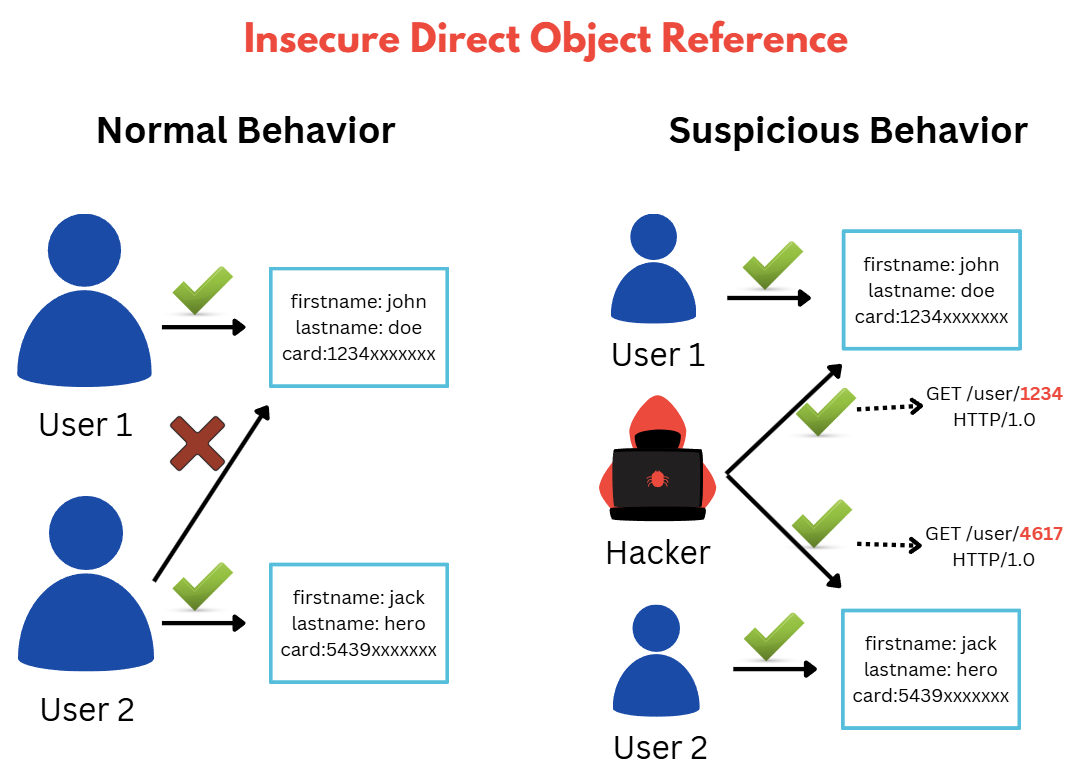
Insecure Direct Object Reference, also known as IDOR, is a type of access control vulnerability that occurs when an application uses user input to access objects such as data or files directly. This can allow attackers to manipulate the input and access unauthorized information, potentially leaking sensitive data.
Example:
Assume an application allows users to access their profiles using the following URL:
http://example.com/users/?userID=4
If the application doesn’t properly check if the user has access to view the profile information before displaying it, an attacker can change the userID to access another user’s data:
http://example.com/users/?userID=1
If the website does not properly validate the user’s access rights, the attacker can access the profile information of another user (user with ID 1 in this case) without being authorized to do so. This is an example of an Insecure Direct Object Reference vulnerability.
What is the impact of IDOR?
The impact of an IDOR vulnerability depends on the application’s data. Some potential impacts of IDOR include:
- unauthorized access to user’s data
- chaining IDOR to account takeover
- Attackers may modify or delete data, leading to loss of data integrity and reliability.
Where to find IDOR?
To find IDOR vulnerabilities, there are some places to search for:
-
Numeric Identifiers
Applications uses numeric identifiers to access resources or specific data. So, attackers try to manipulate these numbers to access unauthorized data or resources.
Example:
GET /profile/user/1234 HTTP/1.0 --> GET /profile/user/1235 HTTP/1.0 -
Username Manipulation
Some applications use username to access profile data or any sensitive data related to specific user, So attackers try to change username to access other’s data.
Example:
GET /profile/?username=jack HTTP/1.0 --> GET /profile/?username=john HTTP/1.0 -
Resource Path Manipulation
Suppose an application uses the following URL to access some data:
GET /files/?file=home.phpAttackers manipulate the
fileparameter trying to access sensitive dataGET /files/?file=secret.php -
POST Request Parameters
Attackers here try to manipulate
POSTrequest parameters (e.g. change user ID, ) to modify or access sensitive/unauthorized data.Example:
POST /profile/edit HTTP/1.0 HOST: example.com ... username=john123&firstname=john&lastname=doeAfter manipulation
POST /profile/edit HTTP/1.0 HOST: example.com ... username=jack432&firstname=john&lastname=doe -
Cookie-based
Suppose an application uses cookies to identify and authorize users to access specific data, here attackers try to change value of cookie to access unauthorized data.
Example:
GET /profile HTTP/1.0 Cookie: user_id=1234After manipulation
GET /profile HTTP/1.0 Cookie: user_id=1235 -
API (Application Programming Interface)
API can be vulnerable to IDOR if it leaks sensitive data.
Example:
GET /api/v1/messages HTTP/1.0 --> GET /api/v2/messages HTTP/1.0 GET /api/v1/users/1 HTTP/1.0 --> GET /api/v1/users/2 HTTP/1.0
Some IDOR Bypasses
-
Change file type
GET /user_data/1234 ---> 401 GET /user_data/1234.json ---> 200 GET /user_data/1234.xml ---> 200 GET /user_data/1234.config ---> 200 GET /user_data/1234.txt ---> 200 -
Send wildcard (
*)GET /api/v1/users/user_id ---> GET /api/users/* HTTP/1.1 -
Change ID to username
GET /api/v1/users/1234 HTTP/1.0 ---> GET /api/v1/users/jack HTTP/1.0 -
Swap UUIDs with numbers
GET /file?id=90ri2-xozifke-29ikedaw0d HTTP/1.1 Host: example.com ... Try this to bypass GET /file?id=1234 Host: example.com ... -
Analyze JS files for leaked IDs
POST /api/v1/users/ HTTP/1.0 user_id=1234&user_id=1235 -
Analyze JS files for leaked IDs
How to prevent IDOR?
To prevent Insecure Direct Object Reference (IDOR) vulnerabilities, consider implementing the following measures:
-
Use Indirect Object References & Unique Identifiers
Instead of using direct object references, use indirect references that are mapped to the actual objects on the server side. This way, even if the user manipulates the reference, they cannot access unauthorized data.
Example:
Instead of
https://www.example.com/users/?userID=36, usehttps://www.example.com/users/?userID=ffc61035-b579-44e0-b7fc-199bb005cdde. -
Validate User Input
Always validate and sanitize user input to prevent malicious input that could be used to manipulate object references.
Time to practice
Now let’s practice what we’ve learned and see how we can find IDOR in a real-world scenario.
Challenge #1
Goal: Access sensitive data.
Login Credentials:
Username: Jack
Password: password123
We can see login page and the challenge provide us with the credentials, so let’s login and check the website.

After logging in, we will be presented with a dashboard that has three functionalities: View Profile, Edit Profile, and Logout.
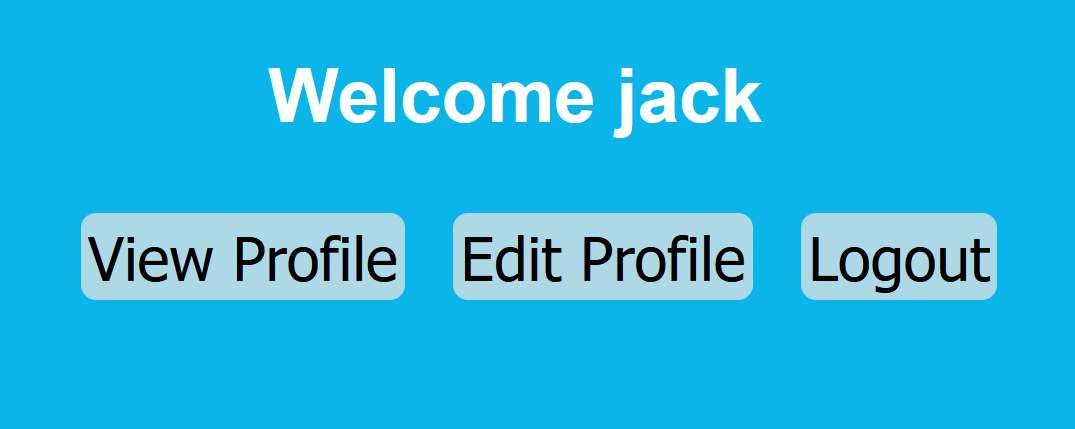
On the View Profile page, we can see Jack’s sensitive information, such as his card number. Take note of how this data is presented.

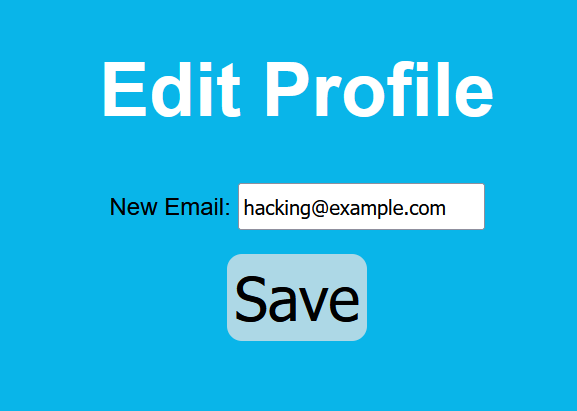
Next, navigate to the Edit Profile page where we can change Jack’s email address. Try changing it to hacking@example.com and observe what happens.

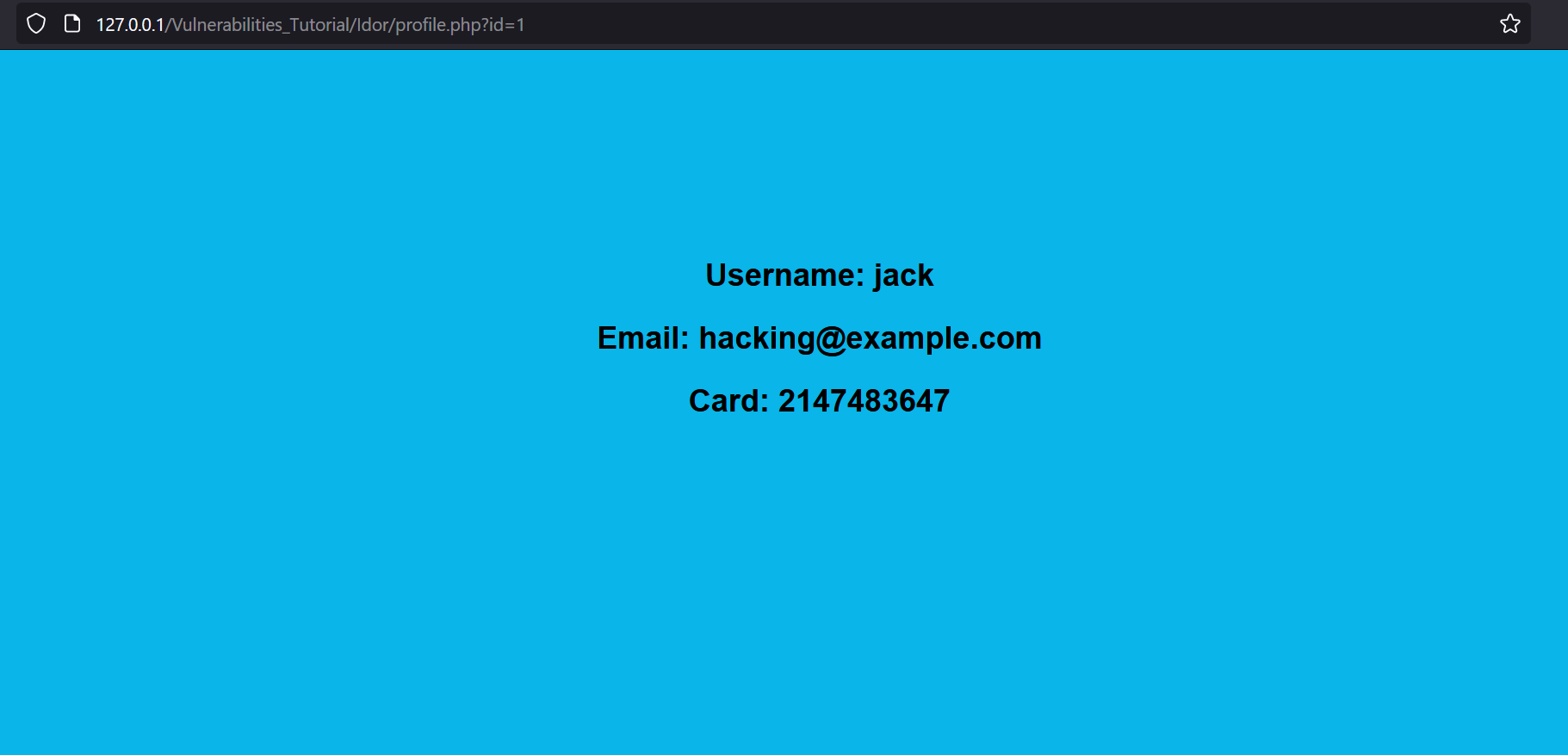
Notice the id parameter in the URL. Attempt to change the id from 1 to 2 and observe if we can access another user’s profile.
As we can see, changing the id allows us to access Bob’s profile, which is an IDOR vulnerability.
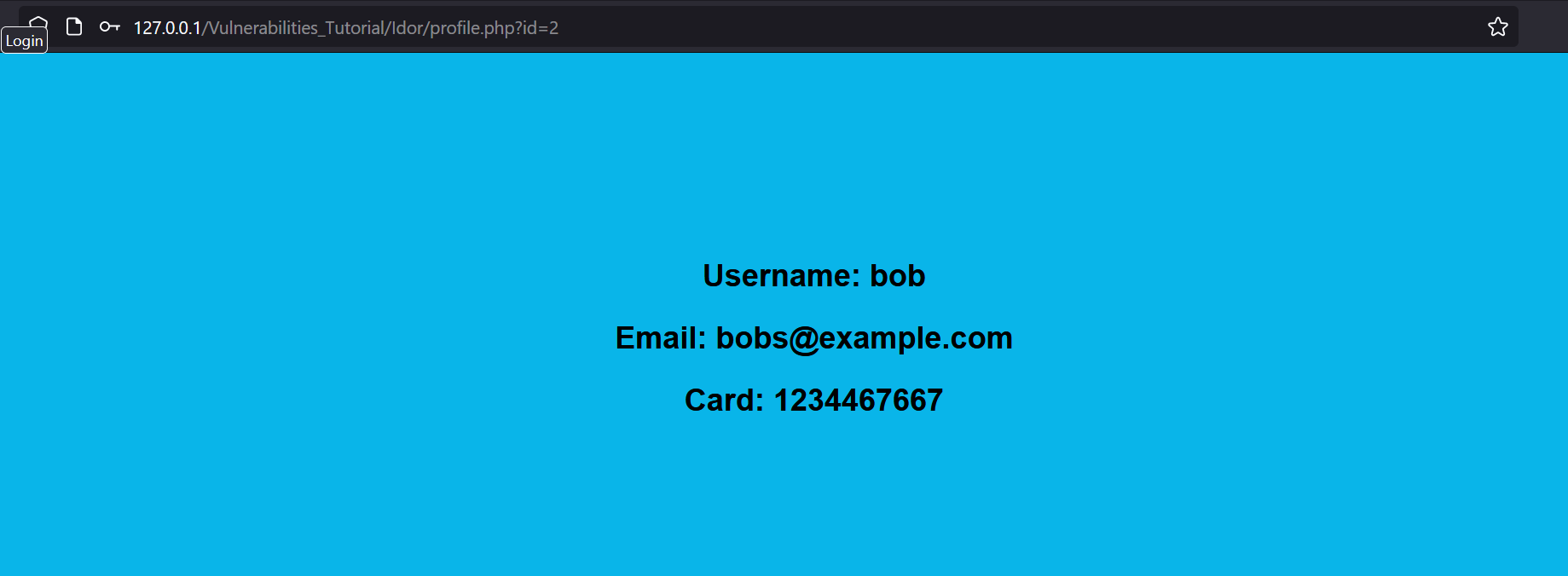
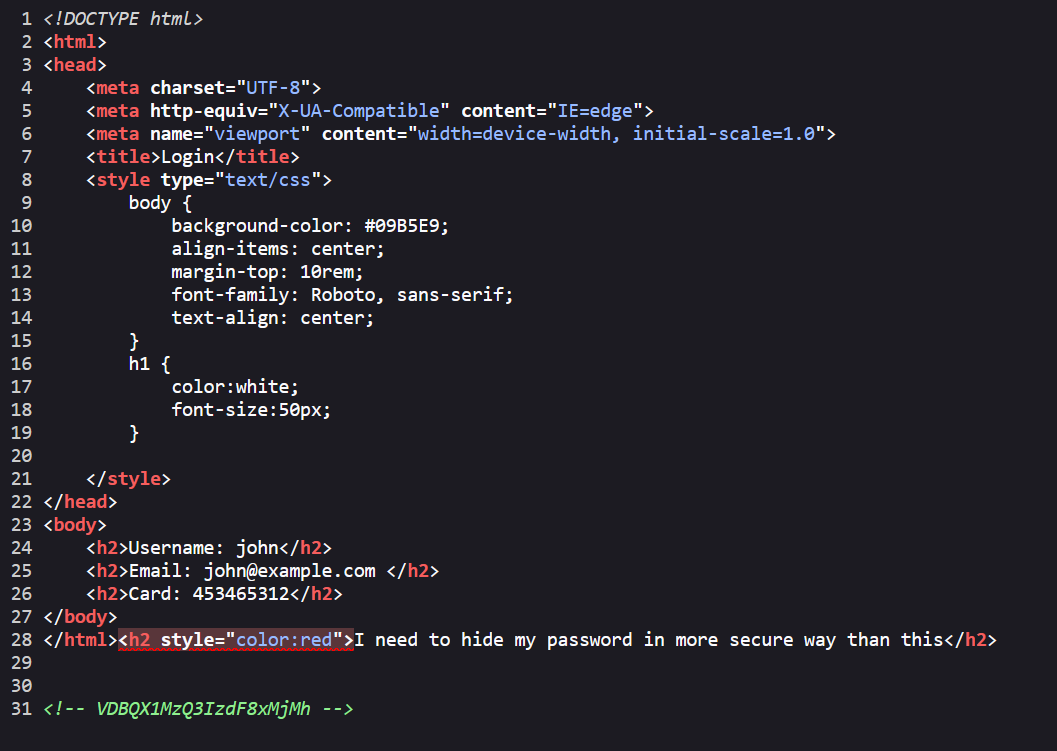
Let’s try changing the id to 3 to see if we can access another user’s profile. In John’s profile, we might notice a message indicating a leaked password.

View the page’s source code, and we can find a base64 encoded string.
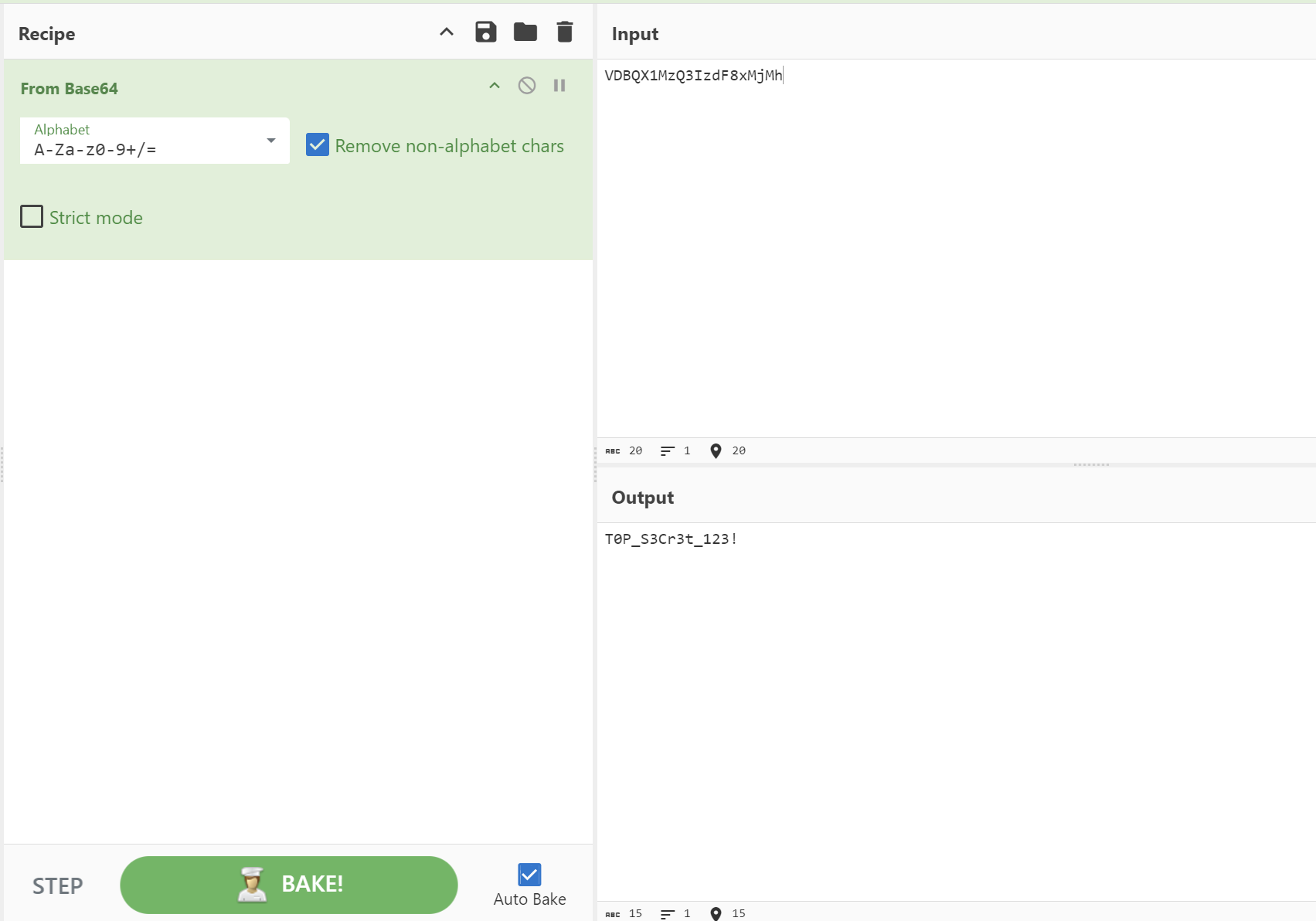
So let’s decrypt it using CyberChef and get the password of john.
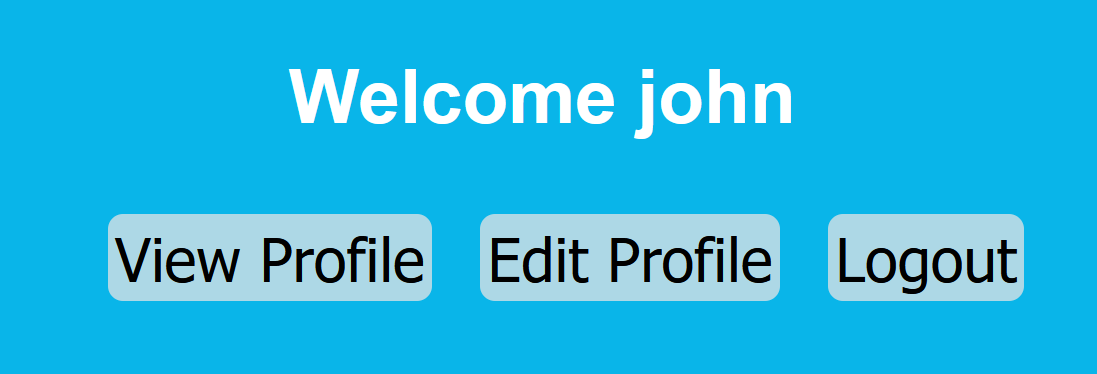
Now, we can login to John account and access the profile.
Resources
Conclusion
In summary, Insecure Direct Object References (IDOR) expose web applications to severe risks. It’s essential to implement strong access controls and validate user permissions to prevent such vulnerabilities.
Hope you enjoy this guide! Thanks for reading.